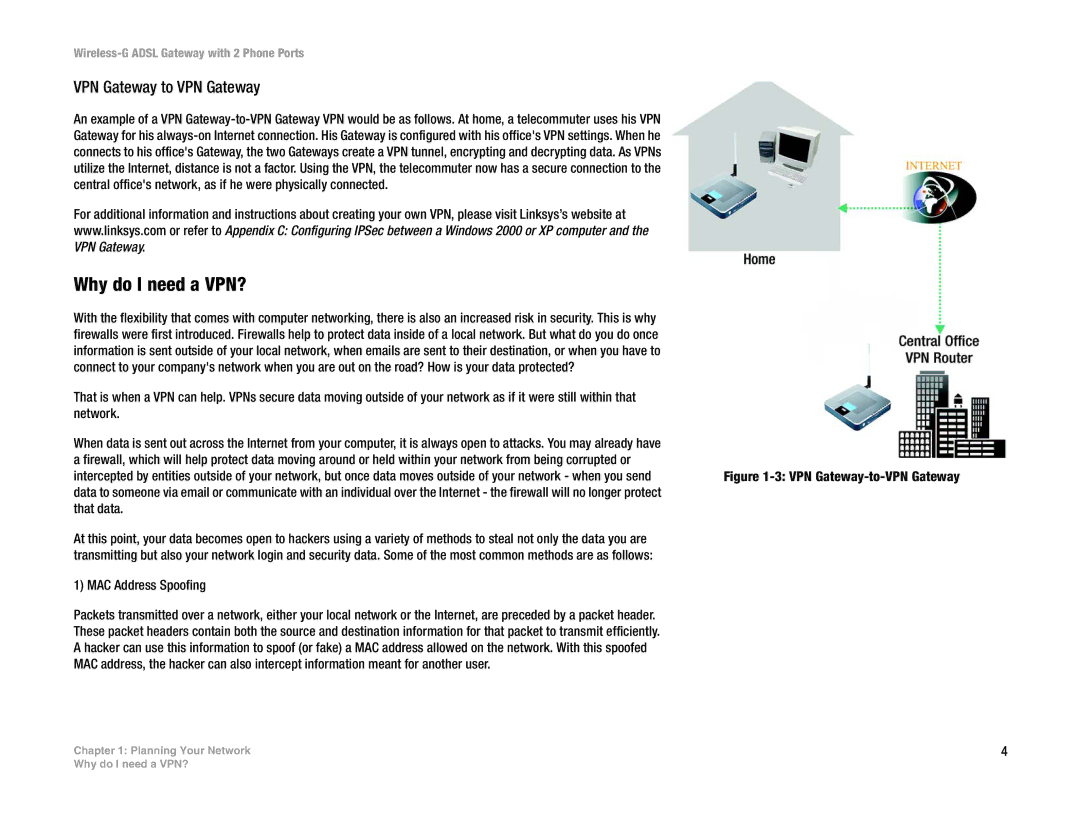
VPN Gateway to VPN Gateway
An example of a VPN
For additional information and instructions about creating your own VPN, please visit Linksys’s website at
www.linksys.com or refer to Appendix C: Configuring IPSec between a Windows 2000 or XP computer and the
VPN Gateway.
Why do I need a VPN?
With the flexibility that comes with computer networking, there is also an increased risk in security. This is why firewalls were first introduced. Firewalls help to protect data inside of a local network. But what do you do once information is sent outside of your local network, when emails are sent to their destination, or when you have to connect to your company's network when you are out on the road? How is your data protected?
That is when a VPN can help. VPNs secure data moving outside of your network as if it were still within that network.
When data is sent out across the Internet from your computer, it is always open to attacks. You may already have a firewall, which will help protect data moving around or held within your network from being corrupted or
intercepted by entities outside of your network, but once data moves outside of your network - when you sendFigure
that data.
At this point, your data becomes open to hackers using a variety of methods to steal not only the data you are transmitting but also your network login and security data. Some of the most common methods are as follows:
1) MAC Address Spoofing
Packets transmitted over a network, either your local network or the Internet, are preceded by a packet header.
These packet headers contain both the source and destination information for that packet to transmit efficiently.
A hacker can use this information to spoof (or fake) a MAC address allowed on the network. With this spoofed
MAC address, the hacker can also intercept information meant for another user.
Chapter 1: Planning Your Network | 4 |
Why do I need a VPN?