Configuring and Monitoring Port Security
Port Security Command Options and Operation
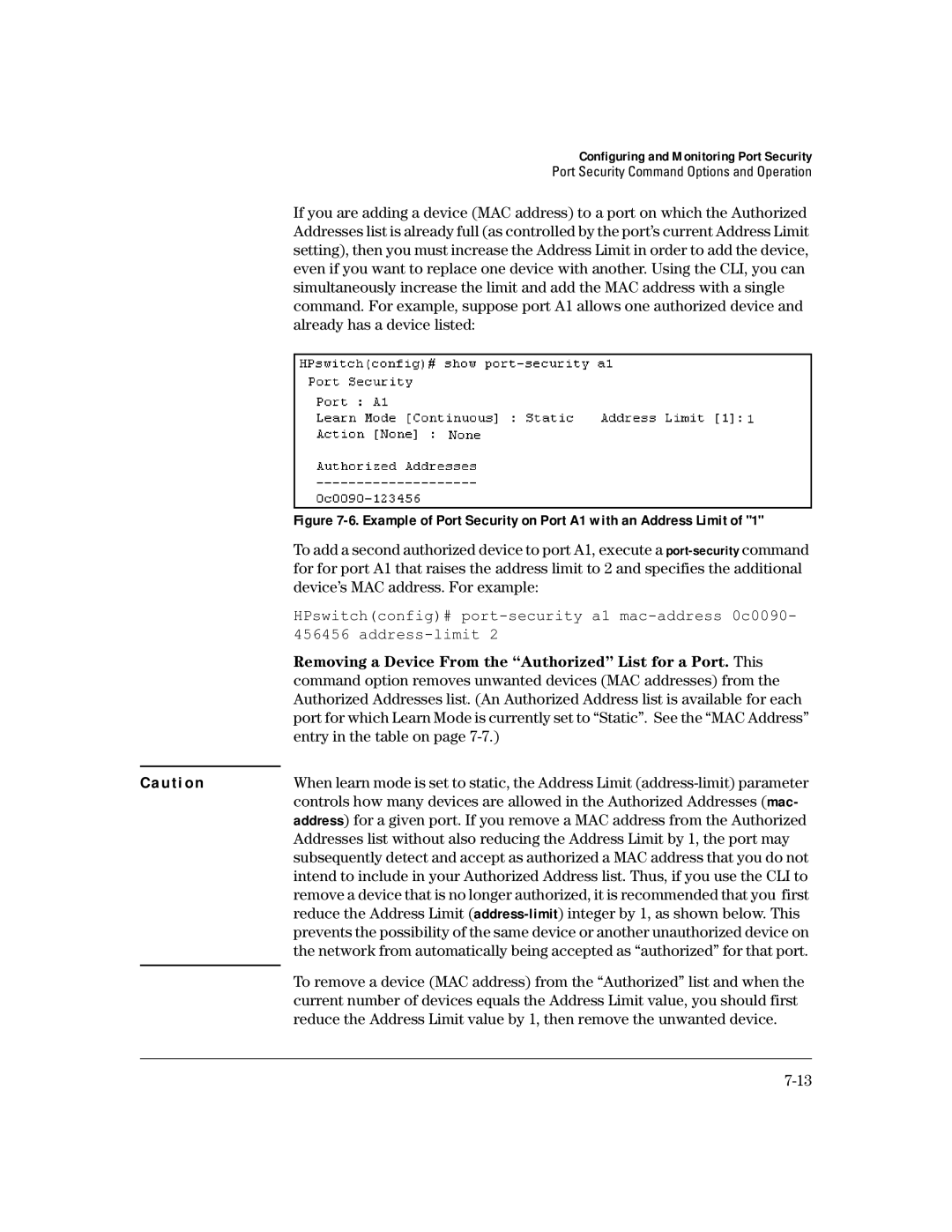
If you are adding a device (MAC address) to a port on which the Authorized Addresses list is already full (as controlled by the port’s current Address Limit setting), then you must increase the Address Limit in order to add the device, even if you want to replace one device with another. Using the CLI, you can simultaneously increase the limit and add the MAC address with a single command. For example, suppose port A1 allows one authorized device and already has a device listed:
| Figure |
| To add a second authorized device to port A1, execute a |
| for for port A1 that raises the address limit to 2 and specifies the additional |
| device’s MAC address. For example: |
| HPswitch(config)# |
| 456456 |
| Removing a Device From the “Authorized” List for a Port. This |
| command option removes unwanted devices (MAC addresses) from the |
| Authorized Addresses list. (An Authorized Address list is available for each |
| port for which Learn Mode is currently set to “Static”. See the “MAC Address” |
| entry in the table on page |
|
|
C a u t i o n | When learn mode is set to static, the Address Limit |
| controls how many devices are allowed in the Authorized Addresses (mac |
| address) for a given port. If you remove a MAC address from the Authorized |
| Addresses list without also reducing the Address Limit by 1, the port may |
| subsequently detect and accept as authorized a MAC address that you do not |
| intend to include in your Authorized Address list. Thus, if you use the CLI to |
| remove a device that is no longer authorized, it is recommended that you first |
| reduce the Address Limit |
| prevents the possibility of the same device or another unauthorized device on |
| the network from automatically being accepted as “authorized” for that port. |
| To remove a device (MAC address) from the “Authorized” list and when the |
| |
| current number of devices equals the Address Limit value, you should first |
| reduce the Address Limit value by 1, then remove the unwanted device. |