Page
February
Table of Contents
Getting Started with the Configuration Manager
Configuring the LAN Ports
Configuring Dynamic Host Configuration Protocol
Configuring Network Address Translation
Configuring DNS Server Addresses
Configuring IP Routes
Configuring the Routing Information Protocol
Configuring the ATM Virtual Circuit
Configuring PPP Interfaces
Configuring EOA Interfaces
Configuring IPoA Interfaces
Configuring Bridging
Viewing DSL Line Information Administrative Tasks
Appendix a
Appendix B
Features
Introduction
Using this Document
System Requirements
Introduction
Notational conventions
Using this Document
Typographical conventions
Special messages
Package Contents
Getting to Know Adsl Barricade
Hardware Description
Getting to Know the Adsl Barricade
Front Panel
Rear Panel
Connecting the Hardware
Quick Start
Quick Start
Connect the Adsl cable
Configuring Your Computers
Attach the power connector
Power up your systems
Connect the Ethernet cable
Windows XP
Windows
Windows Me
Windows 95
Quick Start
Windows NT
Assigning static Internet Information to your PCs
Configuring the Adsl Barricade
Configuring the Adsl Barricade
Logging into the Adsl Barricade Quick Configuration
With your ISP
Path that your connection uses to communicate with your ISP
Configuration of your device
Password
You have used to log in to Configuration Manager
Bridge
Default Router Settings
Addresses
Internet. See Configuring
Description of the NAT service
LAN Ports on page 33 for a
Getting Started with the Configuration Manager
Accessing the Configuration Manager
Getting Started with the Configuration Manager
Login Screen
Functional Layout
Functional Layout
Commonly used buttons
Browser window. Help is available from any main topic
Home Page and System View Table
System View Table
Home Page and System View Table
Modifying Basic System Information
Modifying Basic System Information
Time Zone
Daylight
Committing Changes and Rebooting
Committing your changes
Committing Changes and Rebooting
Rebooting the device using Configuration Manager
Reboot from Last
Configuration
Just committed
Session
Configuring
Connecting via Ethernet
Configuring the LAN Port IP Address
Configuring the LAN Ports
LAN Configuration
Configuring the LAN Port IP Address
Configuring the LAN Ports
Configuring the LAN Port IP Address
Viewing System IP Addresses and IP Performance Statistics
Viewing the Adsl Barricades IP Addresses
Viewing System IP Addresses and IP Performance Statistics
Viewing IP Performance Statistics
Viewing IP Performance Statistics
Configuring Dynamic Host Configuration Protocol
What is DHCP?
Overview of Dhcp
Configuring Dynamic Host Configuration Protocol
Why use DHCP?
Adsl Barricade Dhcp modes
Configuring Dhcp Server
Configuring Dhcp Server
Guidelines for creating Dhcp server address pools
Configuring Dynamic Host Configuration Protocol
Adding Dhcp Server Address Pools
Start IP Address
End IP Address
For distribution to your LAN computers
Mac Address
As explained on
Domain Name
Addresses in this pool. This is used for reference only
Gateway
Viewing, modifying, and deleting address pools
Dhcp Server Pool Modify
Excluding IP addresses from a pool
Viewing current Dhcp address assignments
Configuring Dhcp Relay
Netmask
These terms
Mac
Configuring Dhcp Relay
Dynamic Host Configuration Protocol Dhcp Relay Configuration
Setting the Dhcp Mode
Dynamic Host Configuration Protocol Dhcp
Setting the Dhcp Mode
Configuring Network Address Translation
Overview of NAT
Configuring Network Address Translation
Viewing NAT Global Settings and Statistics
Viewing NAT Global Settings and Statistics
TCP Def Timeout
Active state, where the connection is being used to
Time specified in TCP Idle Timeout
When in the establishing state, the session will timeout
NAT Rule Global Statistics
Network Address Translation NAT Rule Configuration
Viewing NAT Rules and Rule Statistics
Viewing Current NAT Translations
Viewing Current NAT Translations
Is enabled
Was invoked from the rule definition
Protocol
TCP, UDP, Icmp
Out Ports
Translated
Ports Number was translated
Adding NAT Rules
Adding NAT Rules
NAT Rule-Add Page Napt Flavor
RDR rule Allowing external access to a LAN computer
NAT Rule Add Page RDR Flavor
Configuring Network Address Translation
Adding NAT Rules
Basic rule Performing 11 translations
NAT Rule Add Page Basic Flavor
Adding NAT Rules
NAT Rule Add Page Filter Flavor
Adding NAT Rules
Bimap rule Performing two-way translations
NAT Rule Add Page Bimap Flavor
NAT Rule Add Page Pass Flavor
Adding NAT Rules
Configuring DNS Server Addresses
About DNS
Assigning DNS Addresses
Configuring DNS Relay
Configuring DNS Server Addresses
Configuring DNS Relay
Domain Name Service DNS Configuration
Configuring IP Routes
IP routing versus telephone switching
Overview of IP Routes
Configuring IP Routes
Hops and gateways
Using IP routes to define default gateways
Overview of IP Routes
Do I need to define IP routes?
Viewing the IP Routing Table
IP Route Table
Viewing the IP Routing Table
Adding IP Routes
IP Route-Add
Adding IP Routes
Configuring the Routing Information Protocol
RIP Overview
Configuring the Adsl Barricades Interfaces with RIP
Configuring the Routing Information Protocol
When should you configure RIP?
Configuring the Adsl Barricades Interfaces with RIP
Routing Information Protocol RIP Configuration
Configuring the Routing Information Protocol
Configuring the Adsl Barricades Interfaces with RIP
Viewing RIP Statistics
RIP Global Statistics
Configuring the ATM Virtual Circuit
Viewing Your ATM VC
Configuring the ATM Virtual Circuit
Software and identify the type of traffic that can be
Use an aal5-type interface
Vpi
Adding ATM VCs
Adding ATM VCs
Modifying ATM VCs
Modifying ATM VCs
ATM VC Interface Modify
Configuring PPP Interfaces
Viewing Your Current PPP Configuration
Configuring PPP Interfaces
Inactivity TimeOut mins
Ignore WAN to LAN traffic while monitoring inactivity
Viewing Your Current PPP Configuration
Disable, LAN hosts will use the DNS address
Preconfigured in the Dhcp pool see Configuring
Under way e.g., password authorization or
Device will acquire IP addresses for other
Viewing PPP Interface Details
Viewing PPP Interface Details
Enabled
Rebooted
Service Name
Each requiring a different login and other
By changing the Configuration Manager settings
With the timeout period specified on the PPP
On the user name and/or password provided
ISP issued a special packet type to terminate
Adding a PPP Interface Definition
PPP Interface Add
Modifying and Deleting PPP Interfaces
Modifying and Deleting PPP Interfaces
114
Configuring EOA Interfaces
Overview of EOA
Viewing Your EOA Setup
Configuring EOA Interfaces
Viewing Your EOA Setup
Default Route
Enable or disable the interface a red ball may indicate a
Problem with the DSL connection
Adding EOA Interfaces
Adding EOA Interfaces
EOA Interface Add
120
Configuring Ipoa Interfaces
Viewing Your IPoA Interface Setup
Configuring IPoA Interfaces
Enable or disable the interface a down interface may
Indicate a problem with the DSL connection
Adding IPoA Interfaces
Adding IPoA Interfaces
124
Configuring Bridging
Overview of Bridges
Configuring Bridging
When to Use the Bridging Feature
When to Use the Bridging Feature
Defining Bridge Interfaces
128
Deleting a Bridge Interface
Deleting a Bridge Interface
Configuring Firewall Settings
Configuring Global Firewall Settings
Configuring Firewall Settings
Configuring Global Firewall Settings
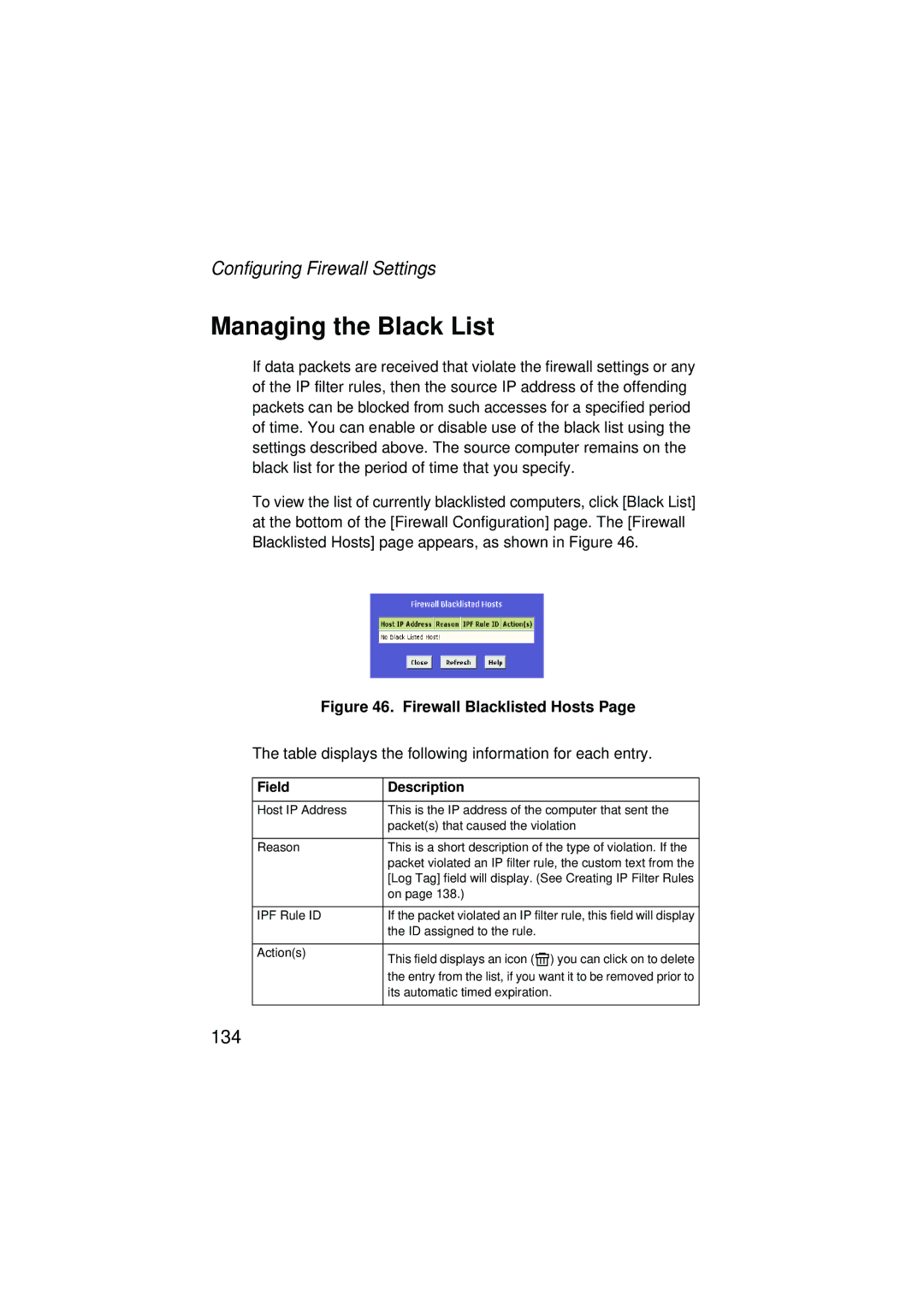
Managing the Black List
ID assigned to the rule
Its automatic timed expiration
Configuring IP Filters and Blocked Protocols
Configuring IP Filters
Configuring IP Filters and Blocked Protocols
Viewing Your IP Filter Configuration
Configuring IP Filters
Configuring IP Filter Global Settings
Creating IP Filter Rules
External computers from accessing your LAN
That are incoming or outgoing on the selected interface
Incoming refers to packets coming from the LAN
Outgoing refers to packets going to the Internet
Choosing the appropriate interface for various rule types
Option is valid only for the outgoing direction
Log Option to Enable if you configure a Log Tag
Security
Low, then the rule will be inactive
Blacklist
Rule to be invoked on packets containing
Any any source IP address
Lt any source IP address that is numerically less than
Specified address
Unwelcome attempt to gain access to a network
Store State
An ongoing communication, etc. This option provides
Received in the anticipated state. Such packets can signify
That have options specified in their packet headers
IP filter rule examples
Example
146
Viewing IP Filter Statistics
Managing Current IP Filter Sessions
IP Filter Rule Statistics
Blocked Protocols
Blocked Protocols
Filter rule, are assigned a session index
Time to expire
150
Address Resolution Protocol. Computers on a LAN use ARP to
Computers when they only know their IP addresses
Your ISP before blocking this protocol
Is often used for handling e-mail, mailing lists
Large networks
Viewing DSL Line Information
DSL Status
Viewing DSL Line Information
DSL Parameter
155
156
Administrative Tasks
Configuring User Names and Passwords
Changing Login Passwords
Administrative Tasks
User Configuration
Viewing System Alarms
Viewing System Alarms
Viewing the Alarm Table
Image Upgrade
Upgrading the Software
Using Diagnostics
Using Diagnostics
File
162
Modifying Port Settings
Modifying Port Settings
Overview of IP port numbers
Modifying the Adsl Barricade’s port numbers
165
Appendix a
IP Addresses
Structure of an IP address
Appendix a
Network ID Host ID
Network classes
Network classes
Subnet masks
Subnet masks
Appendix B
Binary Numbers
Definition binary numbers
Appendix B
Bits and bytes
Definition bit and byte
Troubleshooting
Troubleshooting
Internet Access My PC cannot access Internet
My LAN PCs cannot display web pages on the Internet
My changes to Configuration Manager are not being retained
Diagnosing Problem using IP Utilities
179
180
Technical Specifications
Technical Specifications
Chap
Power Dissipation
Operating System Support
Environmental Operating Range
Power Input
Weight
Dimensions
Safety
Authenticate
Terminology
Analog
Terminology
Digital
Domain name
Download
Ethernet
Filtering
Firewall
Gbps
Hop
Hop count
Host
In-line filter
Internet
Intranet
191
Mask
Mbps
Microfilter
NAT rule
Network mask
Packet
Port
Pots splitter
Protocol
Remote
Routing
Rule
Splitter
Splitterless
Subnet
Subnet mask
Telnet
Twisted pair
Upstream
Web browser
Web
Web site
Compliances
FCC Class B
FCC Part
Compliances
EC Conformance Declaration Class B
Safety Compliance
Wichtige Sicherheitshinweise Germany
Compliances
SMCs Limited Warranty Statement
Legal Information Contacts
Legal Information and Contacts
Limitation of Liability
Is subject to change without notice