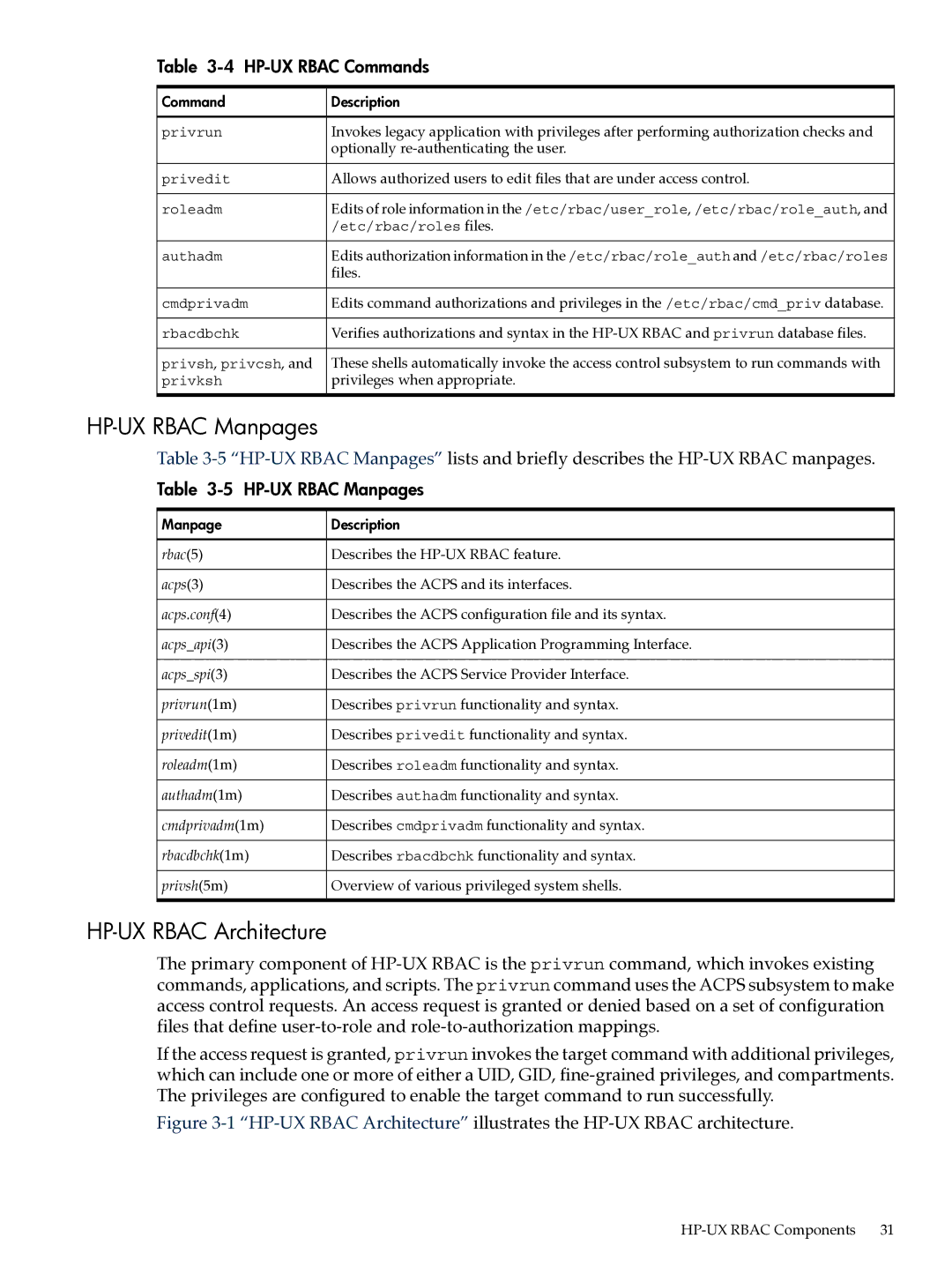
Table 3-4 HP-UX RBAC Commands
Command | Description |
privrun | Invokes legacy application with privileges after performing authorization checks and |
| optionally |
privedit | Allows authorized users to edit files that are under access control. |
roleadm | Edits of role information in the /etc/rbac/user_role, /etc/rbac/role_auth, and |
| /etc/rbac/roles files. |
authadm | Edits authorization information in the /etc/rbac/role_auth and /etc/rbac/roles |
| files. |
cmdprivadm | Edits command authorizations and privileges in the /etc/rbac/cmd_priv database. |
rbacdbchk | Verifies authorizations and syntax in the |
privsh, privcsh, and | These shells automatically invoke the access control subsystem to run commands with |
privksh | privileges when appropriate. |
HP-UX RBAC Manpages
Table
Table 3-5 HP-UX RBAC Manpages
Manpage | Description |
rbac(5) | Describes the |
acps(3) | Describes the ACPS and its interfaces. |
acps.conf(4) | Describes the ACPS configuration file and its syntax. |
acps_api(3) | Describes the ACPS Application Programming Interface. |
acps_spi(3) | Describes the ACPS Service Provider Interface. |
privrun(1m) | Describes privrun functionality and syntax. |
privedit(1m) | Describes privedit functionality and syntax. |
roleadm(1m) | Describes roleadm functionality and syntax. |
authadm(1m) | Describes authadm functionality and syntax. |
cmdprivadm(1m) | Describes cmdprivadm functionality and syntax. |
rbacdbchk(1m) | Describes rbacdbchk functionality and syntax. |
privsh(5m) | Overview of various privileged system shells. |
HP-UX RBAC Architecture
The primary component of
If the access request is granted, privrun invokes the target command with additional privileges, which can include one or more of either a UID, GID,