Draft Document for Review November 15, 2007 3:27 pm | 4372ch04.fm |
the other options is selected, the user is requested to provide a password. If the password is correct, the operating system partition is redeployed, and the user data on the second partition will not be touched.
4.2.3 Process for local redeployment
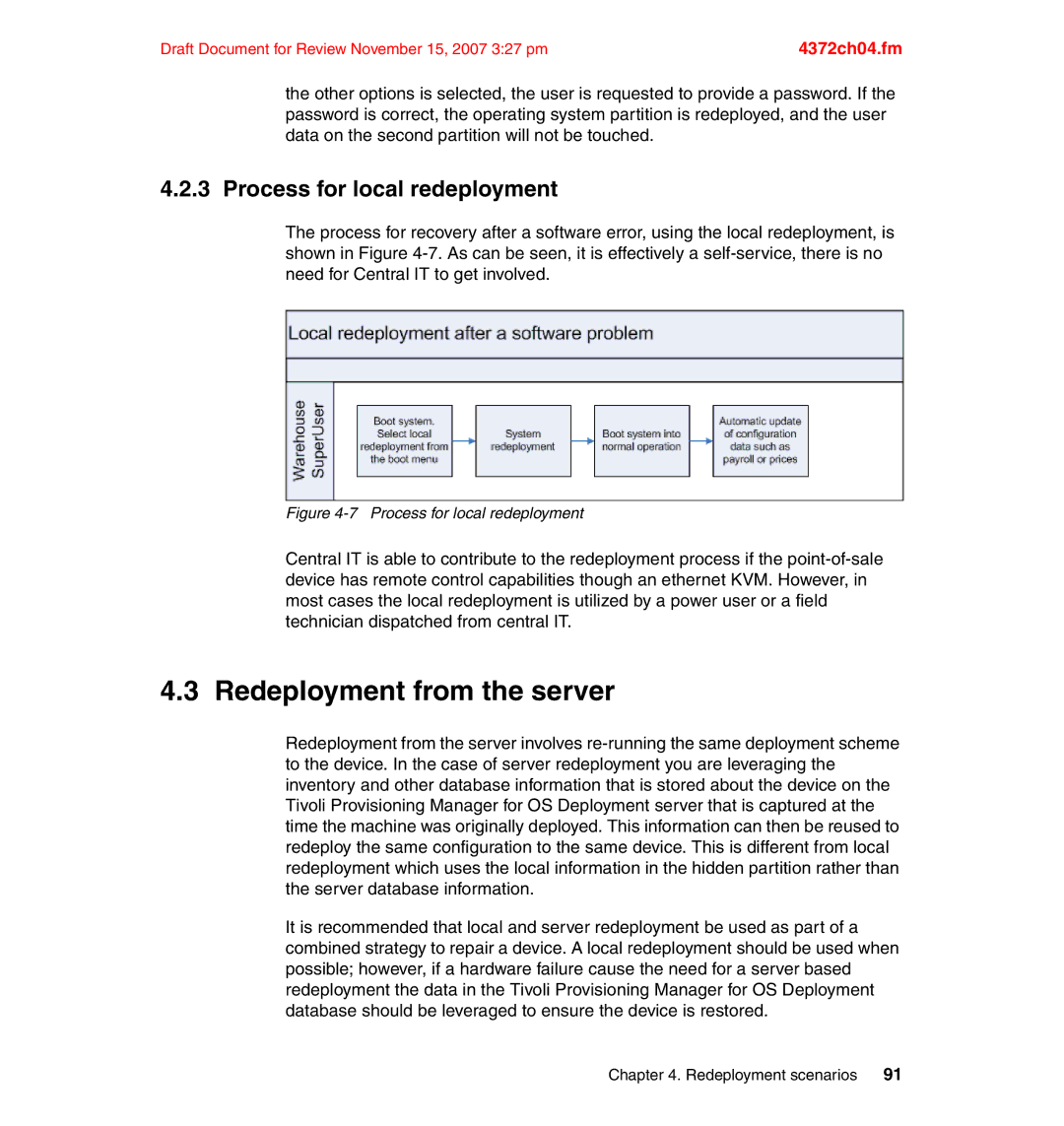
The process for recovery after a software error, using the local redeployment, is shown in Figure
Figure 4-7 Process for local redeployment
Central IT is able to contribute to the redeployment process if the
4.3 Redeployment from the server
Redeployment from the server involves
It is recommended that local and server redeployment be used as part of a combined strategy to repair a device. A local redeployment should be used when possible; however, if a hardware failure cause the need for a server based redeployment the data in the Tivoli Provisioning Manager for OS Deployment database should be leveraged to ensure the device is restored.
Chapter 4. Redeployment scenarios | 91 |