RADIUS Authentication and Accounting
Configuring the Switch for RADIUS Authentication
|
| Specifies the maximum time the switch waits for a response |
|
| to an authentication request before counting the attempt as |
|
| a failure. (Default: 3 seconds; Range: 1 - 15 seconds) |
|
| |
|
| If a RADIUS server fails to respond to an authentication |
|
| request, specifies how many retries to attempt before closing |
|
| the session. Default: 3; Range: 1 - 5) |
|
|
|
Note | Where the switch has multiple RADIUS servers configured to support authen- | |
|
| tication requests, if the first server fails to respond, then the switch tries the |
|
| next server in the list, and |
|
| attempts to use the secondary authentication method configured for the type |
|
| of access being attempted (console, Telnet, or SSH). If this occurs, refer to |
|
| |
|
| ment and Configuration Guide for your switch. |
|
| For example, suppose that your switch is configured to use three RADIUS |
|
| |
|
| servers for authenticating access through Telnet and SSH. Two of these servers |
|
| use the same encryption key. In this case your plan is to configure the switch |
|
| with the following global authentication parameters: |
|
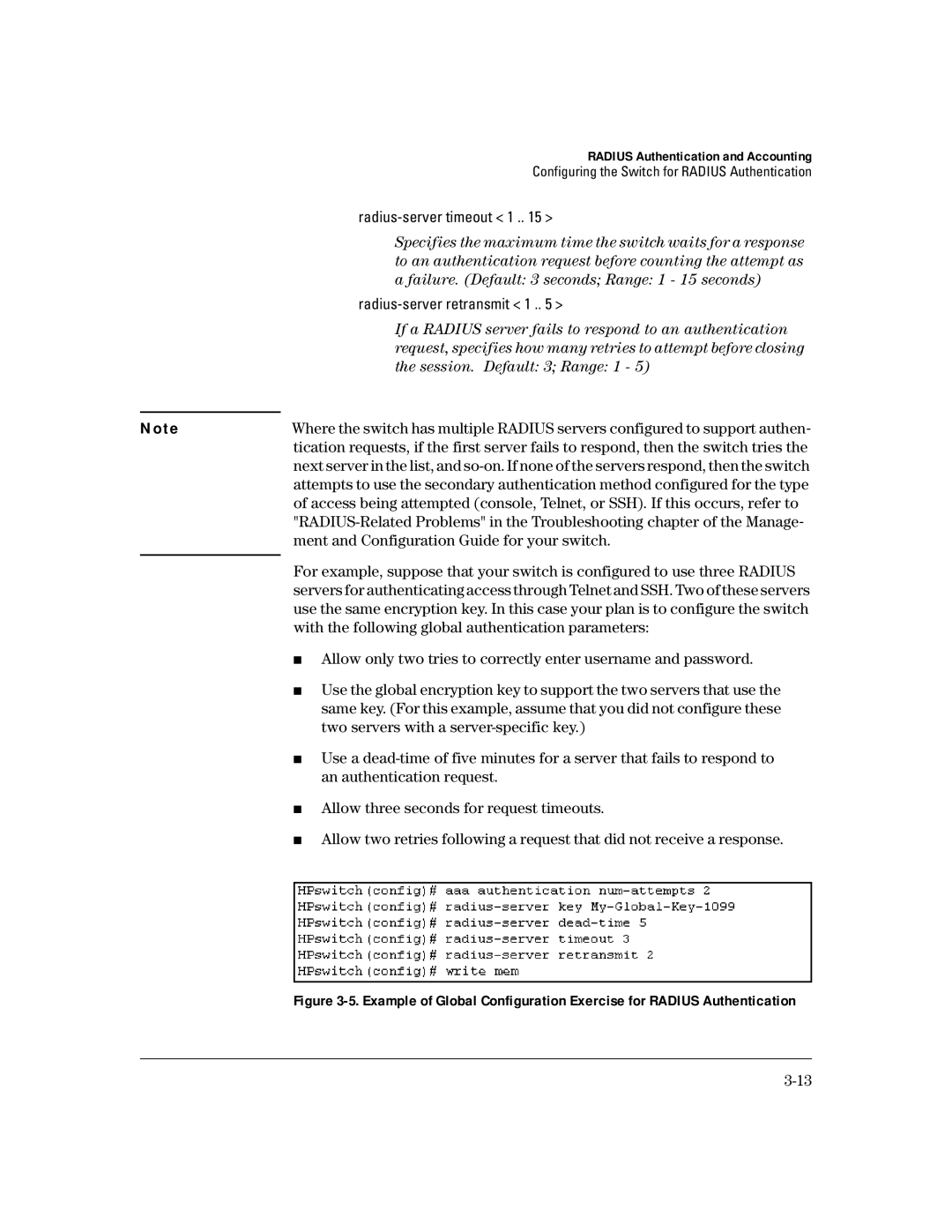
| ■ Allow only two tries to correctly enter username and password. |
|
| ■ Use the global encryption key to support the two servers that use the |
|
| same key. (For this example, assume that you did not configure these |
|
| two servers with a |
|
| ■ Use a |
|
| an authentication request. |
|
| ■ Allow three seconds for request timeouts. |
|
| ■ Allow two retries following a request that did not receive a response. |
|
|
|
|
|
|