VBrick v4.1 MPEG-2 Appliance Admin Guide
VB4000-5000-6000 Series Network Video Appliances
FCC Notice
Copyright
About VBrick Systems
2. MPEG-2 Configuration
Contents
MPEG-2 Admin Guide
1. Introduction
3. SDI Configuration
4. Status
7. Maintenance Mode
5. Diagnostics
6. Maintenance
8. VBStar
Index
Organization
MPEG-2 Admin Guide
Getting Help
Printer-Friendly
Font Conventions
Italics are used to emphasize specific words or phrases
Overview
Introduction
Chapter
VBSSM
Configuration
Mixed Model Appliances
Archiver and Recorder Functionality
Model
Figure 1. Archiver/Recorder Functionality
Introduction
2007 VBrick Systems, Inc
MPEG-2 Configuration
MPEG-2 Overview
Option
Optimizing MPEG-2 Performance
Applicable Model
Dest1, Dest2
MPEG-2 Configuration Recommendations
Absolute Maximum Transport Rates
Decoder
Decoder
Configuration Network
Configuration Network Ethernet
Gateway IP Address
can be letters, numbers or hyphens
Domain Name Server
Configuration Network Routing
Network Time Synchronization
Routing Method
Configuration Network Management
Configuration Billboard
Configuration Network IPv6
Using the Billboard
Billboard FTP
Local URL
Billboard URLs
Billboard File Types
Remote URL
Font Sizes
Creating a Billboard
Video Input
Transparent Background
Configuration Decoder Video
Configuration Decoder
applying this parameter will cause the VBrick to reset
Configuration Decoder Audio
Configuration Decoder Network
Receive Address
Configuration Decoder Picture-In-Picture
Picture in Picture
Configuration Encoder
Configuration Encoder Transport
Configuration Encoder Video
Video Format
\d or \D - Current Date
\h or \H - Host Name
\t or \T - Current Time
Reference Distance
Configuration Encoder Audio
Audio Input
Configuration Encoder Destination 1/Destination2
Destination Address
Configuration Encoder Announce SAP
Announce Common Information
support replacement characters. The replacement text is only shown in
SAP for Destination 1 and/or
following string IPMask=xxx.xxx.xxx.xxx where
Configuration Encoder Text Insertion
Configuration FTP File Transfer
Configuration Pump
Configuration Recorder
Configuration Conferencing
Conferencing
Configuration Passthrough
Configuration Passthrough COM1
Passthrough State Responder
Passthrough State Initiator
Destination
Configuration Passthrough COM2
Configuration System
Dedicated Address Mode
parameters before you can enable Network Time Synchronization on
Configuration System General
System
this window
Configuration System SNMP Traps
Front Panel LCD Display
Program Files\VBrick\VB6000\Download\ReleaseVxxxxxx
Number
Event Description
Number
Configuration System Security
Improving Security
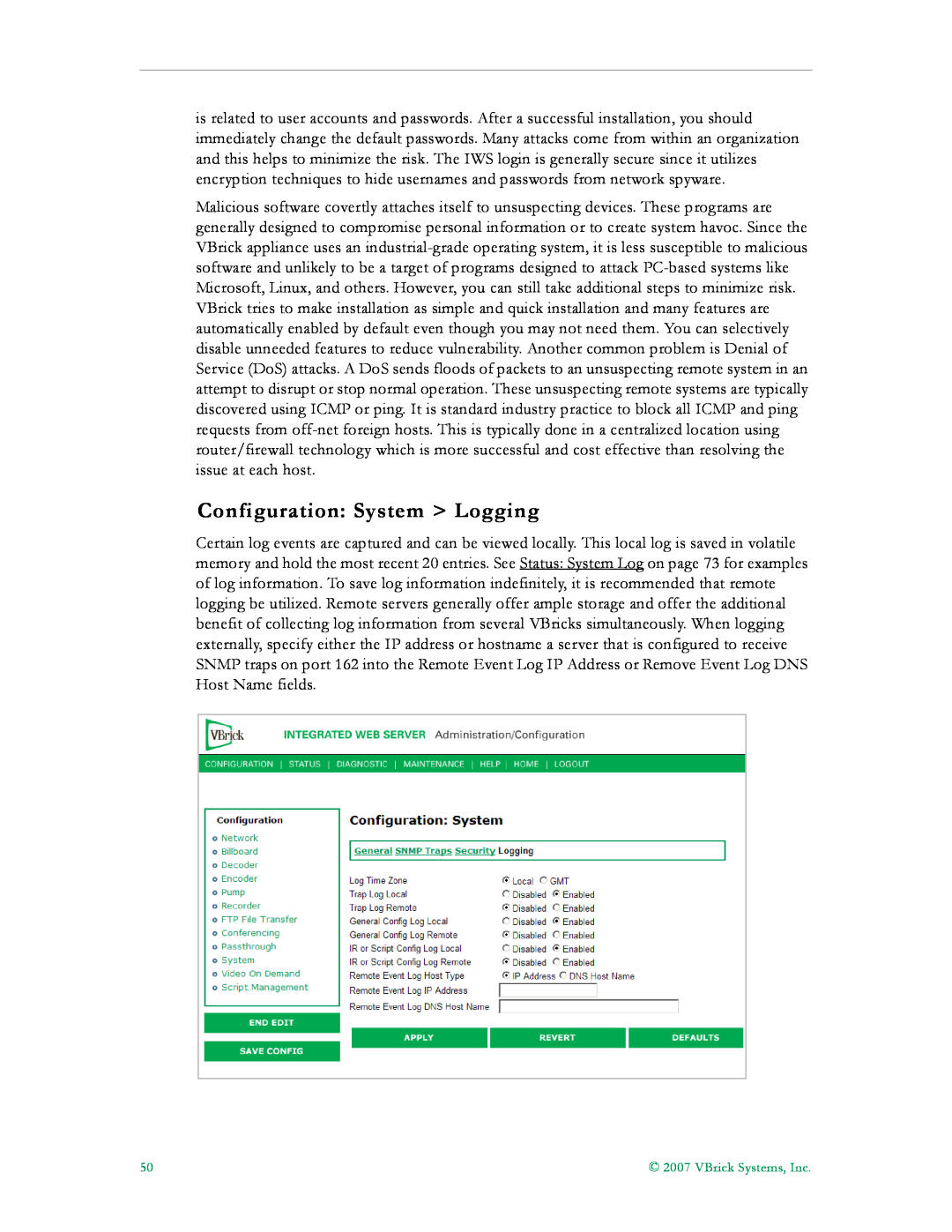
Configuration System Logging
Configuration Video On Demand
Configuration Script Management Event Triggering
Configuration Script Management
Run Scripts Using IWS
Figure 2. Script Management - Part
Run Scripts Using Event Triggers
Run Scripts Using the IR Remote Control
Sample Script
Configuration Script Management Auto Configuration
Scripting Notes
XML Header
SDI Configuration
Introduction
Vertical Offset Correction
SDI Audio Input
2007 VBrick Systems, Inc
Status
Status System Information
System Model
Status Network Status
Status Network Status Codec
General
or 100Mbit
Status Network Status Routing
Interface
Status Network Status Network Time Status Network Status IPv6
Status Decoder Status
MPEG-2 Decoder Status
Decoder State
Status Encoder Status
Status Hard Drive Status
MPEG-2 Encoder Status
Status Hard Drive Status General
Status Hard Drive Status Pump
Network
Status Hard Drive Status Recorder
Status System Log Config
Status FTP Server Status Status System Log
Status System Log System Event
Status System Log Traps
Status System Log System Info
Status User Information
Status User Information Main Board
Status User Information Slot1/Slot2
User Information Version
2007 VBrick Systems, Inc
User Diagnostics
Diagnostics
Diagnostics Network Tests
Diagnostics Network Tests Ping Test
Diagnostics Network Tests Trace Route Test
Trace Route Test Results
Diagnostics Network Tests Data Test
Diagnostics Device Test
Diagnostics Decoder Color Bars
Diagnostics Hard Drive
2007 VBrick Systems, Inc
Maintenance
Maintenance Device Information
Maintenance Read/Write Configuration
Maintenance Default All Configuration
Maintenance Read/Write Read From Device
Read Configuration Data from Device
Maintenance Read/Write Write To Device
Maintenance Usernames & Passwords Change Usernames & Passwords
Maintenance Change Usernames & Passwords
Write Configuration Data to Device
User Name
Default Password
Maintenance Usernames & Passwords Change SNMPv3 Passwords
Default User Name
User Level
User Name
Maintenance Mode
Maintenance Mode Indicators
Maintenance Mode Features
Maintenance Mode Limitations
Entry
Maintenance Mode CLI Operation
Command
ex or exit
Description
VBStar
VBStar Pump
Recording vs. Archiving
store files on the C drive. The C drive has limited space and is
Configuration Pump General
reserved for VBrick firmware
Configuration Pump Destination
Configuration Pump Announce SAP
See MPEG-2 Configuration Encoder Announce SAP on page
Configuration Pump Operation
Filename Syntax Rules
Using Mixed Models
VBStar Record
Recording Batch Files
Batch Wrap Point and Record Duration
Configuration Recorder General
FTP Server Enable
Configuration Recorder Network
Configuration Recorder Operation
Recorder State
Configuration FTP File Transfer Servers
VBStar FTP File Transfer
Configuration FTP File Transfer Transfers
FTP Server
FTP Status
VBStar Status
FTP Queue Operation
2007 VBrick Systems, Inc
Index
Page
Page
VBrick Systems, Inc 12 Beaumont Road
Wallingford, Connecticut 06492, USA