Huawei
V200R001
Manual Version T2-080168-20011213-C-1.5
BOM31010868
Contents
About This Manual
Key 1 + Key
Format Description Key
Bracket, e.g. Enter , Tab , Backspace , or a
Key 1, Key
Symbol
Action Description
Security Configuration SC
Huawei
Configuration of IKE
II. IKE features
IKE Configuration Task List
Creating IKE Security Policy
Select Encryption Algorithm
Select Authentication Algorithm
No IKE security policy is created by default
Select DH Group ID
Set Pre-shared Key
Select Hashing Algorithm
Set Lifetime of IKE Association SA
Show IKE SA parameter Quidway# show crypto ike sa
Networking requirements
Show IKE security policy Quidway# show crypto ike policy
II. Networking diagram
III. Configuration procedure
Problem 1 Invalid user ID information
VPN Configuration VPN
Table of Contents
VPN features
VPN Overview
According to operation mode
Classification of IP VPN
II. According to the layer where the tunnel is
III. According to service purpose
IV. According to networking model
Overview of Vpdn
Configuration of L2TP
Brief Introduction to L2TP Protocol
Brief induction to Vpdn
Tunnel and session
2 L2TP Protocol
III. Method to realize Vpdn
II. Control message and data message
III. Two typical L2TP tunnel modes
IV. Call setup flow of L2TP tunnel
Call setup flow of L2TP channel is shown in the following
Features of L2TP protocol
Figure VPN-2-3Call setup flow of L2TP channel
Configuring at LAC Side
Configuring L2TP
1 L2TP Configuration Task List
Disable Vpdn to run by default
II. Create Vpdn group
IV. Set the connection request to originate L2TP channel
Configuring at LNS Side
Disable Vpdn running by default
Table VPN-2-4L2TP attribute table
Accept dialin l2tp virtual-template virtual
III. Create/delete virtual interface template
No vpdn group group-number
No accept dialin
Set local name of channel
Optional configuration
III. Force local end to perform Chap authentication
IV. LNS forces LCP to renegotiate
Local end does not perform Chap authentication by default
LCP does not renegotiate by default
Set domain name delimiter and search sequence
VII. Enable/disable hiding AV pairs
Disable hiding AV pairs by default
Monitoring and Maintenance of L2TP
VIII. Force to disconnect tunnel
NAS-Initialized VPN
Typical Configuration of L2TP
Show l2tp session command domain
Networking requirement
III. Configuration procedure
Figure VPN-2-5Networking diagram of Client-Initialized VPN
Client-Initialized VPN
Single User Interconnects Headquarters via Router
Chapter
Fault Diagnosis of L2TP
Brief introduction to the protocol
Configuration of GRE
Brief Introduction to GRE Protocol
II. Applicable range
Figure VPN-3-2Format of transmission message in the tunnel
Configuring GRE
GRE Configuration Task List
Creating Virtual Tunnel Interface
Setting the Source Address of Tunnel Interface
Setting the Destination Address of Tunnel Interface
Setting the Identification Key Word of Tunnel Interface
Setting the Network Address of Tunnel Interface
Setting the Encapsulation Mode of Tunnel Interface Message
Setting Tunnel Interface to Check with Check Sum
Show interface tunnel tunnel-number
Monitoring and Maintenance of GRE
Disable tunnel interface to check with check sum by default
Typical Configuration of GRE
Figure VPN-3-6Networking diagram of GRE application
Chapter
Troubleshooting GRE
Reliability Configuration LC
Configuration of Backup Center
Configuration of Hsrp
Configuring the Backup Center
Configuration of Backup Center
Backup Center Overview
Configuration Task List
Backup logic-channel logic-channel
No backup delay
Backup state-up interval-time
Configuring Routes for Main and Backup Interfaces
Backup state-down number
An example of Backup Between Interfaces
Monitoring and Maintaining of Backup Center
Typical Configuration of Backup Center
An Example of Multiple Backup Interfaces
Chapter
Chapter
Configuration of Hsrp
Hsrp Overview
Configuring Hsrp
Starting Hsrp Function
Setting Hsrp Authorization Word
Setting Router’s Priority in Hsrp Hot Standby Group
Setting Router’s Preemption Mode in Hsrp Standby Group
Standby group-number preempt
Standby group-numberauthentication string
Setting Hsrp Timer
Table LC-2-4Set Hsrp authorization word
Monitoring the Specified Interface
Table LC-2-6Monitor the specified interface
Using Actual Interface MAC Address
Modifying Virtual MAC Address
Monitoring and Maintaining Hsrp
Typical Configurations of Hsrp
An example for single hot standby group configuration
Show relevant Hsrp information Quidway# show standby
202.38.160.111
An example for setting Hsrp to monitor a specified interface
An example for multiple hot standby groups configuration
Fault Diagnosis and Troubleshooting of Hsrp
QoS Configuration QC
Apply CAR Rules to Packets Which is Matched the ACL
CAR Configuration Example
Configure CAR Rules Based on the MAC Address
II.Integrated Service
Three service types of QoS
Best-effort Service
QoS Overview
III. Differentiated Service
Functions of QoS
Chapter
Traffic Classification and Policing
II. CAR Committed Access Rate
Traffic Classification and Policing
Introduction to Traffic Classification
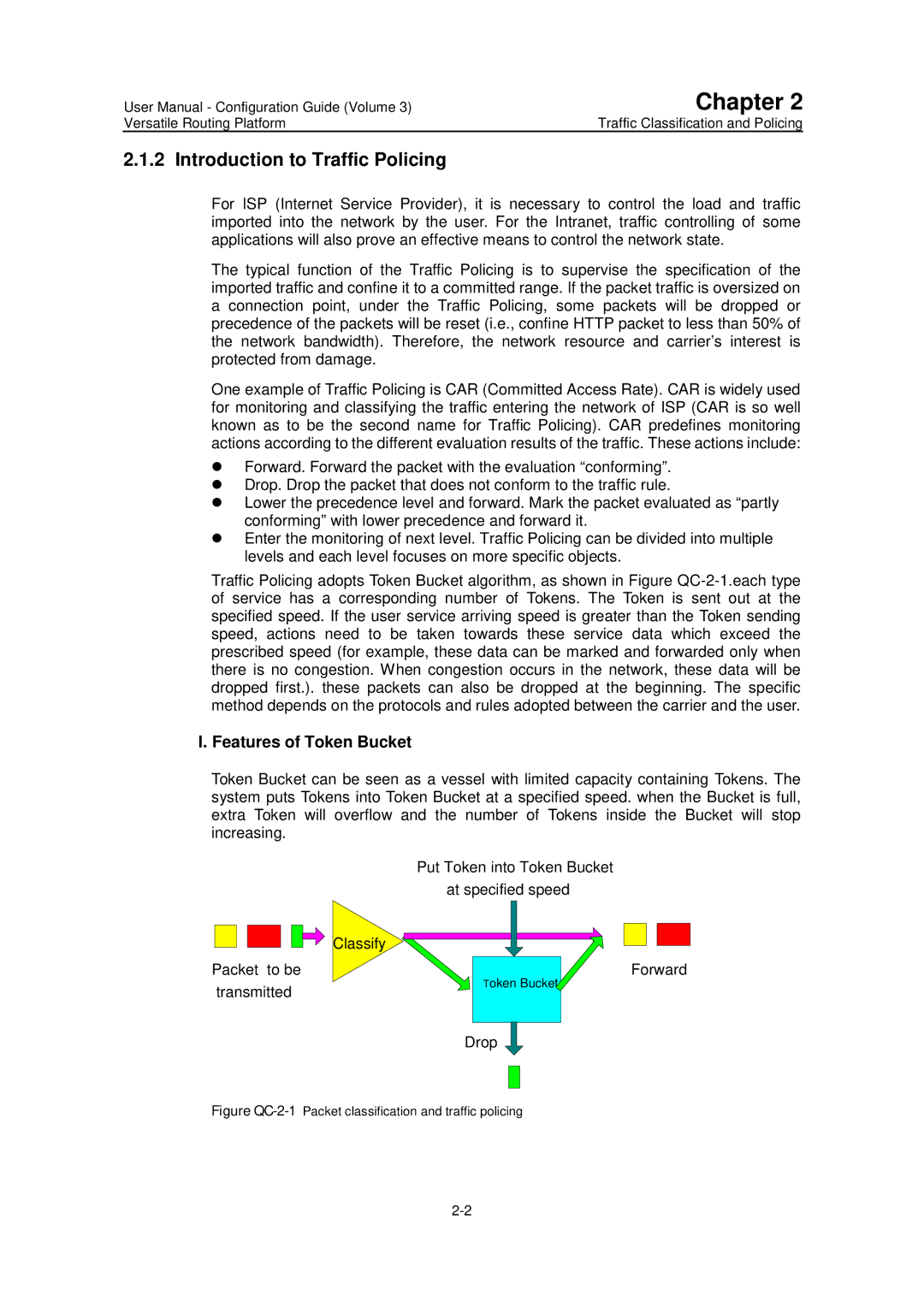
Features of Token Bucket
Introduction to Traffic Policing
III Complicacy Evaluation
Introduction to CAR
II.Traffic Measuring with Token Bucket
No CAR rule is specified by default
CAR Configuration
CAR Configuration Task List
Specify CAR rules
Apply the CAR Rule on the Interface
Monitoring and Maintenance of CAR
Table QC-2-3Monitoring and maintenance of CAR
Show CAR statistics Quidway# show car interface serial
Applying CAR Rules to All Packets
CAR Configuration Example
II.Configuration
Requirements
III. Configuration
Apply CAR Rules to Packets Which is Matched the ACL
II.Networking diagram
Configure CAR Rules Based on the Priority Level
Configure CAR Rules Based on the MAC Address
Chapter
About Congestion
Congestion Management
Congestion and Congestion Management
Congestion Management Policy
II. PQ Priority Queuing
IV. WFQ Weighted Fair Queuing
Fifo Queuing
III. CQ Custom Queuing
Selecting Congestion Management Policy
Working Principle of Congestion Management Policy
No. Advantages Disadvantages Queue
Fifo
III. CQ
PQ Configuration task list
Configuration of Congestion Management
Configuring PQ
II. Configuring priority queue
Priority-list list-number interface type number high medium
Normal low
III. Applying priority queue to the interface
Table QC-3-7Configuration of queue length of priority queue
Interface adopts Fifo queuing by default
IV. Maintaining and monitoring the priority queue
II. Configuring the custom queue
Configuring CQ
CQ configuration task list
Operation Command Configure the default custom queue
No custom-list list-number interface type number
Custom-list list-number queue queue-number byte-count
III. Applying custom queue to the interface
No custom-list list-number queue queue-number limit
No custom-list list-number queue queue-number byte-count
II. Configuring the weighted fair queue
Configuring WFQ
WFQ configuration task list
III. Maintenance and monitoring of the weighted fair queue
CQ Configuration Example
Configuration Example of Congestion Management
PQ Configuration Example
Figre QC-3-6Networking diagram of CQ Configuration
Versatile Routing Platform
Troubleshooting of Congestion Management
DDR Configuration DC
DDR in Which the Router Calls Back PC
Configuring Synchronous/Asynchronous Serial Port Using DDR
DDR Configuration
Configuration of Modem Management
Introduction to DDR Technology
DDR Configuration
Brief Introduction to Dial Configuration
Preparing DDR Configuration
Figure DC-1-1DDR configuration preparation flow
Configuration tasks of Legacy DDR include
Configuring DDR
Configuring Legacy DDR
II. Configure an interface to send calls
Dialer string dial-string isdn-address
Dialer rotary-group number
III. Configure an interface to receive calls
Figure DC-1-2Schematic diagram of Dialer Rotary Group
IV. Configure an interface to send and receive calls
Versatile Routing Platform DDR Configuration
Set the attribute parameters of Legacy DDR
Table DC-1-13Set the idle time of busy interface
Access-list access-list-number deny permit
Table DC-1-16Set access control of the dial interface
Access-list access-list-numberdeny permit
Permit deny
Introduction to Dialer Profile
Configuring Dialer Profile
Default interval is 300 seconds
IV. Set the attribute parameters of a dial interface
II. Configuration task list of Dialer Profile
III. Configure a logic dial interface
Significance of callback
Configuring Callback
Bind physical interfaces for a dialer pool
II. Terms and abbreviations
Or dialer caller remote-number
IV. Configure Isdn calling line identification callback
Dialer caller remote-number callback
Interface dialer
Configure PPP callback
User name callback-dialstring telephone-number
Chapter
Table DC-1-28Client end using Legacy DDR to configure PPP
Configuring DDR Special Functions
Configure Isdn dedicated line
Autodial interval is 300 seconds by default
II. Configure autodial
III. Configure cyclic use of dialer map
Name Meaning
Monitoring and Maintenance of DDR
Table DC-1-34Configure cyclic use of dialer map
Network requirements
DDR Typical Configuration Example
Legacy DDR
Chapter
Dialer Profile
Chapter
Point-to-Point DDR
Networking diagram
II. Configuration procedure
Chapter
Chapter
Point-to-Multipoint DDR
8810063
Chapter
Chapter
8810148
Multipoint-to-Multipoint DDR
8810052
III. Configuration procedure
Chapter
Chapter
Chapter
Chapter
DDR Bearing IPX
Chapter
Chapter
Chapter
DDR Bearing IP and IPX at the Same Time
Chapter
Chapter
Chapter
2.2
Flow Control of Dialer Profile MP over Dialer Profile-Case
RouterA RouterB BRI0
661012
Chapter
Figure DC-1-11Networking diagram of DDR Case
Channels for Dial-up and Connection to the Remote End Case
Chapter
Two Serial Ports for Dial-up and Remote Dial Connection Case
One Serial Port for Dial-up and Remote Dial Connection Case
Chapter
DDR for Access Service
Chapter
Chapter
Chapter
Chapter
DDR for Inter-Router Callback
Chapter
DDR in Which the Router Calls Back PC
III. Configuration procedure
DDR for Autodial
DDR Using Dialer Map Cyclically
DDR Using Dialer Map as Backup
Solution 1 Logical interface as backup interface
Chapter
Configuring Synchronous/Asynchronous Serial Port Using DDR
Precautions for DDR Configuration
Configuring Dialer-group
Configuring Network Layer Address
Configuring PPP In Dialer Profile Configuration Mode
Apply PAP authentication
Chapter
II. Apply Chap authentication
Chapter
Configuring PPP In Legacy DDR Configuration Mode
Chapter
II. Apply Chap authentication
Chapter
DDR Fault Diagnosis
Troubleshooting DDR
Configure Dialer-list
Whether modem is normal
III. Check whether dialer-group is configured
IV. Check whether dialer-list is configured correctly
Chapter
DDR Fault Elimination
Information displayed at the calling end
Troubleshooting with DDR Debugging Information
How to acquire DDR debugging information
Information displayed at the call receiving end
DDR link negotiation Down on interface
Modem Script
Configuration of Modem Management
Modem Management Functions Provided by VRP1.4
Function
Timeout seconds
Key words Description
Configuring Modem Call-In and Call-Out Authorities
Configuring Modem Management
Modem Management Configuration Task List
Configuring Modem Script
Specifying the Event to Trigger Modem Script
Configuring Modem Answer Mode
Executing Modem Script Manually
Typical Configuration of Modem Management
Managing Modem with Modem Script
Networking requirements
Direct Dial with Script
Configuration requirements
Router Initialization with Initialization Script
Interactively Connect Cisco Router Through Modem
VoIP Configuration VC
VoIP Configuration
IP Fax Configuration
Iphc Configuration
E1 Voice Configuration
GK Client Configuration
Versatile Routing Platform Table of Contents
VoIP Configuration
VoIP Overview
II. H.323 protocol stack
VoIP Principle
Basic composition
IP Voice Implementation over VRP
III. a typical telephone call processing by VoIP
IP Voice Feature over VRP
Switch Router Capacity channel
Chapter
VoIP Configuration Task List
Configuring Dial-peer
Pots dial-peer configuration
II. VoIP dial-peer configuration
Configuring Dial Terminator
Ip precedence priority-number
By default, we do not configure the dial terminator
Configuring Abbreviated Dialing
Configuring Voice Port
By default, we do not configure the abbreviated dialing
Table VC-1-6Configuring voice-port
By default, please use the shortest number match policy
Configuring Global Number Match Policy
Configuring the Recovery Method of Voice Board
VoIP Monitoring and Maintenance
By default, Watchdog is enabled
KHT
Rcvccactivecall
Channel = Status = Chtransframe
Typical VoIP Configuration Examples
Configuring Router FXS Port for Interconnection
III. Configuration procedures
Shanghai
Chapter
Figure VC-1-7RouterShenzhen FXO works in the Plar mode
LAN
VoIP Troubleshooting
III. Configuration description
Task List of IP Fax Configuration
IP Fax Configuration
Configuring IP Fax
Overview to IP Fax
Gateway does not use ECM mode by default
Checking If Configuring Fax to Use ECM Mode
Configuring Fax Rate
By default, the fax rate will be determined by voice mode
Configuring Fax Train Mode
Configuring Fax Local-train Threshold Value
Mode is local-train mode local by default
No fax protocol t38 ls-redundancy
Configuring Gateway Carrier Transmit Energy Level
Fax protocol t38 ls-redundancy number
Fax protocol t38 hs-redundancy number
By default, rtp protocol is used
Monitoring and Maintenance of IP Fax
By default, T.38 protocol is used
Typical Configuration of IP Fax
Versatile Routing Platform IP Fax Configuration
Chapter
Function of E1 Voice
E1 Voice Configuration
Overview of E1 Voice Configuration
Usage of cE1/PRI Interface
II. Protocols and standards supported
Features of E1 Voice
Signaling modes supported
III. Support single stage dialing and two-stage dialing
Configuring Pots dial-peer
E1 Voice Configuration
Configuration Task List of E1 Voice
IV. Integrated transmission of voice and data
Incoming called-number number
Configuring VoIP dial-peer
Table VC-3-1Configuration Commands of Pots dial-peer
No incoming called-number
Configuring the Basic Parameters of E1 Interface
Table VC-3-2Configuration Commands of VoIP dial-peer
Configuring Voice Port E1 Interface
Table VC-3-3Configuration Commands of E1 Interface
Table VC-3-4Configuration Commands of E1 Voice Port
Configuring E1 Voice R2 Signaling
Configuring DS0 group
II. Configuring Related Parameters of R2 Signaling
By default, the system has not created any DS0 group
Table VC-3-6Configuration Commands of R2 Signaling
No pri-group
Configuring the Basic Parameters of Isdn PRI Interface
Pri-group timeslots timeslots-list
Interface serial serial-no
Maintaining the MFC Channel and Circuit of the Specified TS
Monitoring and Maintenance of E1 Voice
Configuring Voice Port Isdn PRI Interface
II. show Command Related to E1 Voice
Quidway# show voice-port
III. debug Commands Related to E1 Voice
R2 signalling call statistics
Router Connected to PBX through E1 Voice Port
Typical Configuration Examples of E1 Voice
Table VC-3-11debug Commands of E1 Voice
Versatile Routing Platform
Router Connected to PBX in Isdn PRI Mode
Two-stage Dialing Configuration
II. Netwoking diagram
Parameter configuration of Beijing-side router
Transmission of Data and Voice Simultaneously
Fault Diagnosis and Troubleshooting of E1 Voice
Configuration Task List of GK Client
GK Client Configuration
Configuration of GK Client
Configuring One Interface as H.323 Gateway Interface
By default, GK Client function is deactivated
Configuring Gateway Alias
Configure the GK Server Name and Address
Activating or Deactivate GK Client Function
By default, there is not any tech-prefix
Configuring Tech-Prefix
Configuring GK Interworking Mode
Versatile Routing Platform GK Client Configuration
Typical Configuration Examples of GK Client
Be default, the GK interworking mode is cisco mode
Chapter
Fault Diagnosis and Troubleshooting of GK Client
Iphc Configuration
Overview of Iphc
Enable/disable RTP header compression
Iphc Configuration
Configuration Task List of Iphc
No ip rtp compression-connections
By default, the udpchk field in UDP packet field is set to
Configure the Cisco-compatible RTP header compression
Configure the deleting of udpchk field from UDP header
No ip tcp header-compression
Monitoring and Maintenance of Iphc
Table VC-5-6Monitoring and Maintenance of Iphc
How Are We Doing
Excellent Good Fair Poor
Mistake Suggested Correction Line No