Configuring and Monitoring Port Security
Reading Intrusion Alerts and Resetting Alert Flags
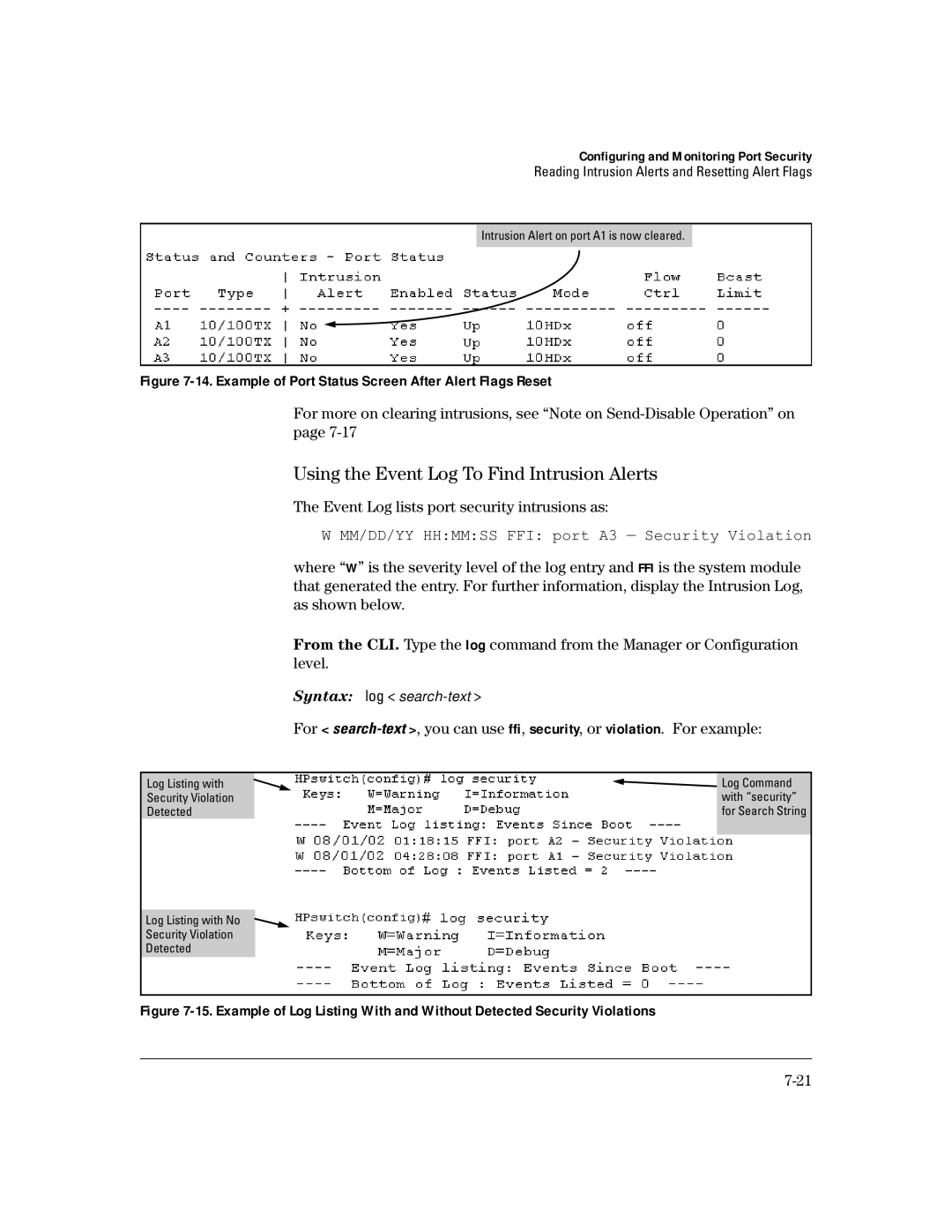
Intrusion Alert on port A1 is now cleared.
Figure 7-14. Example of Port Status Screen After Alert Flags Reset
For more on clearing intrusions, see “Note on
Using the Event Log To Find Intrusion Alerts
The Event Log lists port security intrusions as:
W MM/DD/YY HH:MM:SS FFI: port A3 — Security Violation
where “W” is the severity level of the log entry and FFI is the system module that generated the entry. For further information, display the Intrusion Log, as shown below.
From the CLI. Type the log command from the Manager or Configuration level.
Syntax: log <
For <
Log Listing with Security Violation Detected
![]()
![]() Log Command with “security” for Search String
Log Command with “security” for Search String
Log Listing with No
Security Violation
Detected