For the
NOTE: When configured for EAP authentication, the RADIUS server supports either
Table 2. Allowable Authentication Modes.
The
The
2.6.2.2. Robustness
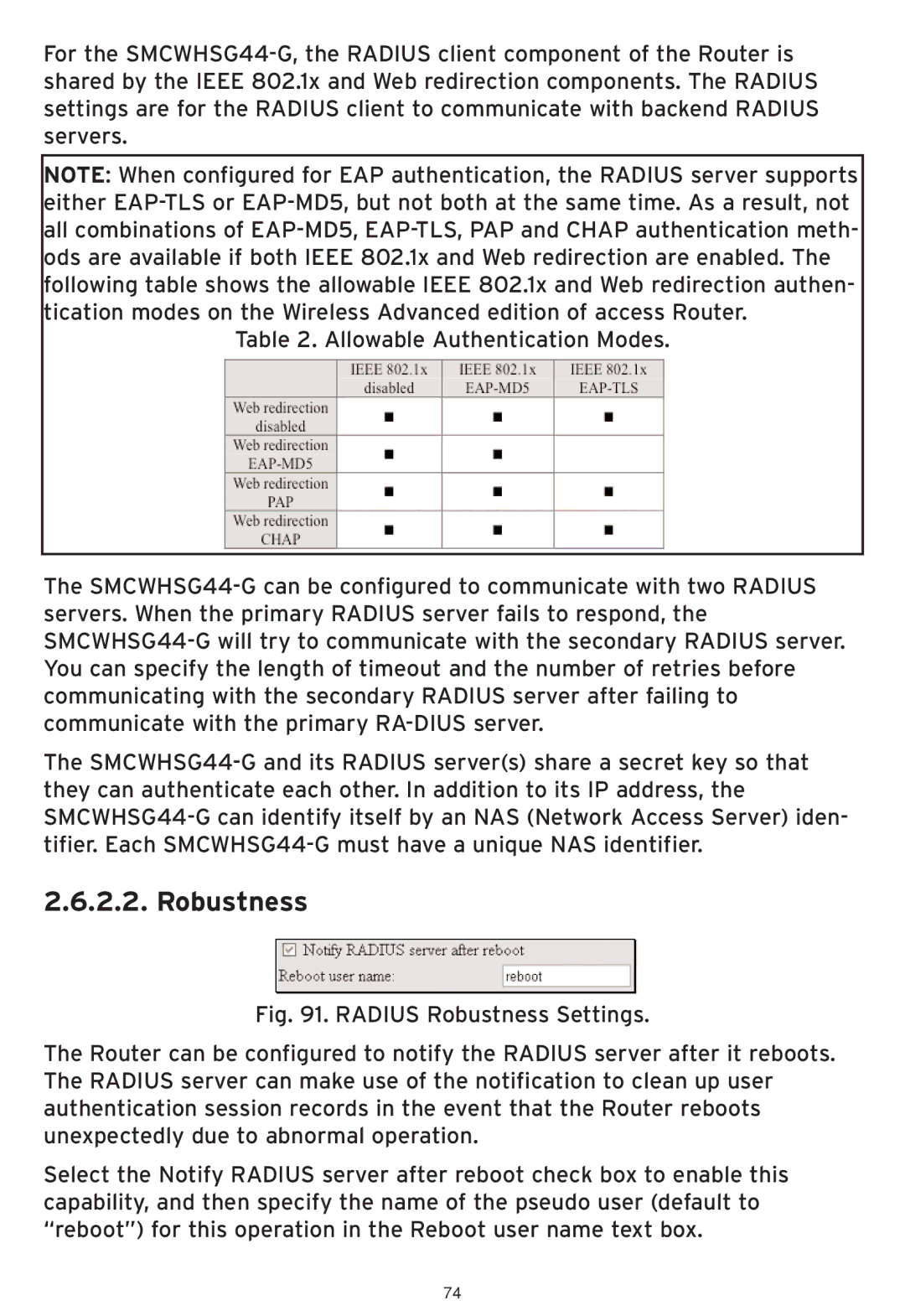
Fig. 91. RADIUS Robustness Settings.
The Router can be configured to notify the RADIUS server after it reboots. The RADIUS server can make use of the notification to clean up user authentication session records in the event that the Router reboots unexpectedly due to abnormal operation.
Select the Notify RADIUS server after reboot check box to enable this capability, and then specify the name of the pseudo user (default to “reboot”) for this operation in the Reboot user name text box.
74