Commands
Table
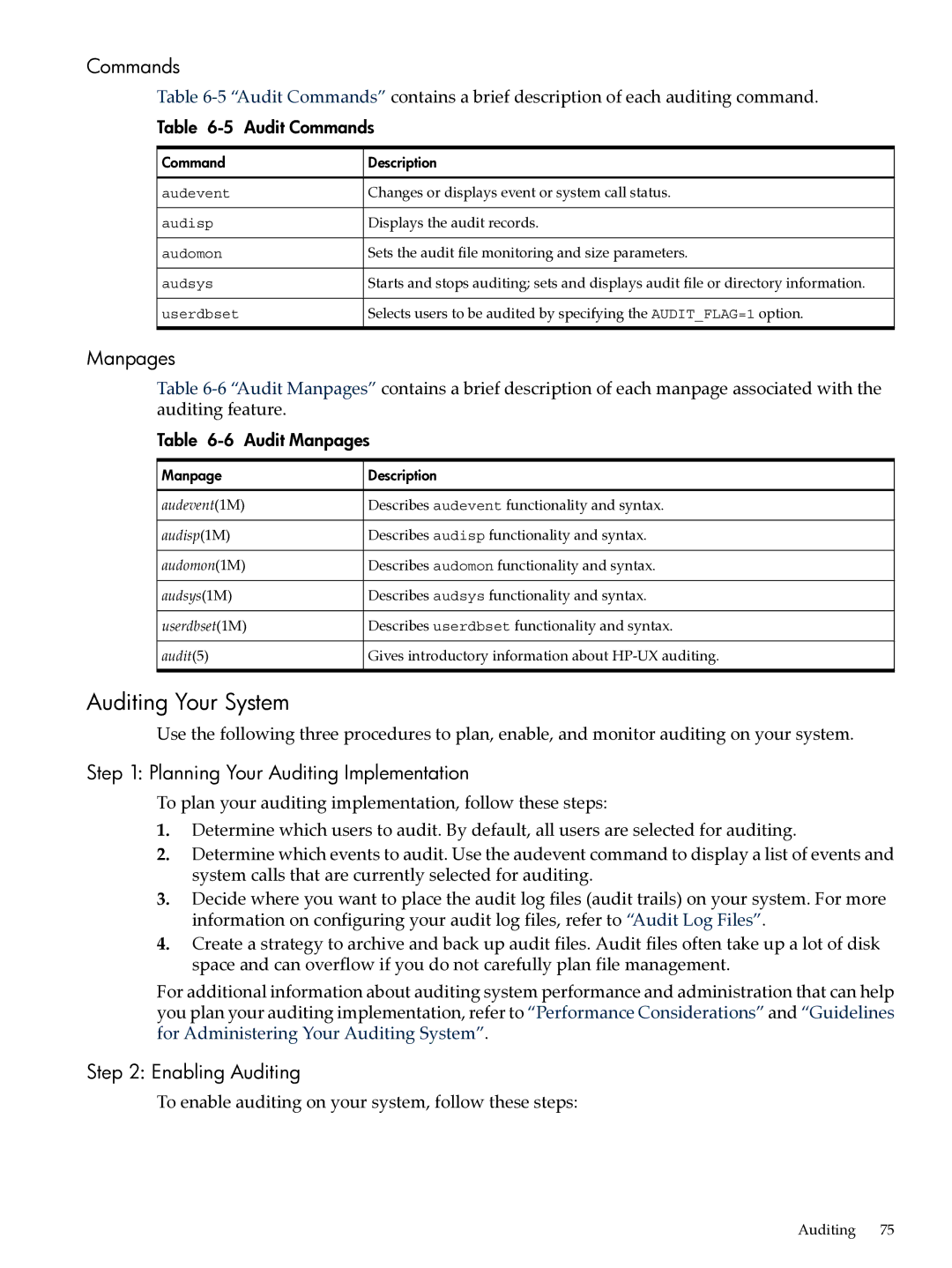
Table 6-5 Audit Commands
Command | Description |
audevent | Changes or displays event or system call status. |
audisp | Displays the audit records. |
audomon | Sets the audit file monitoring and size parameters. |
audsys | Starts and stops auditing; sets and displays audit file or directory information. |
userdbset | Selects users to be audited by specifying the AUDIT_FLAG=1 option. |
Manpages
Table
Table 6-6 Audit Manpages
Manpage | Description |
audevent(1M) | Describes audevent functionality and syntax. |
audisp(1M) | Describes audisp functionality and syntax. |
audomon(1M) | Describes audomon functionality and syntax. |
audsys(1M) | Describes audsys functionality and syntax. |
userdbset(1M) | Describes userdbset functionality and syntax. |
audit(5) | Gives introductory information about |
Auditing Your System
Use the following three procedures to plan, enable, and monitor auditing on your system.
Step 1: Planning Your Auditing Implementation
To plan your auditing implementation, follow these steps:
1.Determine which users to audit. By default, all users are selected for auditing.
2.Determine which events to audit. Use the audevent command to display a list of events and system calls that are currently selected for auditing.
3.Decide where you want to place the audit log files (audit trails) on your system. For more information on configuring your audit log files, refer to “Audit Log Files”.
4.Create a strategy to archive and back up audit files. Audit files often take up a lot of disk space and can overflow if you do not carefully plan file management.
For additional information about auditing system performance and administration that can help you plan your auditing implementation, refer to “Performance Considerations” and “Guidelines for Administering Your Auditing System”.
Step 2: Enabling Auditing
To enable auditing on your system, follow these steps:
Auditing 75