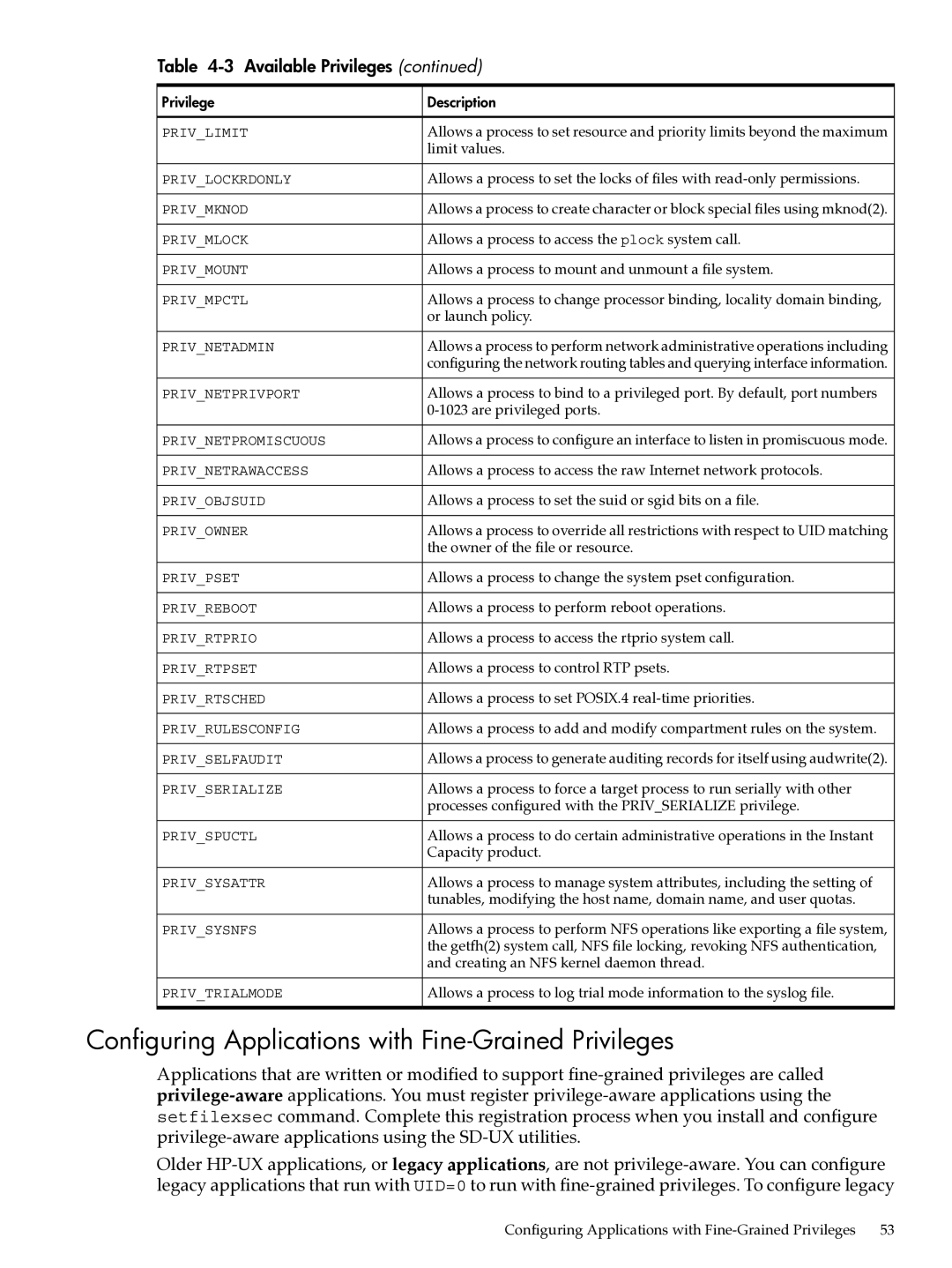
Table 4-3 Available Privileges (continued)
Privilege | Description |
PRIV_LIMIT | Allows a process to set resource and priority limits beyond the maximum |
| limit values. |
PRIV_LOCKRDONLY | Allows a process to set the locks of files with |
PRIV_MKNOD | Allows a process to create character or block special files using mknod(2). |
PRIV_MLOCK | Allows a process to access the plock system call. |
PRIV_MOUNT | Allows a process to mount and unmount a file system. |
PRIV_MPCTL | Allows a process to change processor binding, locality domain binding, |
| or launch policy. |
PRIV_NETADMIN | Allows a process to perform network administrative operations including |
| configuring the network routing tables and querying interface information. |
PRIV_NETPRIVPORT | Allows a process to bind to a privileged port. By default, port numbers |
|
|
PRIV_NETPROMISCUOUS | Allows a process to configure an interface to listen in promiscuous mode. |
PRIV_NETRAWACCESS | Allows a process to access the raw Internet network protocols. |
PRIV_OBJSUID | Allows a process to set the suid or sgid bits on a file. |
PRIV_OWNER | Allows a process to override all restrictions with respect to UID matching |
| the owner of the file or resource. |
PRIV_PSET | Allows a process to change the system pset configuration. |
PRIV_REBOOT | Allows a process to perform reboot operations. |
PRIV_RTPRIO | Allows a process to access the rtprio system call. |
PRIV_RTPSET | Allows a process to control RTP psets. |
PRIV_RTSCHED | Allows a process to set POSIX.4 |
PRIV_RULESCONFIG | Allows a process to add and modify compartment rules on the system. |
PRIV_SELFAUDIT | Allows a process to generate auditing records for itself using audwrite(2). |
PRIV_SERIALIZE | Allows a process to force a target process to run serially with other |
| processes configured with the PRIV_SERIALIZE privilege. |
PRIV_SPUCTL | Allows a process to do certain administrative operations in the Instant |
| Capacity product. |
PRIV_SYSATTR | Allows a process to manage system attributes, including the setting of |
| tunables, modifying the host name, domain name, and user quotas. |
PRIV_SYSNFS | Allows a process to perform NFS operations like exporting a file system, |
| the getfh(2) system call, NFS file locking, revoking NFS authentication, |
| and creating an NFS kernel daemon thread. |
PRIV_TRIALMODE | Allows a process to log trial mode information to the syslog file. |
Configuring Applications with Fine-Grained Privileges
Applications that are written or modified to support
Older
Configuring Applications with | 53 |