Abstract
Ignite-UX Administration Guide
Acknowledgements
Revision History
B2355-90849 HP-UX 11.00, 11i v1, 11i v1.6, 11i
Contents
Managing I/O for installation and recovery
Complex networks challenges and solutions
Simple network creating a server for anonymous clients
Complex networks multi-capable servers
Security
Booting and installing HP-UX on clients using the server 110
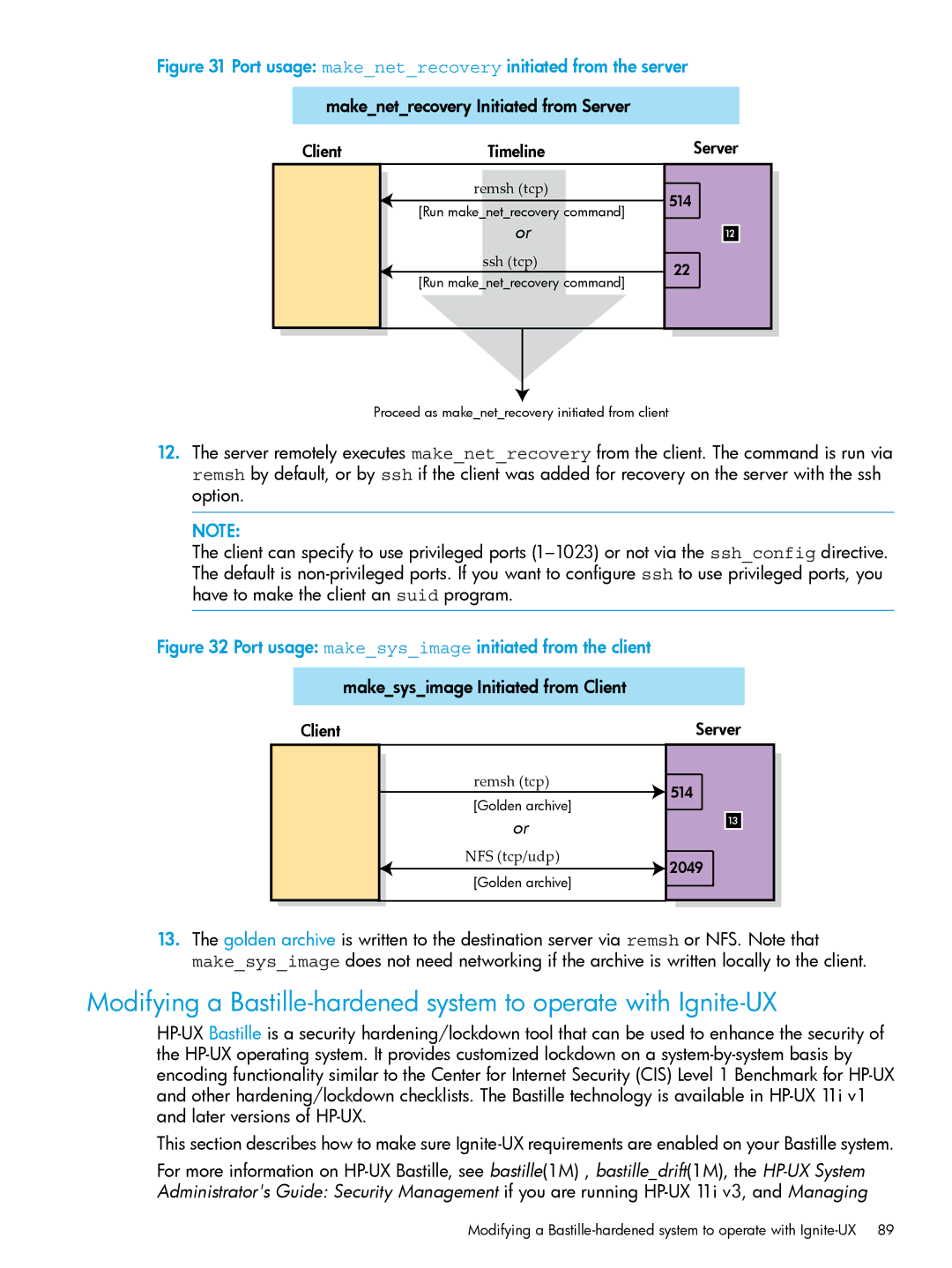
Automating installations 174
Customizing your installation 161
Creating your own boot and installation media 180
Golden images 151
Support and other resources 224
Recovery 191
Configuring Dhcp services 236
Documentation feedback 227 Troubleshooting 228
LIF volume contents 239
Terminal keyboard shortcuts 255
HP secure development lifecycle
Ignite-UX overview
Ignite-UX features
Custom installations
One-step installation
Automated installations
Create custom installation media
Ignite-UX bundles available in the Ignite-UX product
Getting the Ignite-UX software
Ignite-UX command manpages
Ignite-UX commands and manpages
Ignite-UX GUI
Introduction to the Ignite-UX GUI
View menu
File menu
Actions menu
Options menu
Client status dialog box
How Ignite works
Boot sources
Ignite-UX install environment
Installation versus recovery
Network booting and IP addresses
PA-RISC Systems
Phases of operation
Itanium-Based Systems
Startup
Phase
Hardware requirements
Ignite-UX server requirements
Other considerations
Disks and other I/O
Supported peripherals
Firmware
Disk arrays
Simple network solutions
Making configuration decisions for Ignite servers
Boot and install client from media
Instlboottab
Alternate boot with network server installation
Use DVD media to boot a system for network installation
Diagnosing network boot issues
Complex networks
For a detailed discussion, see
Instlboots allow
Investigate instlbootd errors in /var/adm/syslog/syslog.log
HP-UX diagnosing and debugging
Simple network debugging
RDP diagnosing and debugging
Simple network creating a server for registered clients
Configuring the Ignite-UX server for PA-RISC clients
Launch Ignite-UX
Ignite
Ignite-UX GUI welcome dialog box
Launch the server setup wizard
Server setup wizard
Register the PA-RISC clients with the server
Configure booting IP addresses
Skip Dhcp setup
Configuring the Ignite-UX server for Itanium-based clients
Go to the software setup section
Register the Itanium-based clients with the server
Setting up software from OE depots
Configuring server options
More server setup options
Ignite-UX server configuration tabs
Add Dhcp addresses dialog box
Configuring session options
Session options tab
Example Create a configuration for compiler software
Setting up additional software on the server
SD software
Non-SD software
Simple network creating a server for registered clients
Editing the instlboottab file
Using the server setup wizard
Itanium-based clients use Dhcp to boot anonymously
Simple network creating a server for anonymous clients
Working with Dhcp
Understanding PXE booting of Itanium-based systems
Ignite-UX server and boot helper setup for Dhcp
Page
Isolating Ignite-UX from noncontrollable Dhcp servers
Since the install kernel and install file system must be
Dhcpclassid=IgniteDHCPDeviceGroup
Class-id=PXEClientArch00002IgniteDHCPDeviceGroup
Page
Complex network challenges
Complex networks challenges and solutions
How to use this chapter
Remote systems
Multiple subnets
Multiple boot servers
Avoiding complex network issues
An Ignite-UX server for each subnet
Using virtual LANs properly for Ignite-UX
Multi-capable server for each subnet
Extend the local subnet
Automating HP-UX OS version selection
Complex network solutions
Limit network boot response by network interface address
Directed boot
Limit network response by system class
Server selection
Install remote clients through a network router
Control network boot via response timing
Having the client contact the correct server
Multiple NICs attach the Ignite server to multiple subnets
Getting the client the correct networking information
Ignite-UX bootp boot helper
Configuring a Next server boot helper for Integrity systems
HP-UX Dhcp PXE Next server boot helper for integrity systems
Forwarding boot requests via bootp relay
Ha=000000000000\ Hm=000000000000\ Bp=10.2.1.11
Non-HP-UX bootp boot helper
Multi-capable subnet boot server
Non-HP-UX Next server boot helper
Complex networks multi-capable servers
Configuring an RDP server for specific MAC addresses
Configuring an RDP server to delay PXE response
Setting up RDP MenuOptions via Windows commands
Configuring an RDP server to initiate HP-UX installation
Setting up RDP MenuOptions via interactive UI
Complex networks multi-capable servers
Configuring an RDP server to initiate HP-UX installation
Client MAC Addr 00 30 6E 4C AA A5
Using an RDP MenuOption for HP-UX
Page
SuSE
FTP Http
RedHat installation from an HP-UX server
Then you must specify the location of Linux install content
Configuring an HP-UX server to support Windows installation
SuSE installation from an HP-UX server
Introducing multipathing
Managing I/O for installation and recovery
Agile view concepts
Agile view I/O addressing logic looks like Figure
Agile multiple path I/O stack addressing model
Practical considerations
System installation configuration
Ignite-UX client installation configuration tabs
Disk Selection Root Disk Dialog Box With Physical Locations
More Info dialog box
Disk selection add/remove disks dialog box
Support for 2 TB boot disk
Identifying devices for other tasks
Important characteristics of the agile view
UNpath Per YH/W evi
Persistent DSFs and device matching
Recovery and the agile view
Legacy DSFs and device matching
Persistent DSF-to-device matching methods by protocol
Controlling the I/O configuration process
O Configuration variables
O Configuration value types
Agile view questions and answers
Agile view questions and answers
Ignite-UX server ports
Security
Port usage initiate LAN boot for Itanium-based clients
Winstallfs
Kernel
Boot
Sequence
Makenetrecovery Initiated from Client
Port usage makenetrecovery initiated from the client
Makesysimage Initiated from Client
Port usage makenetrecovery initiated from the server
Remove or comment-out the following line
Enabling Ignite-UX server requirements
Run Bastille
Enabling Ignite-UX client requirements
Procedure
Configuring Ignite to replace Tftp with NFS
Overview
Ignite Product Files Moved in Version C.7.9 and Later
Set up NFS exports and check custom configuration files
Now use instladm to update the install file system
Use vi to add hploadfileusenfs=true to the file
Would need to be modified to be
Disable Tftp on the Ignite-UX server optional
Where release is the release identifier
Preparing the client for installation
For 64-bit PA-RISC clients the files on the server are
For Itanium-based clients the files on the server are
Boot using the network
Making boot decisions when using the client console
Boot using media
Support?
Using bootsys on the client console
Boot ADMINhelp boot
Booting PA-RISC clients from the console
Booting Itanium-based clients using the network
Enter a brief description for this boot option
Select Add a Boot Option
Enter the data type of this boot option
Press Y to save the new boot option
LAN1
Direct boot profiles for Itanium-based systems
Options and operands
Dbprofile command
Syntax
Lanboot select -od optionaldata -dn name
Lanboot command
Examples
Shell dbprofile or
Shell lanboot or
Installing HP-UX from the client console
User interface and media options
Network Configuration with no Dhcp
Examples
Setting Mixed interface types
Setting 100 Full Duplex
Add this configuration clause to Wviinstallfs
Edit the file
Installation using bootsys
Booting and installing HP-UX on clients using the server
Methods of installing client systems
Touch /.bootsysblock
Prepare the client for installation
Installation using the Ignite-UX GUI
Starting Ignite-UX
Adding clients
Select boot release
Booting a client
Boot process terminal window
Boot confirmation dialog box
New client displayed in GUI
New installation
Configuring the installation
Client installation configuration interface
Initializing the installation
Basic tab
Functions available from all tabs
No environments note
Booting and installing HP-UX on clients using the server
All Legacy HW Paths Dialog Box
File system default choices
Root Swap MB... button
Languages dialog box
Additional Configuration Controls Dialog Box
Additional Configuration Controls Dialog Box Software tab
Software tab for HP-UX 11i v1 and 11i
Marked ? column status can be
Software cannot be unselected
Change Depot Location note
Interactive swinstall notes
System tab
Job? x/s/c
#nslookup test
Set Time Zone dialog box
255.255.248.0 or 0xfffff800 255.255.255.0 or 0xffffff00
Set Root Password dialog box
Network Services tabs
Set DNS Search Domains Dialog Box
NIS tab
Select an Interface card from the selection list
Network Interfaces Dialog Box
Adding or changing a file system configuration
Configuring the installation
To change, add, or remove a disk from the client
Volume requirements for LVM and VxVM
Highlight a disk in the selection list to select it
Advanced Disk Parameters dialog box
Advanced File System Parameters dialog box
No gap is enabled between physical extents within a mirror
Has these characteristics
Volume
Root volume /, the boot volume /stand, dump volumes
For more information, see manageindex1M
Advanced tab
Repeat an installation
Repeat Install dialog box
Executing the installation
Installation Confirmation dialog box
Client Status... dialog box
Viewing and printing a manifest
Installation log file
Printmanifest
Creating a golden image
Golden images
Advantages of golden images
Installing critical patches onto the operating system
Installing the HP-UX operating system
Install the patch non-interactively
Installing optional software
Customizing the system
Creating the golden archive
On the golden system, run
Localedescription
Here are the HP-UX 11i v1 swsource and swsel examples
Creating golden image using GUI
Creating and using golden images using GUI and CLI
Opt/ignite/bin/ignite
Xhost +Ignite-UXserverhostname
Enabling the client
Creation of a golden image using CLI
Examples on using makegoldenimage script
Installing the golden image on the client
Classes of configuration files
Customizing your installation
Using configuration files
These install kernels and install file systems are located
Configuration File Use and Locations
Var/opt/ignite/data/Relrelease
Opt/ignite/data/Relrelease/config
Var/opt/ignite/config.local
Var/opt/ignite/clients/client/config
Combining configuration files using Index entries
Configuration choices dialog box
Defining Disks
Example configuration files
Defining Networking Parameters
Combining Disks to Form a Single Volume Group
Customizations based on the client hardware
Defining an Installation Depot
# ia64
Customizations based on user selection
# ia64 hp workstation zx2000
# 9000/785
Xpatchsavefiles=falsetrue
Avoid archiving patch files
For more information, see instldbg1M
Debugging configuration files
Using post-installation scripts
Example
How the installation functions
Adding a post-installation script
Where t is for postconfigscript selection settings
Using a saved configuration
Automating installations
Starting a non-interactive installation with bootsys
Using the per-client configuration file
Specifying defaults in the config.local file
Setting defaults with instladm
Final systemname=system11 Final ipaddrlan0=10.2.75.193
Press Ctrl-D
Scheduling installations
Setting installation parameters dynamically
Example
Instladm -T -f file
Checking modified files for errors
Why use custom boot and installation media?
Creating your own boot and installation media
Building PA-RISC boot and installation tape
Possible tape contents
Logical interchange format
Possible PA-RISC installation tape layouts
#nfssource=
Archives and depots
Assumptions
PA-RISC installation tape creation example
Sdserver = IPaddress Sddepotdir = /var/tmp/depot
Change the sourcetype attribute from NET to MT
Instladm -d -F /var/tmp/lifvol /var/tmp/cfg
Example PA-RISC installation tape creation
Verify your changes
Instladm -d -f /var/tmp/lifvol
Boot and archive-based CD/DVDs
Creating a boot CD/DVD or an installation DVD
Assumptions
File and ISO image size considerations
Installation archive-based DVD examples
Boot CD/DVD examples
# makemediainstall -?
# makeopticaldiscrecovery -?
Create a recovery DVD
Error messages
Put a PA-RISC HP-UX 11i v2 golden archive on a DVD
No DVD available
Depot-based DVDs
HP-UX 11i v2 Depot-based installation DVDs
No DVD special files
Missing -cargument on HP-UX 11i v2 USB DVD drive
Create the first DVD
For more information, see instladm1M and instladm4
Copy the EFI partition into the first DVD pseudo-root
Run mkisofs to create the first DVD image pathtodvd1image
Create the second DVD
HP-UX 11i v3 Depot-based installation DVDs
Run mkisofs to create the second DVD image pathtodvd2image
Burn the DVD images and test them
Overview
Recovery
System recovery
Recovery tool comparison
System recovery tools
Use maketaperecovery to
Use makenetrecovery to
Recovery image contents
Recovery image configuration policies
Create files and directories for the recovery image
Recovery image creation process
Var/opt/ignite/clients/client/recovery/2005-03-17,1119
Var/opt/ignite/recovery/archives/client directory
Var/opt/ignite/clients/client/recovery/defaults
Run the recovery interface
Var/opt/ignite/clients/client/recovery directory
Prepare the configuration file
Examining recovery image contents
Recovery image creation status
Opt/ignite/lbin/listexpander -f archivecontent
Init hpignoreswimpact=1
Verifying recovery image results
Recovery
Opt/ignite/recovery/mnressentials
Creating and using recovery tapes
Recovery tape creation examples
Recovering a minimal operating system
Tape recovery for PA-RISC systems
Maketaperecovery -x incentire=vg00
Maketaperecovery -A -s myserver -a /dev/rmt/0m
Determining the tape drive’s EFI path
Tape recovery for Itanium-based systems
Select Boot Configuration from the Boot Menu
EFI menu with timer
Add boot entry
Boot configuration
List of selectable boot devices
Enter load options
Boot Manager menu with the new option
Tape recovery for Integrity Blade systems
Shell tapeboot select Fibre-Channel
Creating and using network recovery images
Determine tape drive EFI path using Command Line Interface
Networking features
Network recovery server dependency
Adding clients for recovery
Var/opt/ignite/recovery/datetime/recovery.log
Xhost +Ignite-UXserverhostname
Recovering using the network for PA-RISC clients
Examples of network recovery image creation
Makenetrecovery -s myserver
Makenetrecovery -s myserver -x incentire=vg00
Recovering using the network for Itanium-based clients
Hpux
Retaining recovery images
# rm latest # ln -s RecoveryArchive.sav latest
Using the recovery config.local file
Making recovery configuration file additions
Var/opt/ignite/clients/client/recovery/config.local
Var/opt/ignite/recovery/config.local
Opt/ignite/data/RelB.11.11/config
Selecting file systems during recovery
CD/DVD
Using the makesysimage method
Run # shareall -F nfs
Cloning a system using makenetrecovery
Question
System recovery questions and answers
Check /etc/inetd.conf
# rm oldhostname
Related information
Support and other resources
Contacting HP
Websites
Typographic Conventions
Typographic conventions
Following conventions are used in this document
Documentation feedback
Errors and warnings
Troubleshooting
Ignite-UX server problems
Installing systems with Ignite-UX
Debugging SD during cold-installation
Problem installing clients on multiple subnets
Too much file space needed
Ignite-UX requests more file system space than expected
Corrupted /opt/ignite/boot/bootlif file
Booting errors on PA-RISC systems
Applications hang after igniting
Problems pointing to client over network
Received n bytes in s seconds
Tftp quit
Server not listed
Bootsys Command Seems to Work in Reverse
Installing from golden images
Installing from media
File size miscalculated
Common network booting errors
Insufficient Response to PXE Boot Request
File Size miscalculated on HP Integrity virtual machines
Creation of archive
Overview of Dhcp services
Configuring Dhcp services
Dhcp usage examples
Background information on Dhcp design
Using bootptab as an alternative to Dhcp
LIF volume contents
For more information, see Classes of configuration files
For more information, see Using configuration files
Description of the files in the LIF volume
Using Integrated Lights Out Virtual Media with Ignite-UX
243
Using Integrated Lights Out Virtual Media with Ignite-UX
245
Using Integrated Lights Out Virtual Media with Ignite-UX
247
Using vMedia with DVD installation media and ISO images
Expert recovery procedure
Expert recovery
Expert recovery preparation
Expert recovery
Expert recovery procedure
Expert recovery
Expert recovery procedure
# mknod /ROOT/dev/console c 0
Basic keyboard shortcuts
Terminal keyboard shortcuts
Advanced keyboard navigation
HP terminals
Function keys
Vt100 terminals
Advanced keyboard actions
See Link Level Address LLA
Glossary
Checknetrecovery1M
Maketaperecovery. See copyboottape1M
Iinstall
See instlcombine1M
Makebundles1M
Maketapenetrecovery
See Software Distributor
Vinstall
Index
Setting hplanadminargs, 108 boot source
Index
DVD
Index
LVM
PXE
Port usage on makenetrecovery, 89 port usage with bootsys
Page
Server display Xntp configuring, 136 screen Xntpd daemon