Identifying authentication requirements
Acloser look at CA-based certificates
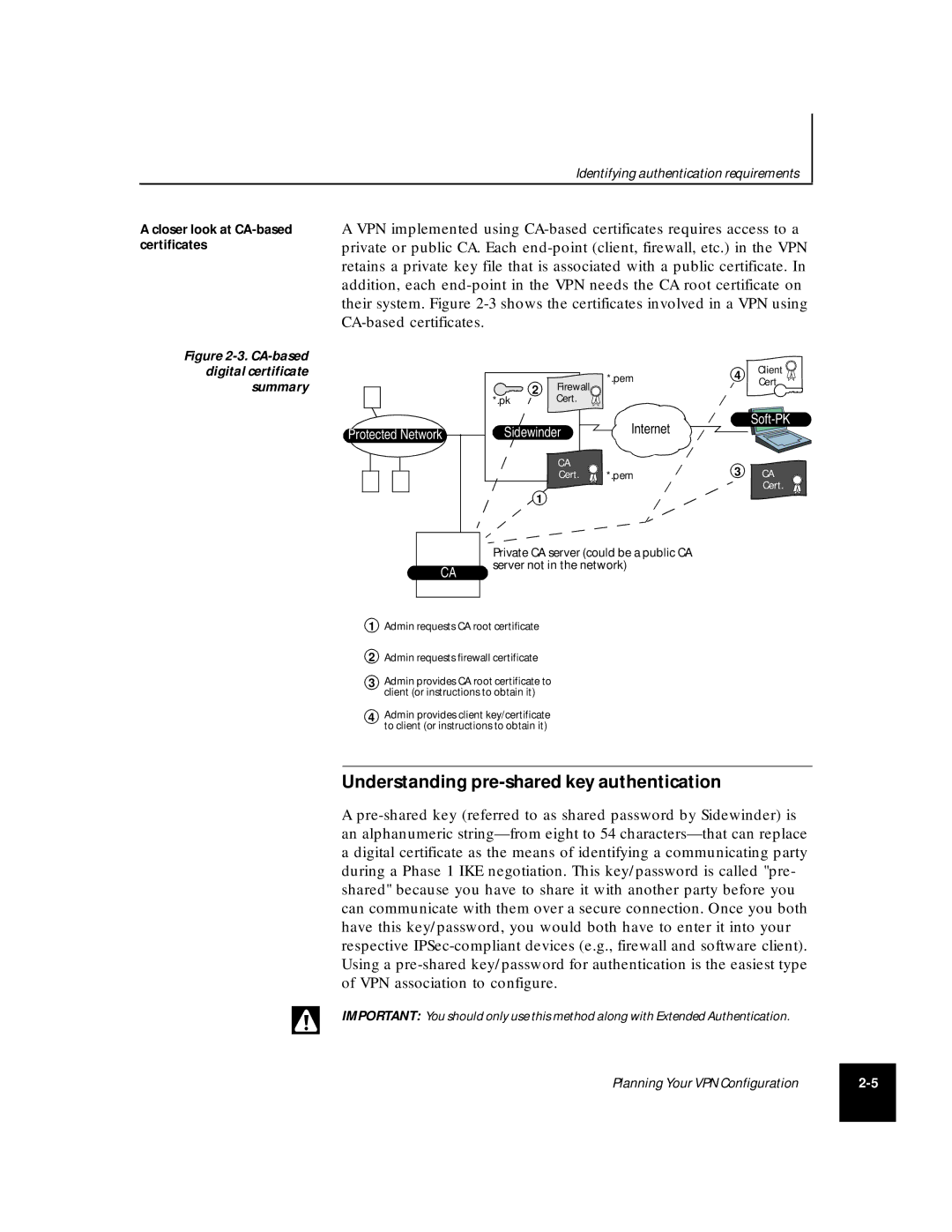
A VPN implemented using
Figure 2-3. CA-based digital certificate summary
Protected Network
|
| *.pem | 4 | Client | |
2 | Firewall | Cert. | |||
|
| ||||
|
|
| |||
*.pk | Cert. |
|
|
| |
Sidewinder | Internet |
|
| ||
|
| ||||
| CA |
| 3 | CA | |
| Cert. | *.pem | |||
|
|
|
| Cert. | |
1 |
|
|
|
| |
CA
Private CA server (could be a public CA server not in the network)
1Admin requests CA root certificate
2Admin requests firewall certificate
3Admin provides CA root certificate to client (or instructions to obtain it)
4Admin provides client key/certificate to client (or instructions to obtain it)
Understanding pre-shared key authentication
A
IMPORTANT: You should only use this method along with Extended Authentication.
Planning Your VPN Configuration | |
|
|