CrossFireTM 8600/8605 Token-Ring Switches
Page
CrossFireTM 8600/8605 Token-Ring Switches
Trademarks
Iii
Modifications
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Table of Contents
Installation
Preparing for Installation
Connecting a Network Management Console
Vii
Switch Configuration
Viii
Monitoring the Network with the Console 145
Monitoring the Network with Snmp 183
Monitoring Port Traffic 193 Troubleshooting 195
Getting in Touch with Technical Support 201
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
List of Figures
Connecting using Building Wiring
Xii
List of Tables
Xiii
About this Manual
Xiv
Overview and Specifications
Switch of Switches
Switching Technology
Switch of Hubs
Switch of Servers
Switch of Desktops
Switch of Routers
Switch of Floors and Buildings
Out-of-Band Management OBM
Physical Characteristics
Token-Ring Ports
Switched Port Analyzer
Labels
Reset Button
Universal Expansion Slots and Modules
System Request Button
State Meaning
Status and Activity LEDs
On or
Features
Features and Specifications
Performance and Advanced Features
Management
Installation
Scalability and High Availability
Capacity
Specifications
Performance
Physical Characteristics
Software updates
Specification Value Operating Temperature
Non-operating Temperature
Safety
Tivoli TME 10 NetView for AIX
Specification Value Network management
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
How the CrossFire 8600 and the CrossFire 8605 Works
Switch Theory of Operation
Multiple Simultaneous Conversations
Address Management
Low Latency
Multiple Bridging Modes
Source Route Bridging SRB
Source Route Switching SRS
Source Route Transparent SRT
SRT/SRB
Filtering
Store and Forward
Three Switching Modes
Congestion Control
Cut-Through
RI/RO-Like Connection
Token-Ring Port Operation Modes
CrossLink Connections
Transmission Priority Queues
Spanning Tree Protocol Support
Vlan Support
Switch Configured with Two VLANs
Management
Specification
IBM LAN Network Manager
Switch Manager for HP OpenView for Windows
Rmon Support
Telnet Management and VT100 Management Console
Built-in Port Counters
Internal Stacker
Optional Redundant Power Supply
Stackable Architecture
Back-to-Back
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Token-Ring Port Operation Modes
Benefits of the CrossFire 8600 and the CrossFire
Automatic media
Feature Function Benefit Automatic port
Sensing of operating
Mode
Auto
Three Switching Modes
Feature Function Benefit Cut-Through
Store and Forward
Expansion Module Slots
Multiple Bridging Modes
Spanning Tree Protocol
Feature Function Benefit Ieee 802.1D
Windows
Feature Function Benefit
Vlan support
HP OpenView for
Network Monitoring
Control LLC
Feature Function Benefit MAC address
Filtering
Logical Link
Connectivity Options
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Safety with Electricity
Safety Recommendations
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Preventing Electrostatic Discharge Damage
Environment
Chassis Accessibility
Power
Site Requirements
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Unpacking and Inspecting
Frame Length Limit
Rules to Remember
Cables and Distances between Devices
Sample Applications for the CrossFire 8600 and the CrossFire
Simple Application of the Switch
Typical Network without the CrossFire Switches
Replacing SRBs with CrossFire 8600 or CrossFire
Next Step
Important Management Considerations
Star-Wired Topology of Interconnected Switches
Required Network Preparation Frame Length Limit
Installation
Installation Summary
Unpacking Instructions
Materials Needed for Installation
Removing the Universal Expansion Slot Cover
Installing a Universal Expansion Module
Rack or Cabinet Mounting
Mounting the Chassis
Table-Mounting
Mounting the Switch in a Rack or Cabinet
Cabling
Connecting Devices to the Token-Ring Ports
Connecting Devices to Token-Ring Ports
Connecting using Building Wiring
Checking the Installation
Back Panel of the Switch
Applying Power
Page
Name Description
Connectors and Push-Buttons
Control Panels
Front Panel
Status LEDs
Back Panel
Connecting the Console
Connecting a Network Management Console
XON/XOFF
Specification Value
Disable the Use Function, Arrow,
Communication Problems
Ctrl Keys for Windows option located
Diagnostic Screen
Press Return key to activate console
CrossFire 8600/8605 Token-Ring Switches v .2, P/N
Switch Configuration
General Guidelines
Navigating within the Menus
Main Menu
Configuration Menu
Console Configuration
Port Configuration
Switched Port Analyzer
Password
Burned-in MAC Address
Switch Configuration Screen
Configured MAC Address
System Description
Switch reserves 31 addresses for ports
System Name
Dram Installed
Flash Memory Installed
Address Format
Local Box Number
Stack Configuration Screen
Time of Day
Number of Boxes
Module Information Screen
HW Rev
Status
Model
Board ID
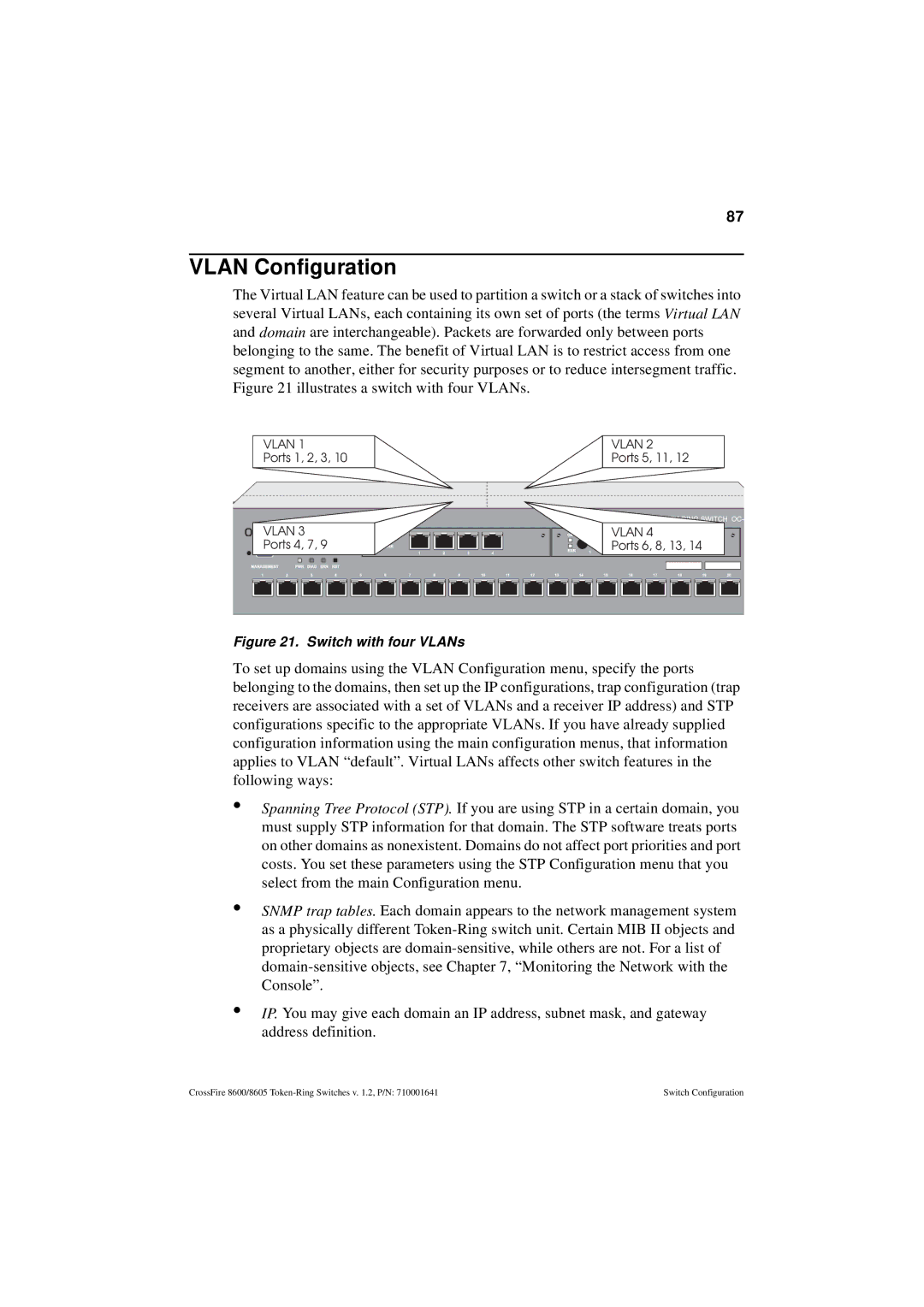
Switch with four VLANs
Vlan Configuration
Local Vlan Port Configuration
Vlan Configuration Menu
Vlan Configuration Screen
Delete
Vlan Parameter Configuration for TrCRF Screen
Add
Change
State
Bridging Mode
Vlan Name
Parent Vlan
MTU
Vlan Parameter Configuration for TrBRF Screen
Local Vlan Port Configuration Screen
IP Address
IP Configuration Screen
Default Gateway
Interface MAC Address
Send Ping
IP State
BootP Requests and Parameters
Spanning Tree Protocol
Snmp Configuration Menu
Ieee 802.1D Spanning Tree Protocol STP
STP Participation
Spanning Tree for TrBRF Screen
Bridge Hello Time in Seconds
Bridge Forward Delay in Seconds
100 Ieee STP Uses Bridge Functional Address
Bridge Priority
STP Priority
STP Mode TrBRF to TrCRF
Spanning Tree for TrCRF Screen
101
Switch Forward Delay in Seconds
Switch Priority
Switch Hello Time in Seconds
Switch Maximum Message Age in Seconds
Priority
Port Spanning Tree Parameters Screen
103
Port Spanning Tree Parameters
Current Spanning Tree Information Screen
104 STP Mode
Name
Port Configuration Screen
Enabled
105
Max Explorer Rate on Input
106 Status
Media Type
Media Speed
Forwarding Mode
107 Operation Mode
Priority Threshold
108 Min Transmit Priority
Error High Threshold
Error Low Threshold
Error Sampling Interval
CrossLink
Switched Port Analyzer Menu
109
110
111
CrossLink Menu
CrossLink Configuration Screen
113
Setting up a CrossLink
114
Current CrossLink Information Screen
115
Address Filtering
Filters and Port Security Menu
MAC Address
Configure Filters Screen
117
Index
Applied Ports
118
Exit Ports
119
Configure Port Security Mode Screen
120
View Port Filters Screen
Description
Protocol Class Assignment
Port number Security Mode
Protocol Filters Menu
121 More
Ethertype
Protocol Class Assignment Screen
122
Class
123
Port Filtering Attributes Screen
Block
124 Ethertype
Set at the Master Address Table Aging menu
Address Aging
125
Set at the Port Address Table Aging menu
Port Address Table Aging
Configuration menu
Address Aging Menu
126
Demand Aging Level
Port Address Table Aging Screen
127
Aging Time min
128
Master Address Table Aging Screen
Aging Time
129
Password Menu
Set Password
Delete Password
Console/Telnet Sessions
Console Configuration Menu
Serial Link Configuration Screen
Stopping the Console Session
Creating a Console Session Using a Modem
132
Telnet Configuration Screen
Remote
Telnet Sessions Screen
134 Telnet Sessions
Box
135
Starting the Telnet Session
Stopping the Telnet Session
Involuntary Termination of the Telnet Session
136
Tftp Download/Upload
Download/Upload Menu
137
Serial Link Download
138
Serial Link Download Screen
Select Serial Link Download Select Main Image Download
Download Vlan
Tftp Download/Upload Screen
139
Tftp Server Address
Execute name Download/Upload
141
Reset Switch Without Diagnostics
Reset Screen
Number of Resets Since Diagnostics
Reset Switch With Diagnostics
Power-On Diagnostics
143 Reset Port Address Table
Clear Non-Volatile RAM
144
145
Monitoring the Network with the Console
146
Navigating Within the Menus
Statistics Menu
Display Summary
Switch Statistics Screen
148 Diagnostic Test Results
Message Log Information
Reset
149 Board Temperature
Frame Transmit Errors
Error Frames Received
Spd
Port Status Screen
150
Ins
Fwd Mode
151 Oper Mode
Port Statistics Menu
General Statistics Screen
Broadcast Frames Received
Frame Errors
154 Frames Processed
Frames Unknown
Transmit Buffer Overflows
Config Loss
Config Loss Reason
155 Receive Buffer Overflows
Statistics Screen
Last Reset
Line Errors
Burst Errors
Lost Frame Errors
157 AC Errors
Abort Transmit Errors
Internal Errors
Lobe Wires
158 Hard Errors
Signal Loss
Recoveries
Ring State
State Information Screen
159
Ring Status
DTR MAC Information Menu
Authorized Function Classes
Error Report Timer
TXI Information Screen
161 Station-CPort Information
Beacon UNA
162 Join State
Monitor State
Beacon Source Address
Station-CPort Information Screen
164 CPort Phantom Drive Mask
Common Access Protocol Mask
Common Policy Flags
Address Tables Menu
166
Master Address Table Screen
Address
Unknown
167
Route hex
Master Route Descriptor Table Screen
168 Ports
Search
169 Type
170
Vlan Address Table screen
171
Vlan Route Descriptor Table Screen
Root CRF
172
Bridge ID
Root ID
PCst
Forward Delay
173 Max Message Age
PId
# Chgs
174 DCst
Dsg SwId/BrId
Dsg PId
175
Current Spanning Tree Information for a TrCRF Screen
Root Port
176 Max Message Age
177
Vlan Statistics Screen for TrCRF
Vlan Statistics
178
179
Vlan Statistics Screen for TrBRF
Display Members
180
Diagnostic Test Results Screen
Message Log Information Screen
182 Clear
Display Summary Screen
183
Snmp Setup
Community String screen Trap Receiver screen
Enable Rmon Statistics
Snmp Configuration
Snmp Configuration Screen
Send Authentication Traps
185 Community Strings
Community Strings Screen
Trap Receivers
186 Community Name
187
Trap Receivers Screen
General traps
List of Supported Traps from a Switch
188 Add Entry
Zoom
Enterprise specific traps from OC8600.MIB
189
Per Port Traps
Traps for the Spanning Tree Protocol
190
Oc8600TsCrossLinkFailed
191 Traps for CrossLinks
192
Active Monitoring
193
Passive Monitoring
Select Then
194
Port Number
Port To Monitor
Troubleshooting in a Network
Obtaining Service
Start of Troubleshooting Process
196
Choosing a Troubleshooting Procedure
Symptom and LED State Go To
Procedure a
Procedure C
197 Procedure B
198 Procedure D
199
200
Hotline Support
Before You Contact Olicom Technical Support
201
Isdn Modem
Bulletin Board Service
Fax Support
Standard Modem Requirements
Olicom Support WEB
Internet E-Mail
Anonymous Internet FTP Server
Internet World Wide Web Server WWW
204
Problem Report Form
Switch Information
Switch Configuration
205
Problem Description Network Installation Sketch
206
207
Appendix A. Abbreviations
Mbps
208
TrBRF
209
TrCRF
210
Cable Function Cable Type or Cable Solution
Connecting to the Out-of-Band Management Port
211
Management Port Pin-Out
Pin Signal Name
Out-of-Band Management Port and Cable Pin-Outs
212
213 TIA/EIA 232 Null-Modem Connections
TIA/EIA 232 Null-Modem Cable for the 25-pin Connector
Straight-Through 100-Ohm/120-Ohm Cable
Ohm IBM STP Data Connector-to-RJ-45 Straight-Through Cable
Twisted-Pair Cable Pin Outs
214
Cable Type
Cabling Recommendations
215
Cable Type Impedance
Number Of Attaching Devices
216
Ring Speed Ohm Type Ohm Category
CrossFire 8600 Token-Ring Switch
217
Ring Types Speed
Ring Speed 62.5/125 µm
CrossFire 8605 Token-Ring Fiber Switch
218
Ring Speed 100 or 120 Ohm Category
219
220
Numerics
Index
119
Index-2
116
Index-3
207 203
Index-4
MMF
Index-5
131 162
Index-6
Index-7
Index-8
170
Index-9
Index-10
Index-11
Index-12
Page
Olicom Australia