Indicates that the IP and MAC address of this entry is already bound.
To bind the entries in the list, check these entries and click the <Import> button, then the settings will take effect if the entries do not conflict with the existed entries.
![]() Note:
Note:
If the local hosts suffered from ARP attack, you cannot add
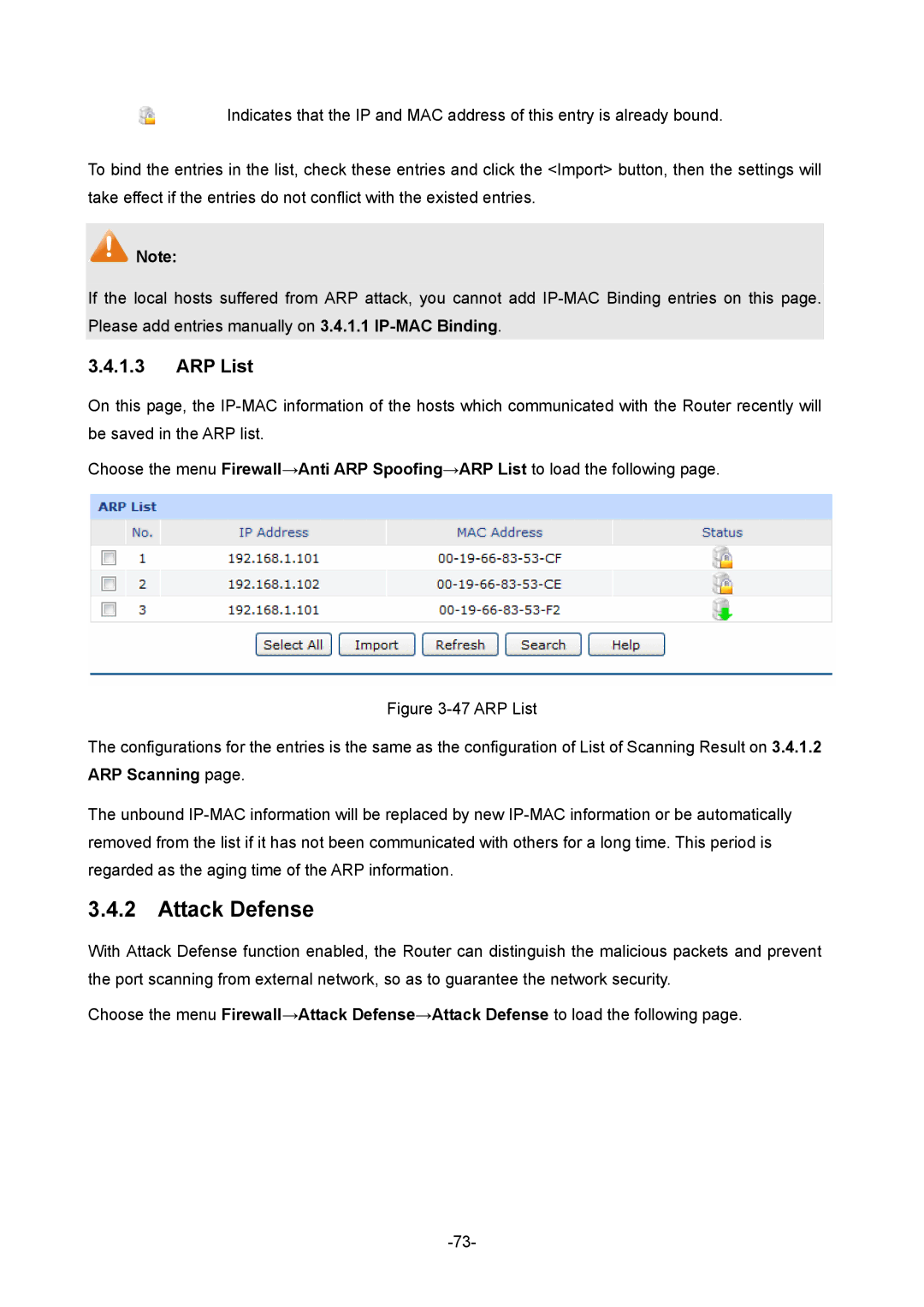
3.4.1.3ARP List
On this page, the
Choose the menu Firewall→Anti ARP Spoofing→ARP List to load the following page.
Figure 3-47 ARP List
The configurations for the entries is the same as the configuration of List of Scanning Result on 3.4.1.2 ARP Scanning page.
The unbound IP-MAC information will be replaced by new IP-MAC information or be automatically removed from the list if it has not been communicated with others for a long time. This period is regarded as the aging time of the ARP information.
3.4.2 Attack Defense
With Attack Defense function enabled, the Router can distinguish the malicious packets and prevent the port scanning from external network, so as to guarantee the network security.
Choose the menu Firewall→Attack Defense→Attack Defense to load the following page.