|
| 7: Network, Line, Tunnel, and Terminal Settings |
|
|
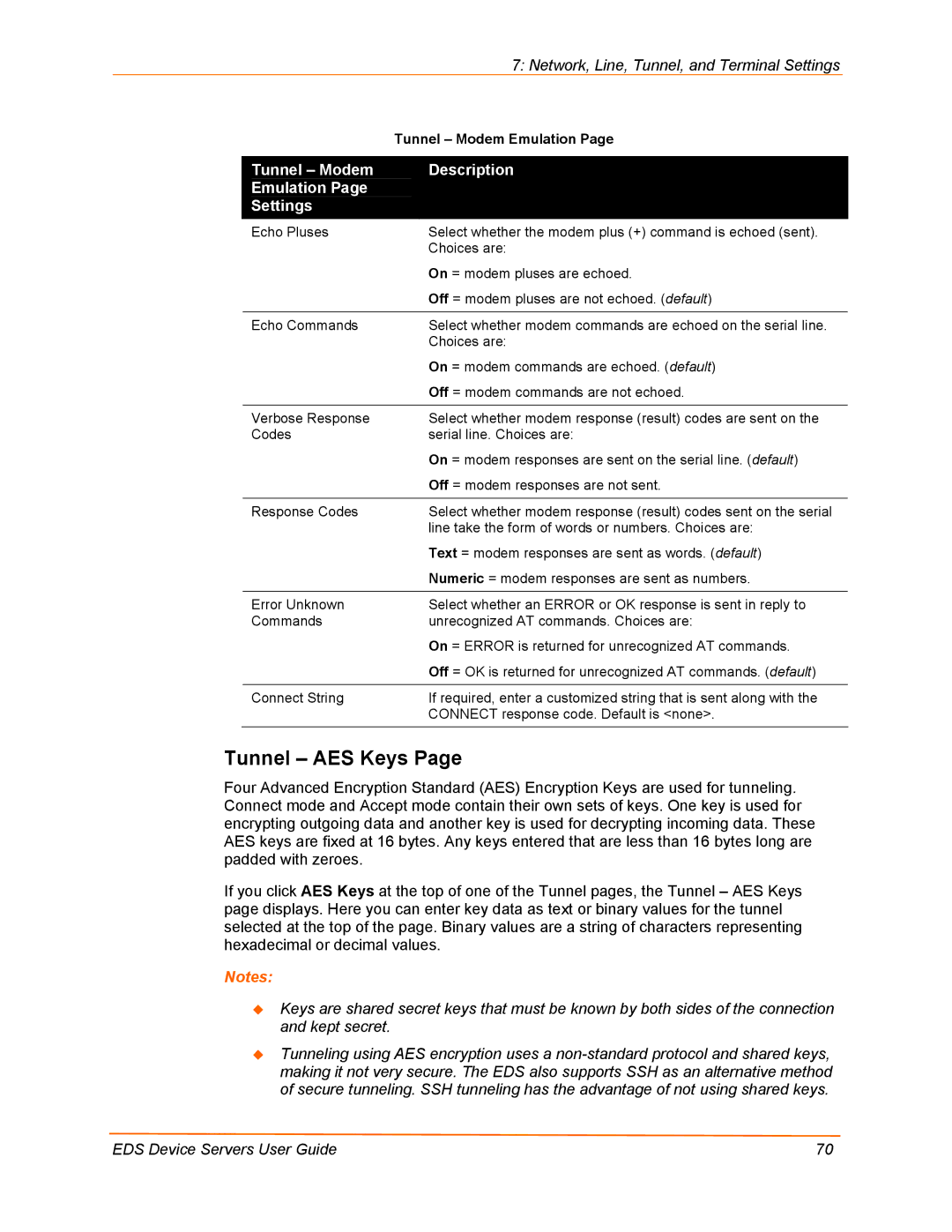
| Tunnel – Modem Emulation Page |
|
|
|
|
|
| Tunnel – Modem | Description |
|
| Emulation Page |
|
|
| Settings |
|
|
| Echo Pluses | Select whether the modem plus (+) command is echoed (sent). |
|
|
| Choices are: |
|
|
| On = modem pluses are echoed. |
|
|
| Off = modem pluses are not echoed. (default) |
|
|
|
|
|
| Echo Commands | Select whether modem commands are echoed on the serial line. |
|
|
| Choices are: |
|
|
| On = modem commands are echoed. (default) |
|
|
| Off = modem commands are not echoed. |
|
|
|
|
|
| Verbose Response | Select whether modem response (result) codes are sent on the |
|
| Codes | serial line. Choices are: |
|
|
| On = modem responses are sent on the serial line. (default) |
|
|
| Off = modem responses are not sent. |
|
|
|
|
|
| Response Codes | Select whether modem response (result) codes sent on the serial |
|
|
| line take the form of words or numbers. Choices are: |
|
|
| Text = modem responses are sent as words. (default) |
|
|
| Numeric = modem responses are sent as numbers. |
|
|
|
|
|
| Error Unknown | Select whether an ERROR or OK response is sent in reply to |
|
| Commands | unrecognized AT commands. Choices are: |
|
|
| On = ERROR is returned for unrecognized AT commands. |
|
|
| Off = OK is returned for unrecognized AT commands. (default) |
|
|
|
|
|
| Connect String | If required, enter a customized string that is sent along with the |
|
|
| CONNECT response code. Default is <none>. |
|
|
|
|
|
Tunnel – AES Keys Page
Four Advanced Encryption Standard (AES) Encryption Keys are used for tunneling. Connect mode and Accept mode contain their own sets of keys. One key is used for encrypting outgoing data and another key is used for decrypting incoming data. These AES keys are fixed at 16 bytes. Any keys entered that are less than 16 bytes long are padded with zeroes.
If you click AES Keys at the top of one of the Tunnel pages, the Tunnel – AES Keys page displays. Here you can enter key data as text or binary values for the tunnel selected at the top of the page. Binary values are a string of characters representing hexadecimal or decimal values.
Notes:
Keys are shared secret keys that must be known by both sides of the connection and kept secret.
Tunneling using AES encryption uses a
EDS Device Servers User Guide | 70 |