Chapter 4 Configuring Connection Entries
Authentication Methods
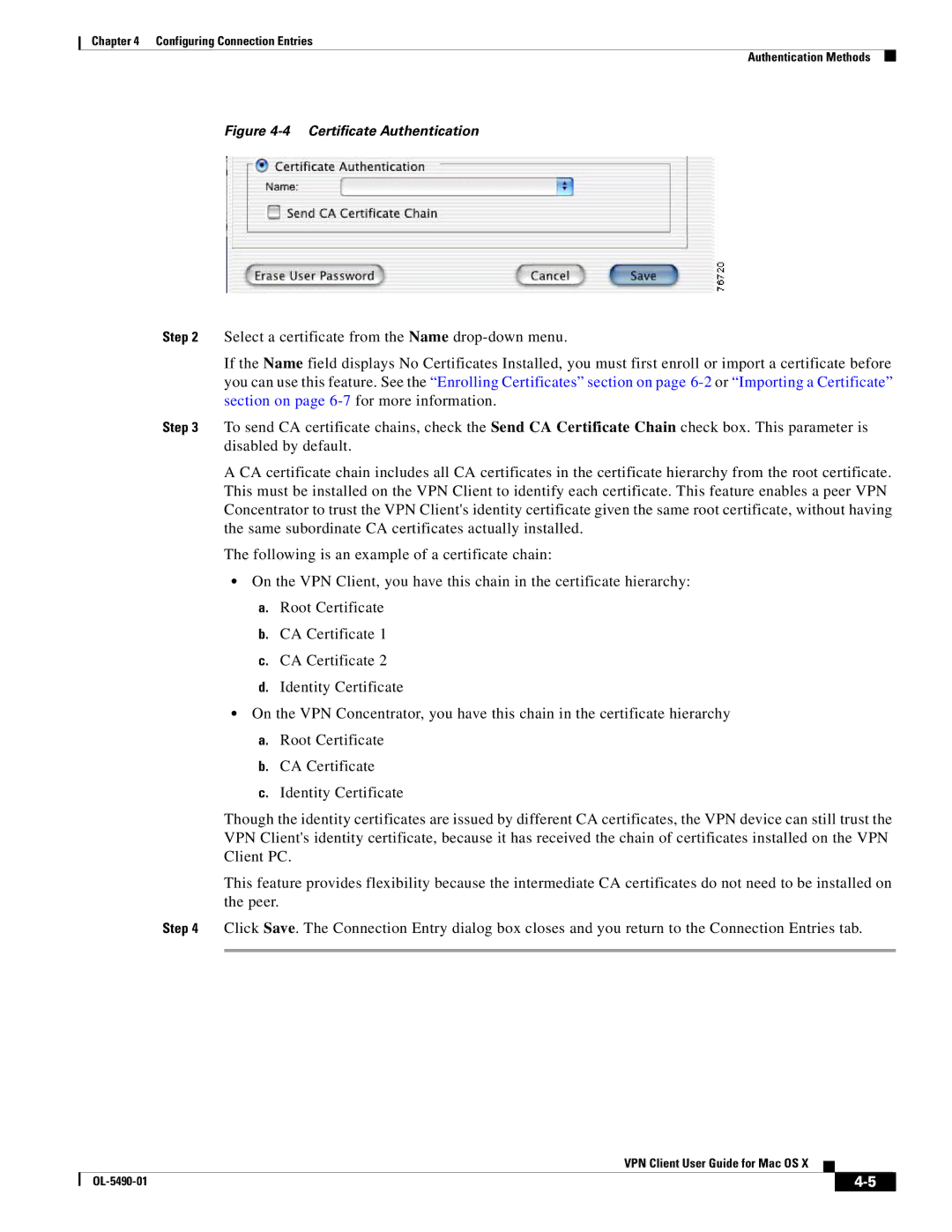
Figure 4-4 Certificate Authentication
Step 2 Select a certificate from the Name
If the Name field displays No Certificates Installed, you must first enroll or import a certificate before you can use this feature. See the “Enrolling Certificates” section on page
Step 3 To send CA certificate chains, check the Send CA Certificate Chain check box. This parameter is disabled by default.
A CA certificate chain includes all CA certificates in the certificate hierarchy from the root certificate. This must be installed on the VPN Client to identify each certificate. This feature enables a peer VPN Concentrator to trust the VPN Client's identity certificate given the same root certificate, without having the same subordinate CA certificates actually installed.
The following is an example of a certificate chain:
•On the VPN Client, you have this chain in the certificate hierarchy:
a.Root Certificate
b.CA Certificate 1
c.CA Certificate 2
d.Identity Certificate
•On the VPN Concentrator, you have this chain in the certificate hierarchy
a.Root Certificate
b.CA Certificate
c.Identity Certificate
Though the identity certificates are issued by different CA certificates, the VPN device can still trust the VPN Client's identity certificate, because it has received the chain of certificates installed on the VPN Client PC.
This feature provides flexibility because the intermediate CA certificates do not need to be installed on the peer.
Step 4 Click Save. The Connection Entry dialog box closes and you return to the Connection Entries tab.
VPN Client User Guide for Mac OS X
|
| ||
|
|