10/100/1000 4-Port VPN Router
Domain Name (FQDN) (Fully Qualified Domain Name): Enter the Domain Name of the Remote Client. When the Remote Client requests to create a tunnel with the Router, the Router will act as a responder. The Domain Name must match the local settings of the Remote Client.
Microsoft XP/2000 VPN Client: This option is used for Dynamic IP users (e.g. PPPoE or DHCP) which using Microsoft VPN client. The difference between Microsoft and other VPN client is that Microsoft client does not support Aggressive mode and FQDN/USER FQDN ID options.
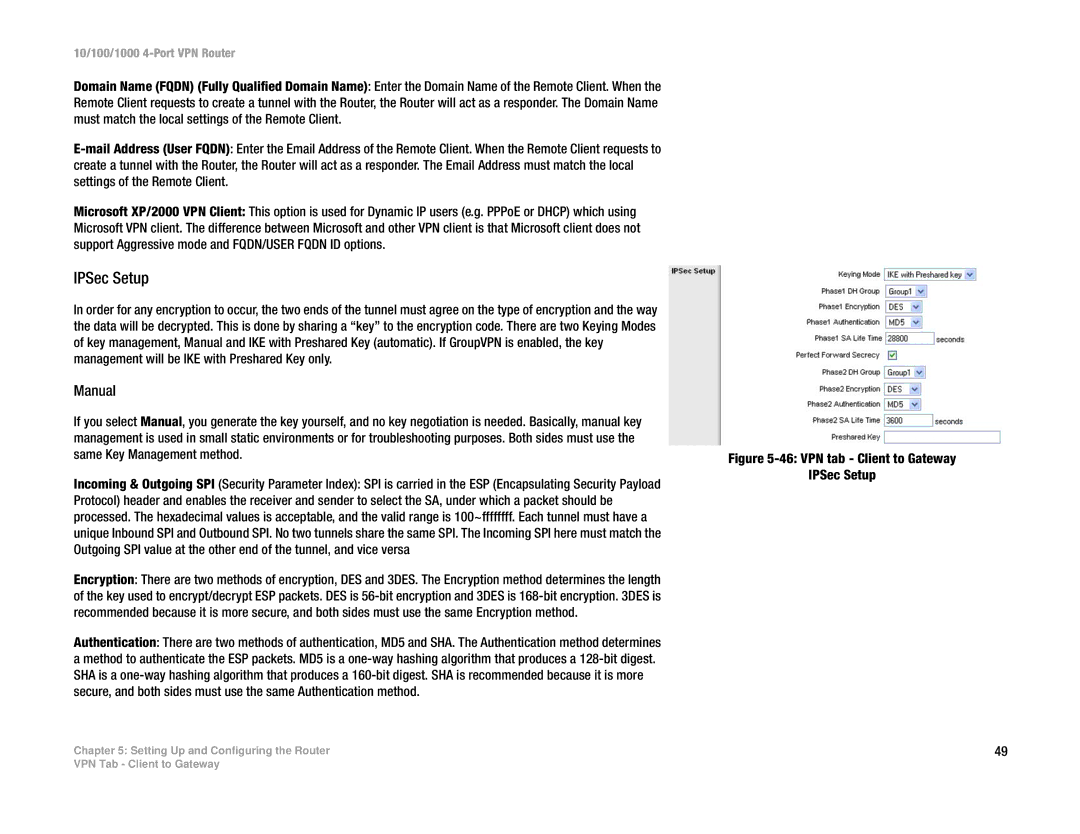
IPSec Setup
In order for any encryption to occur, the two ends of the tunnel must agree on the type of encryption and the way the data will be decrypted. This is done by sharing a “key” to the encryption code. There are two Keying Modes of key management, Manual and IKE with Preshared Key (automatic). If GroupVPN is enabled, the key management will be IKE with Preshared Key only.
Manual
If you select Manual, you generate the key yourself, and no key negotiation is needed. Basically, manual key management is used in small static environments or for troubleshooting purposes. Both sides must use the same Key Management method.
Incoming & Outgoing SPI (Security Parameter Index): SPI is carried in the ESP (Encapsulating Security Payload Protocol) header and enables the receiver and sender to select the SA, under which a packet should be processed. The hexadecimal values is acceptable, and the valid range is 100~ffffffff. Each tunnel must have a unique Inbound SPI and Outbound SPI. No two tunnels share the same SPI. The Incoming SPI here must match the Outgoing SPI value at the other end of the tunnel, and vice versa
Encryption: There are two methods of encryption, DES and 3DES. The Encryption method determines the length of the key used to encrypt/decrypt ESP packets. DES is
Authentication: There are two methods of authentication, MD5 and SHA. The Authentication method determines a method to authenticate the ESP packets. MD5 is a
Chapter 5: Setting Up and Configuring the Router
Figure 5-46: VPN tab - Client to Gateway
IPSec Setup
49
VPN Tab - Client to Gateway