Sun StorEdge 5310 NAS Troubleshooting Guide
Please Recycle
Contents
NAS Head 1 Hardware
Contents
Storage Arrays 1 Fibre Channel FC
Clustering 1 Overview Checkpoints/Snapshots 1 Overview
Viii Sun StorEdge 5310 NAS Troubleshooting Guide December
Boot Block Post Progress LED Code Table Port 80h Codes
Tables
Storage Array Status Icon Quick Reference Standard Terms
Figures
Array Management Window
Write ordering on the Mirror
Removing the SFP Transceiver and fibre Optic Cable
Preface
Typographic Conventions
Who Should Use This Book
How This Manual is Organized
Table P-1Typographic Conventions
Related Documentation
Accessing Sun Documentation Online
Ordering Sun Documents
Sun Welcomes Your Comments
Shell Prompts in Command Examples
Table P-2Shell Prompt
Troubleshooting Overview
How to Use This Manual
2Sun StorEdge 5310 NAS Troubleshooting Guide December
Troubleshooting Tools
High-Level Troubleshooting Tasks
Troubleshooting Procedures
Log Message Severity Levels
Initial Troubleshooting Guidelines
Troubleshooting Flow Charts
Follow the steps below to diagnose hardware problems
Diagnostic Information Sources
StorEdge Diagnostic Email
To collect diagnostics, proceed as follows
Collecting Information from the Sun StorEdge 5310 NAS
Accurately quantify the problem
Data Collection for Escalations
Collect general data
Data Collection for Specific Issues
Check remote access capabilities
Software compatibility issues
Security Issues
User access token
Cacls
Proc filesystem
StorEdge network capture utility
Network trace
Client and Server data
Duplication instructions
1List of Adapters
2.9 TCP/IP Connectivity problems
2Routing Table
Network Configuration
Performance Issues
Configuration
Command Line performance utilities
Other processes / High CPU Utilization
Log Error Messages Syslog
Understanding Sun StorEdge 5310 NAS Log Messages
Components of an Event Message
Time/date Severity
Severity Level Definitions highest to lowest
About SysMon Error Notification
Sun StorEdge 5310 NAS Error Messages
UPS Subsystem Errors
Table A-3UPS Error Messages
Controller Cache Disabled
Table A-5PEMS Error Messages
File System Errors
Table A-4File System Errors
Pems Events
Power supply failure
Tools Required
Maintenance Precautions
Preparation Procedures
Electrostatic Discharge Information
Grounding Procedure
Static Electricity Precautions
Static Electricity
28Sun StorEdge 5310 NAS Troubleshooting Guide December
NAS Head
Hardware Contacting Technical Support
Problems With Initial System Startup
Checklist
Shutdown Commands for Software Menu
Resetting the Server
Shutdown Commands for Hardware LCD Display
Specific Problems and Corrective Actions
Preparing the System for Diagnostic Testing
1Index to Problems
Server Does Not Power On
Problems Starting Up
Front Panel is Unresponsive and Video is Disabled
Server Beeps at Power On or When Booting
2Bootup Beep Codes
Server Starts Booting Automatically at Power On
Power-On Self-Test Post
System Cooling Fans Do Not Rotate Properly
Power LED Does Not Light
Verifying Proper Operation of Key System LEDs
Problems with Network
Cannot Connect to a Server
Diagnosing System Errors
Troubleshooting the Server Using Built- In Tools
Other Problems
Beep Codes
LEDs and Pushbuttons
LEDs
Post Screen Messages
Front Panel LEDs and Pushbuttons
Post
Front Panel LEDs
4Front Panel LEDs
14Sun StorEdge 5310 NAS Troubleshooting Guide December
Front Panel Pushbuttons
5Front Panel Pushbuttons
Rear Panel LEDs
2Rear Panel LEDs 6Rear Panel LEDs
6Rear Panel LEDs
Critical Condition
Front-Panel System Status LED
7System Status LED States
Non-Critical Condition
Degraded Condition
Rear Panel Power Supply Status LED
8Power Supply Status LED States
Server Main Board Fault LEDs
5Fault and Status LEDs on the Server Board
22Sun StorEdge 5310 NAS Troubleshooting Guide December
System ID LEDs
6Location of Front-Panel ID Pushbutton and LED
Power-On Self Test Post
9Standard Post Error Messages and Codes
System memory size error Yes
10Extended Post Error Messages and Codes
Post Error Beep Codes
11BMC-Generated Post Beep Codes
12BIOS-Generated Boot Block Post Beep Codes
08h
Bios Recovery Beep Codes
13Memory 3-Beep and LED Post Error Codes
0Ch
Post Progress Code LED Indicators
14BIOS Recovery Beep Codes
15Boot Block Post Progress LED Code Table Port 80h Codes
7Examples of Post LED Coding
16POST Progress LED Code Table Port 80h Codes
Post Progress LED Code Table Port 80h Codes
34Sun StorEdge 5310 NAS Troubleshooting Guide December
Post Progress LED Code Table Port 80h Codes
Filesystem Check fsck Procedure
OS Operations
StorEdge Network Capture Utility
Upgrades Cacls Access Control List
Proc filesystem
FTP Server
Updating the OS on the Sun StorEdge 5310 NAS
Sun StorEdge 5310 NAS Firmware
Operating System
8The Update Software Panel
Common Problems Encountered on the Sun StorEdge 5310 NAS
CIFS/SMB/Domain
Cannot join Windows Domain
NAS Head
46Sun StorEdge 5310 NAS Troubleshooting Guide December
NAS Head
Reboot the StorEdge
Lost Connection with Windows Domain
50Sun StorEdge 5310 NAS Troubleshooting Guide December
StorEdge has same files in 2 different shares
Can’t copy greater than 4G file from Windows to StorEdge
Can’t map drives via CIFS/SMB
Cannot see the security tab from Windows clients
At the CLI, enter set smb.dirsymlink.disable yes
CIFS/SMB share created to /cvol is not visible or accessible
56Sun StorEdge 5310 NAS Troubleshooting Guide December
Users from trusted domains cannot access StorEdge
Connection to Samba domain controller fails
Dial-up CIFS/SMB clients cannot connect to StorEdge
Windows local groups cannot be added to Access Control List
Log Message Share database corrupt
Can’t create new DTQ
NFS Issues
NFS root user doesnt have appropriate access
Trusted host does not have root access
Local NIS files are no longer updating
64Sun StorEdge 5310 NAS Troubleshooting Guide December
NAS Head
When is it necessary to add a TCP/IP route?
Network Issues
How do I manually add a TCP/IP route?
NIC speed and duplex negotiation issues
Default gateway changes without user input
How can I disable RIP routing?
StorEdge is only reachable from systems on the local subnet
File System Issues
File system inaccessible mount failure
Can’t write to file system
File system related error messages
NAS Head
Drive Failure Messages
Light on one of the hard drives is red
Drive has failed how do I replace it?
Log message LUN critical Email alert LUN critical
File and Volume Operations
Free space not immediately available after delete
Can’t delete a file
After deleting files, volume free space remains the same
Can’t delete files from /etc directory
Cant run StorEdge Web Admin or some screens incorrect
Administration Interfaces
Cant run GUI, Java certificate expired message
StorEdge Web Admin missing Icons or GUI does not respond
Web GUI login failure
Web GUI session aborted while performing administration
How do I reset the StorEdge administrator password?
NAS Head
StorEdge Features and Utilities
Load unixtools Ll /cvol
StorEdge fails to send diagnostic email
Hardware Warning Messages
Log Message Blower Fan has failed
Log message Low Battery
Log message Controller write-back cache is enabled
UPS Messages
Front LCD panel message P21 Power 1 Failed
Light on one of the power supplies is amber
What do the Status LED Indicators on front panel indicate?
17Status LED Indicators
Network backup fails due to .attic$ directory
Backup Issues
Tape library not recognized
Ndmp Can’t browse backup history
Ndmp backup fails access denied message
Ndmp incremental/differential backups back up all files
Direct Attached Tape Libraries
Local backup or restore fails with ?PNReduce error? in log
Ndmp Can?t browse backup history
CIFS/SMB/Domain Issues
Frequently Asked Questions
How do I configure local SMB groups?
NAS Head
94Sun StorEdge 5310 NAS Troubleshooting Guide December
How do I create hidden shares?
What does the umask setting do?
NAS Head
How do I modify existing user and group credential mappings?
NAS Head
How do I set up the SMB Autohome directory feature?
NAS Head
102Sun StorEdge 5310 NAS Troubleshooting Guide December
What are the limitations of Workgroup mode?
Does StorEdge support Domain Local Groups?
Does StorEdge support DFS?
24 NIS/NIS+ Issues
How do I set up NIS or NIS+?
What support is there for Windows Server Manager?
How do I configure the NS lookup order?
25 TCP/IP and Network Configuration
What is port aggregation?
How do I set up port aggregation?
How do I disable port aggregation?
What is IP aliasing?
How do I set up IP aliasing?
How do I configure Jumbo Frames support?
Quota Configuration
Can I set more than one default gateway?
110Sun StorEdge 5310 NAS Troubleshooting Guide December
How do I configure user and group quotas at the CLI?
How do I set up Directory Tree Quotas DTQs?
NAS UI
Dtq remove volume=volume-name name=dtq-name
How do I disable quotas?
How do I create a DTQ for an existing directory?
How does the default quota work?
Checkpoint Configuration
What are checkpoints?
How do I set up checkpoints?
Select option 7, Save Changes or press Esc to cancel
How do I manage checkpoints from the command line?
How do I disable checkpoints?
How do I recover deleted files from a checkpoint?
Volume Creation and Expansion
How do I create a volume?
How do I extend the size of an existing volume?
How do I rename an existing volume?
How do I delete an existing volume?
What is the function of the /proc volume?
What is the function of the .attic$ directory?
What is the function of the /etc directory?
Reserved Filesystems and Directories
What is the function of the /dvol volume?
What is the function of the /cvol volume?
How do I share files with NFS users?
Select option M, Trusted Hosts
How do I manage NFS exports via the StorEdge Web Admin?
How do I manage NFS exports via the configuration files?
Object type path hosts or groups security
Administration Interfaces and Utilities
How do I access the StorEdge administration interfaces?
How do I collect diagnostics from StorEdge?
How do I set up Smtp email?
How do I set up local or remote logging?
132Sun StorEdge 5310 NAS Troubleshooting Guide December
How do I set up NTP or RDATE?
How can I capture network traffic to and from the StorEdge?
How do I access command history at the CLI?
136Sun StorEdge 5310 NAS Troubleshooting Guide December
SE5310 rm /vol1/dir1/file1
Rmdir /vol1/d1 /vol1/d2 /vol1/d3 /vol1
How do I set up an FTP server on StorEdge?
How do I configure the FTP service to load automatically?
How do I configure and secure rsh access?
How do I access a shell prompt from the StorEdge CLI?
Set rshd.allow.cmd.user yes
Backup and Migration Issues
NAS Head
How do I set up Ndmp to backup the StorEdge?
What the best way to migrate data to or from StorEdge?
How do I view the Ndmp backup log?
How do I share files with Mac Users?
Macintosh Connectivity
How do I move files from one disk to another with NDMP?
What does the desktop DB option in the shares menu do?
Miscellaneous Log Messages
System log message statmon error no statmon, remote
System log message ARP information overwritten
Scsi ID Settings
18Supported Tape Libraries and Tape Drives
How Does File Replicator work?
Disaster Recovery
StorEdge File Replicator
What are the applications for File Replicator?
How do I set up File Replicator?
Backup
Data Distribution
To activate Mirror License both systems, do the following
StorEdge File Replicator Issues
Enter the desired size of the Mirror Buffer
Mirror Promoted on host
Error Initializing mirror buffer
Mirror stops when creating buffer
Waiting on host, link is down
EXT Free Pages
Array Overview
Fibre Channel FC
Module Description
Controller Battery
Controllers
Controller Memory
2Label Locations on the Controller
3Battery Charging/Charged and Cache Active Lights
Drives
Fans
5Drive Numbering Rackmount Module
Power Supplies
SFP Transceivers and Cables
Tray ID Switch
8SFP Transceiver and fibre Optic Cable
Using the Array
Removing and Replacing the Back Cover
Turning On the Power
10Removing and Replacing a Deskside Module Back Cover
Check the status of each module and it components
Turning Off Power for a Planned Shutdown
12Sun StorEdge 5310 NAS Troubleshooting Guide December
12and -1shows the locations of the status lights
1Lights on the Back of a Command Module
Fan Fault Amber Off Replacing Fan on
Turning Off Power for an Unplanned Shutdown
Storage Arrays
Restoring Power After an Unplanned Shutdown
Yes Go to step No Go to step
Responding to the Optional Audible Alarm
13Alarm Mute Button
Yes Go to . No Go to step
Troubleshooting and Recovery
Troubleshooting the Module
Storage Arrays
Lights on the Back of a Command Module
3Lights on the Back of a Command Module
Recovering from an Overheated Power Supply
Did the power supplies restart automatically?
16Power Supply Switches
Setting the Tray ID Switch
17shows the location of the Tray ID switch
Verifying the Link Rate Setting
17Setting the Tray ID Switch
Relocating a Command Module
Upgrade Requirements
Adding New Drives
Upgrade Methods
Replace Existing Drives with Greater Capacity Drives
Replace All Drives at the Same Time
Adding New Drives to Empty Slots
Replace One Drive at a Time
Locate the blank drives in the command module
Repeat and to install each new drive
Replacing All Drives at the Same Time
Put on antistatic protection Unpack the new drives
Yes- Go to . No Go to step
20Power Supply Switches
Replacing One Drive at a Time
Put on antistatic protection Unpack the new drives
Yes- Go to . No Go to step
22Removing and Installing a Drive
Relocation Considerations
Relocate Drives or Modules
Convert an Command Module to a Drive Module
Raid Storage Manager RSM
Client Software Windows
23Enterprise Management Window
Enterprise Management Window
25Enterprise Management Window
Device Tree
26Device Tree Example
Enterprise Management Window Menus
Device Table
4Enterprise Management Window Menus
Enterprise Management Window Toolbar
Array Management Window
5Enterprise Management Window Toolbar Buttons
Array Management Window Tabs
27Array Management Window
Array Management Window Menus
6Array Management Window Tabs
7Array Management Window Menus 1
Array Management Window Toolbar
8Array Management Window Toolbar Buttons
Protecting Your Data
Software Redundancy
Snapshot Volumes
Volume Copy
Remote Volume Mirroring
RAID Levels and Data Redundancy
Storage Arrays
9RAID Level Configurations
RAID
Hardware Redundancy
Controller Cache Memory
Hot Spare Drives
Background Media Scan
6.8 I/O Data Path Protection
Multi-Path Driver with AVT Enabled
Channel Protection
Password Protection
Multi-Path Driver with AVT Disabled
Volumes and Volume Groups
Configuring Storage Arrays
Password Failure Reporting and Lockout
Volume Groups
Standard Volumes
28Unconfigured and Free Capacity Nodes
Specifying Volume Parameters from Free Capacity
Specifying Volume Parameters from Unconfigured Capacity
Mappings View
29Mappings View Window
11Volume-to-LUN Terminology
10Mappings View Tab
70Sun StorEdge 5310 NAS Troubleshooting Guide December
Register the Volume with the Operating System
SANshare Storage Partitioning
SANshare Storage Partitioning Example
SANshare Storage Partitioning involves three key steps
Heterogeneous Hosts
Heterogeneous Hosts Example
31Host Port Definitions Dialog
32Heterogeneous Hosts Example
Storage Arrays
Dynamic Volume Expansion DVE
33DVE Modification Operation in Progress
80Sun StorEdge 5310 NAS Troubleshooting Guide December
Data Replication
82Sun StorEdge 5310 NAS Troubleshooting Guide December
Managing Persistent Reservations
34Persistent Reservations Dialog
Maintaining and Monitoring Storage Arrays
Storage Array Health
Storage Array Status Icons
Event Monitor
12Storage Array Status Icon Quick Reference
36Event Monitor Configuration
37Event Monitor Example
Storage Arrays
Problem Notification
Storage Array Problem Recovery
38Problem Notification in the Array Management Window
39Displaying the Recovery Guru Window
40Recovery Guru Window Example
41Status Changes During an Example Recovery Operation
Updating Firmware and Nvsram on the Array
Start the SMclient
Storage Arrays
Example, c\temp\rsmfw\ Select N2882-610843-5xx.dlp
Updating ESM Firmware
Select Start to begin the upgrade
StorEdge File Replicator
Overview
1Standard Terms
NBD
Pseudo Real-time Mirroring
Real-time Mirroring
StorEdge File Replicator
1The lifecycle of a transaction in StorEdge File Replicator
2Write ordering on the Mirror
3Lost transaction handling on the Mirror
Mirroring Variations
Many-to-One Mirroring
One-to-Many Mirroring
Piggyback or Cascading Mirroring
Replication
Operational State
Bi-directional Mirroring
Push Technology
Mirror Creation
Mirror Replication
Link Down and Idle Conditions
Mirror Sequencing
Cracked and Broken Mirrors
Filesystem errors, such as run check, directory broken, etc
Cannot perform first-time synchronization of mirror system
14Sun StorEdge 5310 NAS Troubleshooting Guide December
Clustering
2Sun StorEdge 5310 NAS Troubleshooting Guide December
Volumes
Checkpoints/Snapshots
Physical and Logical Volume Relationship
Checkpoint Lifecycle
Checkpoint Creation
Active Checkpoint
2The Copy-On-Write Mechanism for Checkpoints
3Mappings for Block n Before Modification
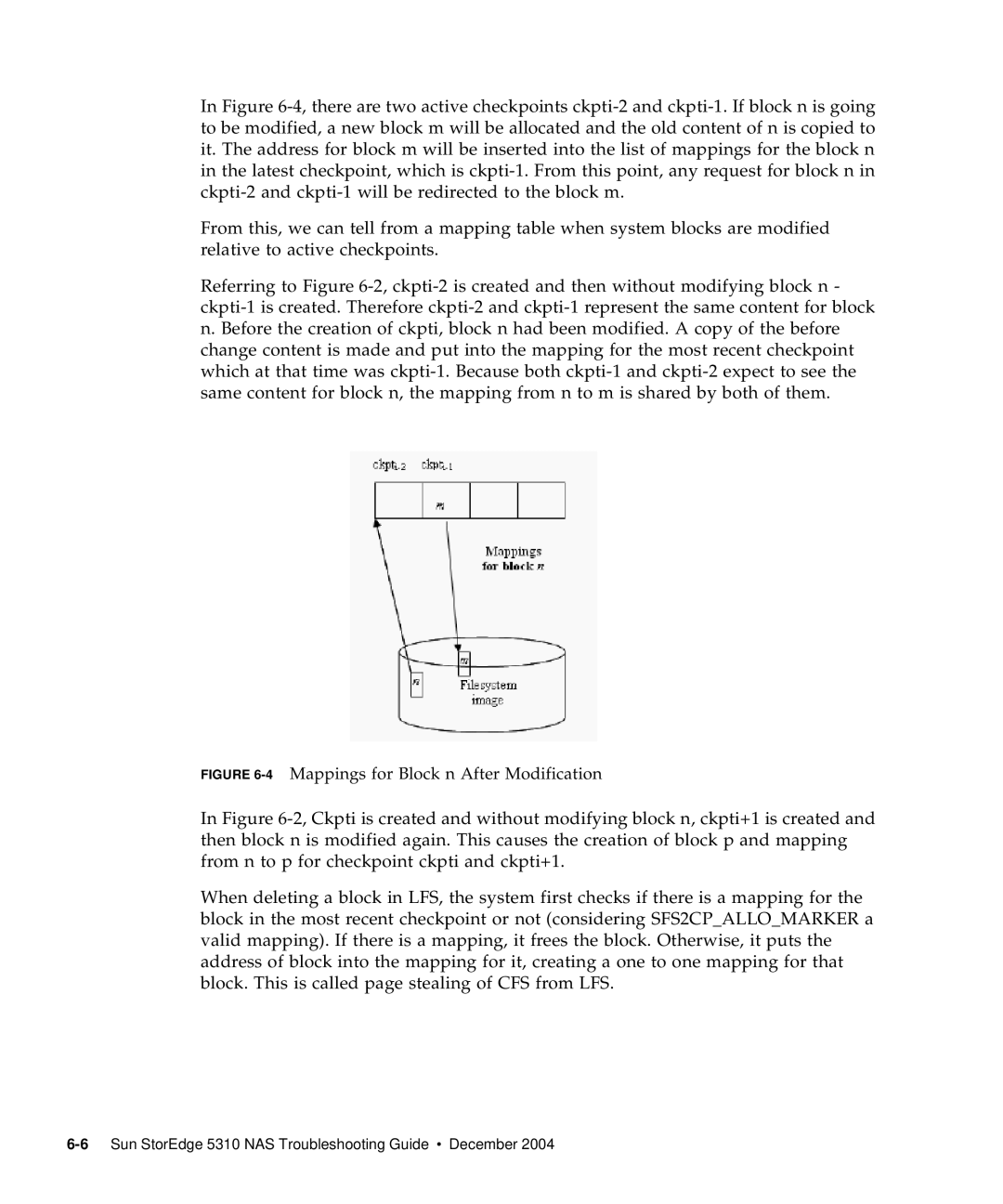
4Mappings for Block n After Modification
Translation of File System Objects in Checkpoints
Src directory entry
Src inode nlink =
Entry Dst directory entry Src inode nlink = Entry y
Checkpoint Deletion
6Mappings for Block n After Deleting ckpti-1
Local Directory Checkpoint Access
Checkpoint management commands
Checkpoint Scheduling
Accessing Checkpointed Data
8Accessing .chkpnt in Unix
Compatibility Issues
Syntax for the command is
9Accessing .chkpnt in Windows Explorer
Object Checkpoint Restore
10Viewing .chkpnt in Windows Explorer
StorEdge cp Command
11Sharing Blocks Between Live and Checkpoint File Systems
18Sun StorEdge 5310 NAS Troubleshooting Guide December
Checkpoints/Snapshots
20Sun StorEdge 5310 NAS Troubleshooting Guide December
FRU/CRU Replacement Procedures
Tools and Supplies Needed
Safety Before You Remove the Cover
Determining a Faulty Component
Removing and Replacing the Cover
Set the cover aside and away from the immediate work area
Field Replaceable Unit FRU Procedures
NAS Head FRU Replacement Procedures
2Sun StorEdge 5310 NAS Bezel Replacement
Opening the Front Bezel
Memory
3Sun StorEdge 5310 NAS Expansion Unit
Power Supply Unit
Sun StorEdge 5310 NAS Power Supply
4Replacing the Power Supply
Fan Module
Sun StorEdge 5310 NAS Fan Module Removal
5Removing the Fan Module
Sun StorEdge 5310 NAS Fan Module Replacement
High Profile Riser PCI Cards
Gigabit Ethernet Card
6The Gigabit Ethernet Card in the Low Profile Riser Slot
Low Profile Riser PCI Cards
Qlogic HBA Removal and Replacement
LCD Display Module
Backup of /dvol/etc
Flash Disk Module
Replacing the Flash Disk
Upgrade and Configuration Recovery
Flash Disk
Reboot the server to complete the upgrade process
Super FRU Installation
System FRU Super FRU
Replacing a Controller
Array FRU replacement Procedures
Tools and Equipment
Procedure
FRU/CRU Replacement Procedures
Are you using the battery from the old controller?
12Replacing the Controller Battery
13Label Locations for the Controller
Replacing a Controller Battery
14Controller Host Link, Drive Link, and Fault Lights
Procedure
15Removing the SFP Transceiver and fibre Optic Cable
Date of Installation Enter todays date
17Removing the Controller Cover Upside Down View
19Label Locations on the Controller
Is the problem corrected?
20Drive Link, Host Link, Battery, and Fault Lights
Replacing a Drive
FRU/CRU Replacement Procedures
21Replacing a Drive
Replacing a Fan
22Replacing a Fan
Replacing a Power Supply
42Sun StorEdge 5310 NAS Troubleshooting Guide December
Check the Power and Fault light on the new power supply
Replacing an SFP Transceiver
24Replacing an SFP Transceiver
Yes Go to step No Contact technical support