Fortinet 222 FortiWeb 5.0 Patch 6 Administration Guide
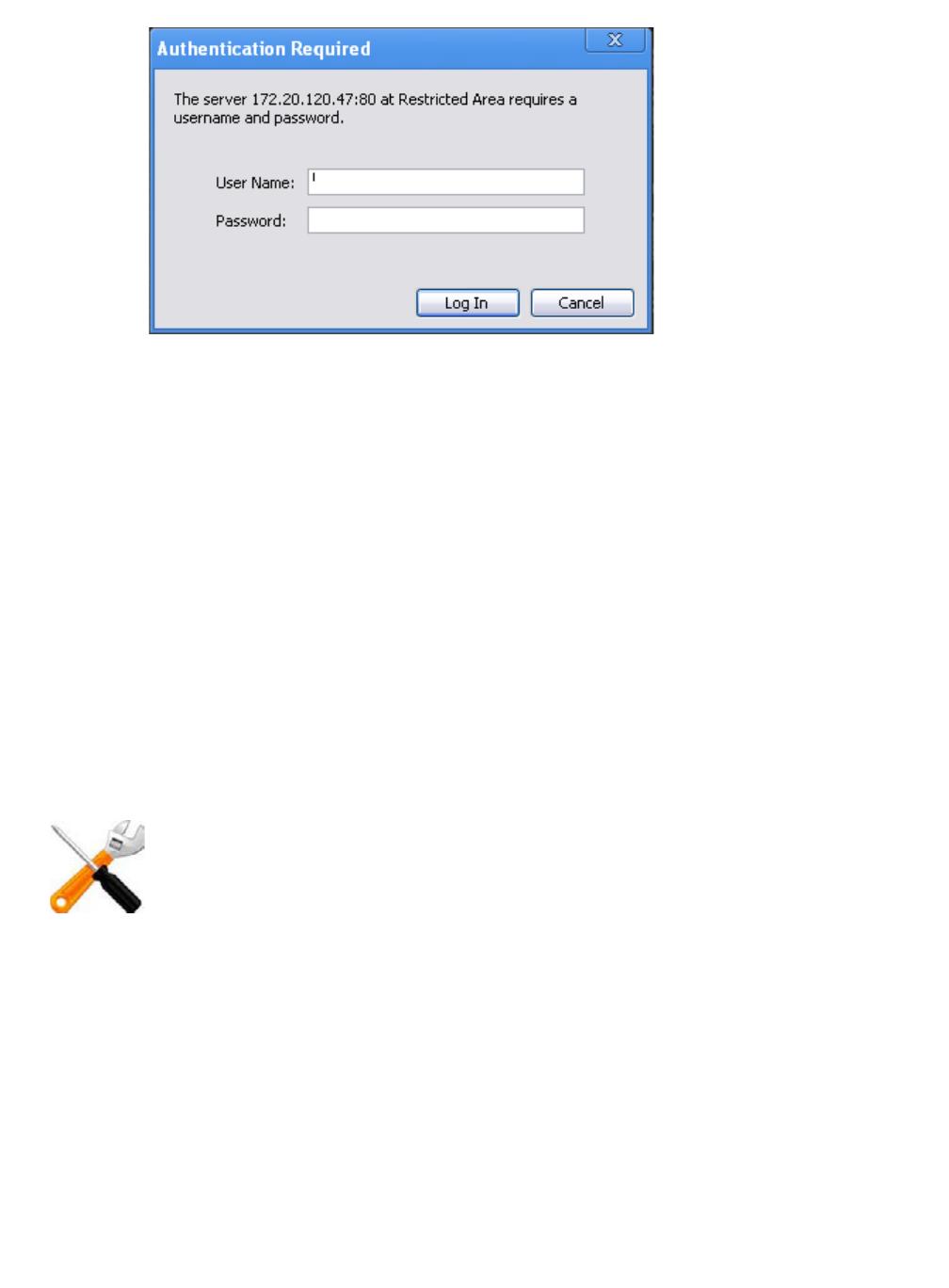
Figure 32:An HTTP authentication prompt in the Google Chrome browser
If the user supplies credentials, his or her web browser includes them in a second request for
the same page. If the credentials are valid, the web server returns the requested URL;
otherwise, it repeats its 401 Authorization Required response.
This type of authorization is handled at the web server layer of the host’s software stack,
independently of the static HTML, dynamic pages and runtime interpreters (PHP, ColdFusion,
Python, etc.), or database (MySQL, PostgreSQL, etc.) of the web applications it may host, and
as a result can span multiple web applications. It also may be offloaded to a FortiWeb (see
“Offloading HTTP authentication & authorization” on page 225).
Because the HTTP protocol itself is essentially stateless — no request is required to have
knowledge of or be related to any other request — as a practical matter, many browsers cache
this data so that users will not have to re-enter the same user name and password over and
over again, for every page that they visit on the web site. (For this reason, one-time passwords
are generally impractical. They effectively contradict the reusability of the cache.) However, in
payment for this initial convenience, logouts are basically impossible unless the user clears his
or her browser’s cache and/or closes the window (which can also clear the cache).
Accounting, if any, of this type of authentication is handled by the web server (or, if you have
offloaded authentication to FortiWeb, it may be accounted for in logs, depending on your
configuration of Alert Type).
Via forms embedded in the HTMLWeb applications can authenticate users by including <input> tags for each login credential in
an <form> buttons, text fields, check boxes, and other inputs on a web application’s login page
such as /login.asp.
While some supported WWW-Authenticate: methods encrypt passwords, due to a lack of
other cryptographic features, if used with HTTP, it is not as secure as HTTPS. For stronger
protection, use HTTP-based authentication with HTTPS.