Chapter 5 Further Configuration
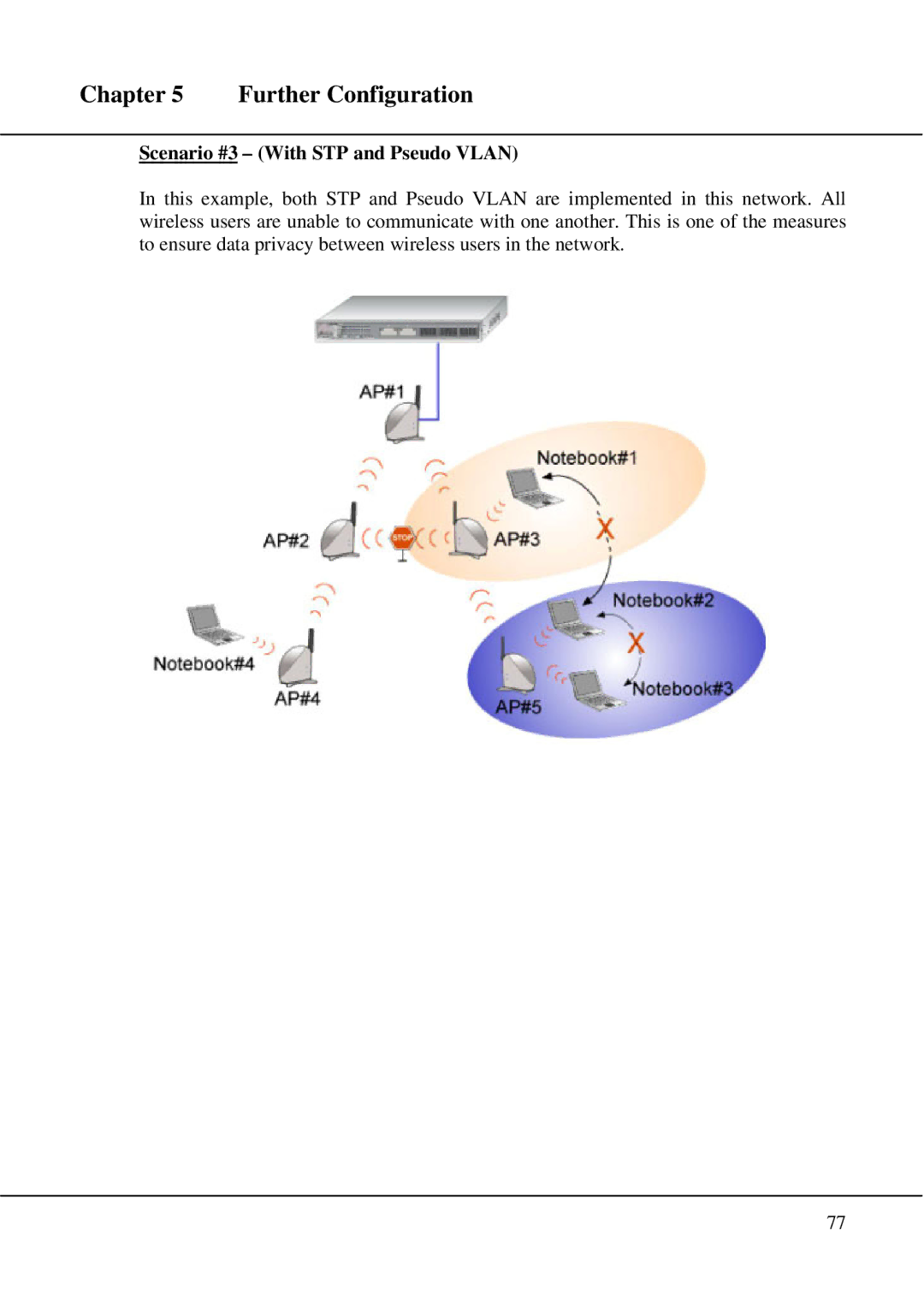
Scenario #3 – (With STP and Pseudo VLAN)
In this example, both STP and Pseudo VLAN are implemented in this network. All wireless users are unable to communicate with one another. This is one of the measures to ensure data privacy between wireless users in the network.
77