HP Remote Insight Lights-Out Edition II User Guide
Audience assumptions
Contents
Directory services
Riloe II security
Systems Insight Manager integration
Scripting, command line, and utility options 110
Directory-enabled remote management 103
Troubleshooting the Riloe 173
Technical support 194
Directory Services schema 187
Regulatory compliance notices 195
Acronyms and abbreviations 199 Index 202
Riloe II kit contents
Operational overview
New in this release
Virtual Power Button cable 4-pin
Preparing to install Riloe
Installing the Riloe
Keyboard/mouse adapter cable configuration
Remote Insight cable configuration
Installing Riloe II in the server
Installing Internal Cables
Installing a Virtual Power Button cable 4-pin
Connecting external cables to Riloe
Installing a Remote Insight cable 16-pin
Installing a Remote Insight cable 30-pin
Keyboard/mouse adapter cable connection
Monitor cable connection
Headless server deployment
LAN cable connection
AC power adapter connection
Powering up the server
Configuration options
Configuring the Riloe
Remote setup
ROM-Based Setup Utility F8
SmartStart setup of Riloe
Installing Riloe II device drivers
Microsoft device driver support
Novell NetWare device driver support
Linux device driver support
Disabling DNS/DHCP
Configuring the Riloe II
Accessing Riloe II for the first time
Using the Riloe
Using the Riloe II
Features of the Riloe
Managing the user and configuration settings of the Riloe
User configurations and settings
Click Restore User Information
Click User Settings on the Administration tab
Adding authorized users
Modifying an existing users profile
Click Network Settings in the Administration tab
Network settings
Parameter Default value Definition
Administration Click Global Settings
Global settings
External power connector to the operating system agent
Riloe
Snmp alerts and settings
Snmp Pass-through Status
Click Apply Snmp Settings
Generating Test Alerts
Disabling Alerts
Two-Factor Authentication Settings
Riloe II firmware updates
Security Settings
Using the Remote Console
Remote Console Information Option
Using Enhanced Features of the Remote Console
Local Cursor
Refresh
Remote Console Linux settings
Recommended client settings
Recommended server settings
Microsoft Windows 2000 settings
Microsoft Windows NT 4.0 and Windows 2000 settings
Microsoft Windows Server 2003 settings
Red Hat Linux and Suse Linux server settings
Novell NetWare settings
Supported hot keys
Video replays of previous server Reset Sequences
Click Reset Sequences on the Remote Console tab
Windows EMS console
Terminal Services Client requirements
Terminal Services pass-through option
Windows RDP Pass-Through service
Terminal Services pass-through installation
Windows 2000 Terminal Services port change
Terminal Services Pass-Through status
Enabling the Terminal Services Pass-Through option
Terminal Services warning message
FileImport
Troubleshooting Terminal Services
Remote Console and Terminal Services clients
Terminal Services button display
ComputerPropertiesRemoteRemote Desktop
ManagementSystem ToolsEvent ViewerApplication
Using virtual devices
Virtual media
Virtual power
Riloe II Virtual Floppy
Select Local Media Drive
Click Connect
MS-DOS
Virtual Floppy operating systems notes
Virtual Floppy screen
Mounting USB Virtual Media Floppy in Linux
Uploading a diskette image to the remote server
Submit Changes
Changing Virtual Floppy drive settings
Diskette Image Utility
Copying files on the host server to the Virtual Floppy drive
Using the Riloe II
Using the Riloe II
Select Local CD-ROM Drive
Riloe II Virtual CD-ROM
Virtual Media CD-ROM operating system notes
Creating Riloe II disk image files
Mounting USB Virtual Media CD-ROM in Linux
Click Create Disk Image
Virtual Media applet timeout
Resetting the Riloe II to the factory default settings
Cancel
Riloe II Virtual Media privilege
Getting help
Pocket PC access with Riloe
Using the Riloe II
Using the Riloe II
Using the Riloe II
Riloe II security
Password guidelines
General security guidelines
Encryption
Setting up two-factor authentication for the first time
Two-factor authentication
Setting up local user accounts
Click View/Modify Click Add a certificate
Two-factor authentication user certificates
Setting up directory user accounts
Click View/Modify
Two-factor authentication login
Introduction to certificate services
Certificates
Verifying directory services
Installing certificate services
Configuring Automatic Certificate Request
Select FinishCloseOK
Securing Rbsu
Systems Insight Manager integration
Integrating Riloe II with Systems Insight Manager
Systems Insight Manager functional overview
Systems Insight Manager identification and association
Systems Insight Manager status
Systems Insight Manager links
Systems Insight Manager systems lists
Configuring Systems Insight Manager identification
Systems Insight Manager port matching
Receiving Snmp alerts in Systems Insight Manager
Systems Insight Manager integration
Directory services
Overview of directory integration
Benefits of directory integration
Schema-free
HP Extended schema
How directory integration works
Schema-free browser-based setup
Setup for Schema-free directory integration
Schema-free scripted setup
Active Directory preparation
Minimum Login Flexibility
Schema-free HPLOMIG-based setup Schema-free setup options
Better Login Flexibility
Maximum Login Flexibility
Setting up HP schema directory integration
Features supported by HP schema directory integration
Setting up directory services
Schema required software
Directory services support
Schema installer
Schema Preview
Setup
Directory services
Directory services for Active Directory
Management snap-in installer
Active Directory installation prerequisites
Results
Directory services preparation for Active Directory
Snap-in installation and initialization for Active Directory
NewHPObject
Directory services
Active Directory snap-ins
Directory services objects
Active Directory role restrictions
Directory services
Active Directory Lights-Out management
Directory services for eDirectory
EDirectory installation prerequisites
Snap-in installation and initialization for eDirectory
Directory services
Directory services
Directory Services objects for eDirectory
Members
Role managed devices
Enforced client IP address or DNS name access
EDirectory Role Restrictions
Time restrictions
Lights-Out Management
User login using directory services
Directory settings
Name or multi-host DNS name. If an IP address is
Group administration
Directory tests
Click Test Directory Settings
Introduction to directory-enabled remote management
Directory-enabled remote management
Using existing groups
Creating roles to follow organizational structure
Using multiple roles
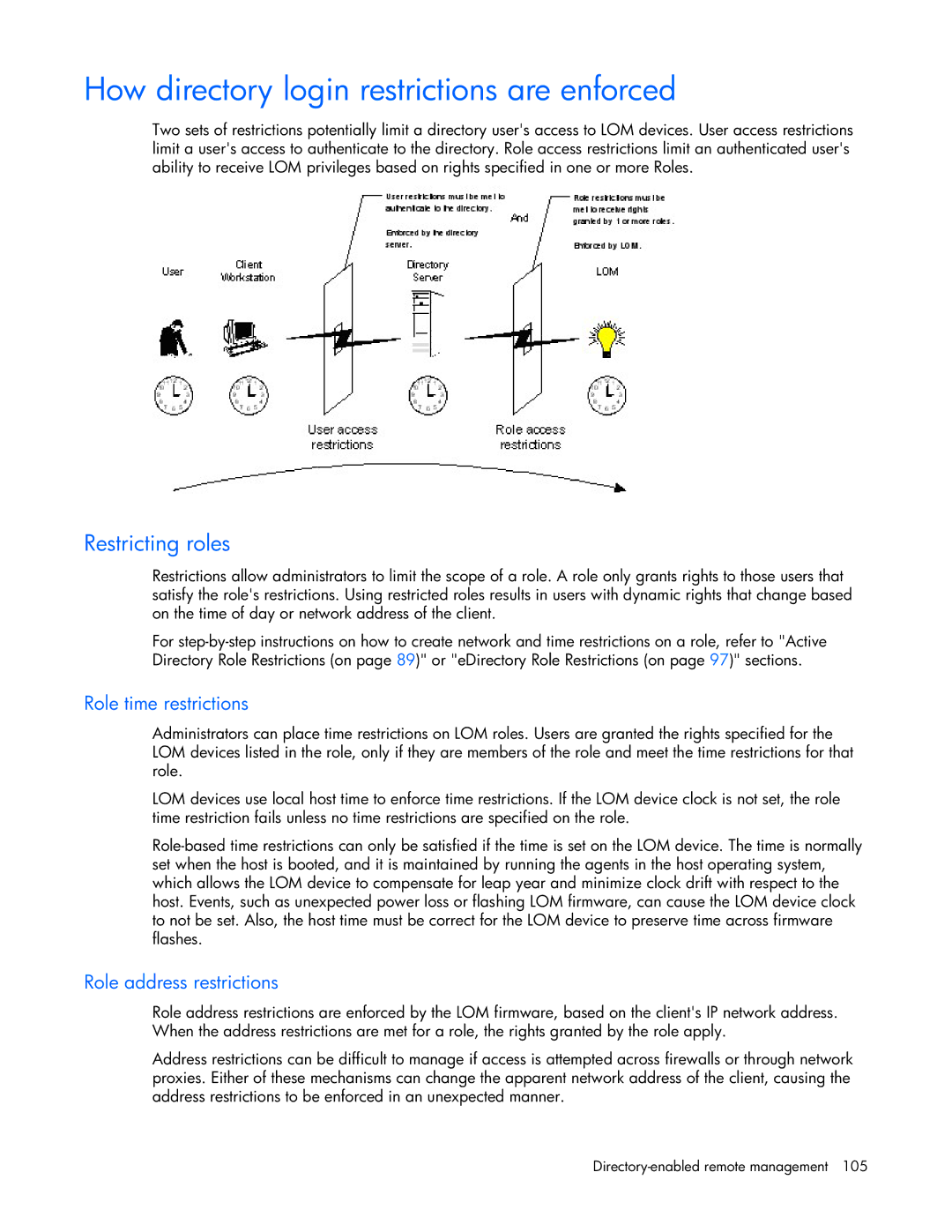
Restricting roles
How directory login restrictions are enforced
Role time restrictions
Role address restrictions
User restrictions
User address restrictions
How user time restrictions are enforced
Creating multiple restrictions and roles
Using bulk import tools
Directory-enabled remote management
Command line arguments
Scripting, command line, and utility options
Overview of the Lights-Out DOS utility
Cpqlodos general guidelines
Virtfloppy
Ribcl XML Commands for Cpqlodos
Adduser runtime errors
Cpqlodos runtime error
Cpqlodos parameter
Adduser parameters
Pre-migration checklist
Lights-Out directories migration utilities
Compatibility
HP Lights-Out directory package
Hpqlomig operation
Finding management processors
16.100.225.20RILOEII1.20RILOE2DBuserpasswordDefault Schema
Upgrading firmware on management processors
Selecting a directory access method
Naming management processors
Configuring directories when HP Extended schema is selected
Scripting, command line, and utility options
Setting up management processors for directories
Hpqlomgc operation
Firmware version is validated and updated if necessary
Launching Hpqlomgc using application launch
Management processor directory settings are updated
Directory is updated
RILOE2CONFIG
Hpqlomgc command language
RILOE2CONFIG
Lights-Out Configuration Utility
Create a custom command
Create a customized list
Create a task
Query definition in Systems Insight Manager
Application Launch using Systems Insight Manager
Click QueriesDevice
Select Management Processor and click OK
Lights-Out Configuration Utility parameters
Batch processing using the Lights-Out Configuration Utility
XML enhancements
Using Perl with the XML scripting interface
Opening an SSL connection
Readloop
Sending the XML header and script body
Scripting, command line, and utility options
Hponcfg requirements
Hponcfg supported operating systems
Using Hponcfg
Installing Hponcfg
Windows server installation
Linux server installation
Hponcfg command line parameters
Using Hponcfg on Linux servers
Obtaining an entire configuration
Using Hponcfg on Windows servers
Obtaining a specific configuration
Remote Insight command language
Setting a configuration
Ribcl sample scripts Ribcl general guidelines
XML header
Data types
Response definitions
Ribcl runtime errors
Login
Login parameters
Ribcl
Userinfo runtime error
Login runtime errors
Userinfo
Adduser
Adduser parameters
Deleteuser runtime errors
Adduser runtime errors
Deleteuser
Deleteuser parameter
Getuser
Getuser runtime errors
Getuser parameter
Getuser return messages
Moduser Parameters
Moduser
Getallusers
Moduser runtime errors
Getalluserinfo
Getallusers runtime errors
Getallusers parameters
Getallusers return messages
Ribinfo
Getalluserinfo runtime errors
Getalluserinfo parameters
Getalluserinfo return messages
Getnetworksettings
Resetrib
Getnetworksettings Parameters
Getnetworksettings Runtime Errors
Getnetworksettings Return Messages
Modnetworksettings Parameters
Modnetworksettings
Scripting, command line, and utility options
Modnetworksettings Runtime Errors
Getglobalsettings
Getglobalsettings parameters
Getglobalsettings runtime errors
Modglobalsettings parameters
Modglobalsettings
Scripting, command line, and utility options
Modglobalsettings runtime errors
Updateribfirmware
Cleareventlog Runtime Errors
Cleareventlog
Getfwversion
Hotkeyconfig parameters
Hotkeyconfig
Dirinfo
Getdirconfig
Getdirconfig return messages
Getdirconfig runtime errors
Dirinfo Login Ribcl
Moddirconfig
Moddirconfig parameters
Serverinfo
Resetserver
Insertvirtualfloppy Runtime Errors
Resetserver parameters
Insertvirtualfloppy
Ejectvirtualfloppy
Getvfstatus
Copyvirtualfloppy
Setvfstatus
Getvfstatus Runtime Errors
Getvfstatus Parameters
Getvfstatus Return Messages
Sethostpower
Gethostpowerstatus
Getvpbcablestatus
Getallcablesstatus Runtime Errors
Gettwofactorsettings
Getallcablesstatus
Getallcablesstatus Parameters
Gettwofactorsettings parameters
Modtwofactorsettings
Gettwofactorsettings runtime errors
Gettwofactorsettings return messages
Importing a CA and a user certificate example
Example of enabling Two-Factor Authentication
Modtwofactorsettings runtime errors
Modtwofactorsettings parameters
Troubleshooting the Riloe
Supported client operating systems and browsers
Supported hardware and software
USB
Server PCI Slot and Cable Matrix
PCI
Inability to connect to the board through the NIC
Network connection problems
Alert and trap problems
NetWare initialization errors
Web browser not connecting to the Riloe II IP address
NetWare error message table
Miscellaneous problems
Accessing System Partition Utilities
Inability to reboot the server
Interpreting LED indicators
Inability to upgrade the Riloe II firmware
Switch settings SW3 to force ROM upgrade
Incorrect time or date of entries in the event log
Remote Console mouse control issue
Login name and password problems
Resetting the Riloe II to Factory Default Settings
Virtual Floppy media applet is unresponsive
Video Problems
Troubleshooting the host server
Additional information on the state of the host server
Information logs
Event Log Entries
Integrated Management Log
Not connect to the specified IP address
Subsystem Failure Codes
Restarting the host server
Directory Services errors
Directory Server connect failed
Directory Server timeout
Invalid credentials
Invalid Directory Server address or port
HP Management Core Ldap OID classes and attributes
Directory Services schema
Core class definitions
Core attributes
HpqTarget
HpqRole
Core attribute definitions
HpqRoleIPRestrictionDefault
HpqPolicyDN
HpqRoleMembership
HpqRoleIPRestrictions
HpqRoleTimeRestriction
Lights-Out Management attributes
Lights-Out Management classes
Lights-Out Management class definitions
HpqLOMv100
Lights-Out Management attribute definitions
HpqLOMRightLogin
HpqLOMRightRemoteConsole
HpqLOMRightVirtualMedia
HpqLOMRightServerReset
HpqLOMRightLocalUserAdmin
HpqLOMRightConfigureSettings
Technical support
Before you contact HP
HP contact information
Federal Communications Commission notice
Regulatory compliance notices
Class a equipment
Class B equipment
European Union regulatory notice
Canadian notice Avis Canadien
Modifications
Class a equipment
France
Italy
Bsmi notice Japanese notice
ILO
Acronyms and abbreviations
IML
Ribcl
Index
77, 78, 81, 83, 85, 92, 99, 106, 114
16, 20, 21
Index