•Access Layer: Place Cisco NAMs at the access layer only if critical clients are required to be monitored. IP phones, for example, can be monitored for latency or for adequate response to and from Cisco CallManagers.
•WAN Edge: Place Cisco NAMs at the WAN edge to gather WAN statistics from Optical Services Module (OSM) or FlexWAN interfaces, or to collect NetFlow statistics on remote
•Branch Office: Place Cisco NAMs in the branch office to troubleshoot remote sites, similar to being on the campus, but taking full advantage of the remote accessibility and local data collection of the Cisco NAMs.
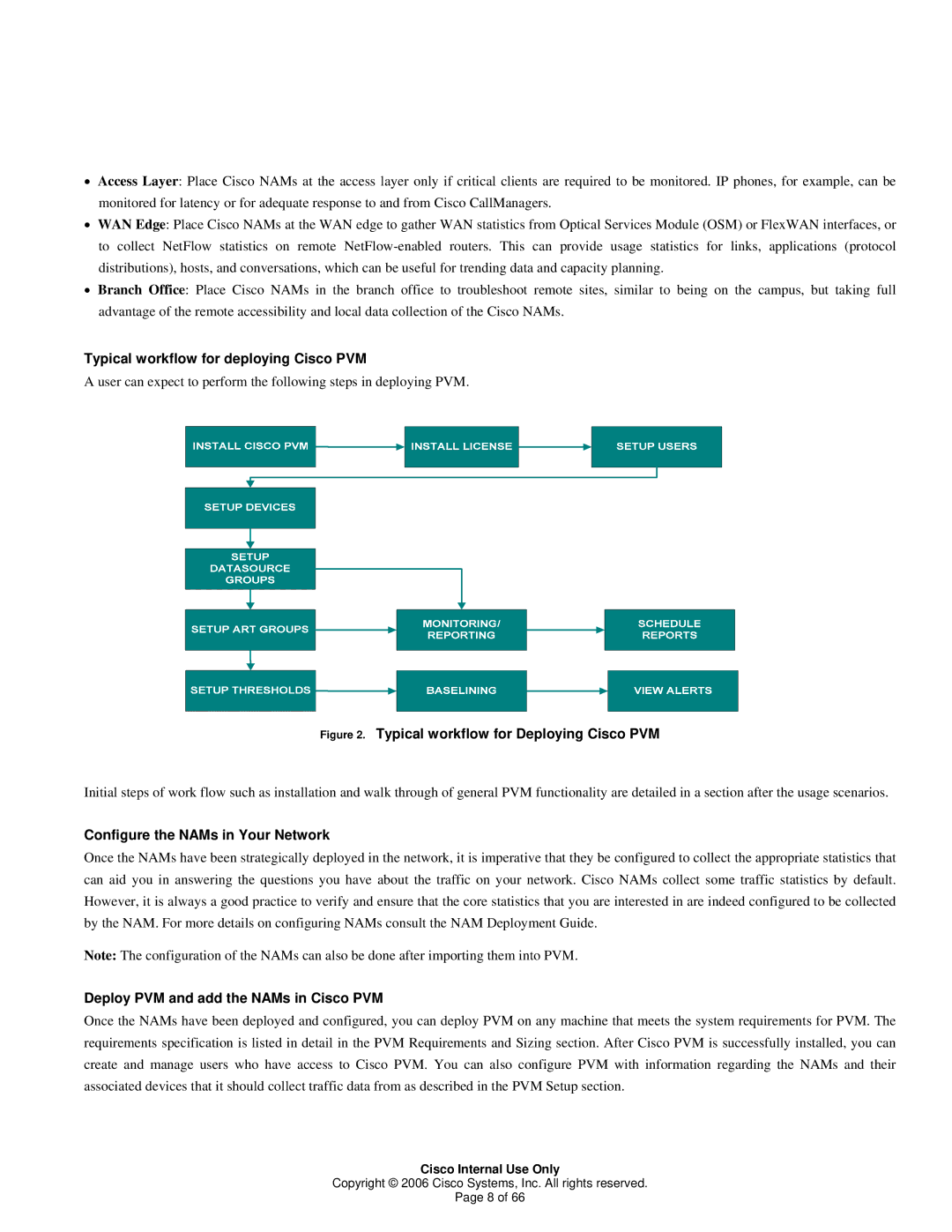
Typical workflow for deploying Cisco PVM
A user can expect to perform the following steps in deploying PVM.
Figure 2. Typical workflow for Deploying Cisco PVM
Initial steps of work flow such as installation and walk through of general PVM functionality are detailed in a section after the usage scenarios.
Configure the NAMs in Your Network
Once the NAMs have been strategically deployed in the network, it is imperative that they be configured to collect the appropriate statistics that can aid you in answering the questions you have about the traffic on your network. Cisco NAMs collect some traffic statistics by default. However, it is always a good practice to verify and ensure that the core statistics that you are interested in are indeed configured to be collected by the NAM. For more details on configuring NAMs consult the NAM Deployment Guide.
Note: The configuration of the NAMs can also be done after importing them into PVM.
Deploy PVM and add the NAMs in Cisco PVM
Once the NAMs have been deployed and configured, you can deploy PVM on any machine that meets the system requirements for PVM. The requirements specification is listed in detail in the PVM Requirements and Sizing section. After Cisco PVM is successfully installed, you can create and manage users who have access to Cisco PVM. You can also configure PVM with information regarding the NAMs and their associated devices that it should collect traffic data from as described in the PVM Setup section.
Cisco Internal Use Only
Copyright © 2006 Cisco Systems, Inc. All rights reserved.
Page 8 of 66