700 Series Managed Switch User’s Guide for Software v2.1
![]() 1
1 ![]()
![]() 3
3 ![]()
4
![]() 5
5 ![]()
![]() 7
7
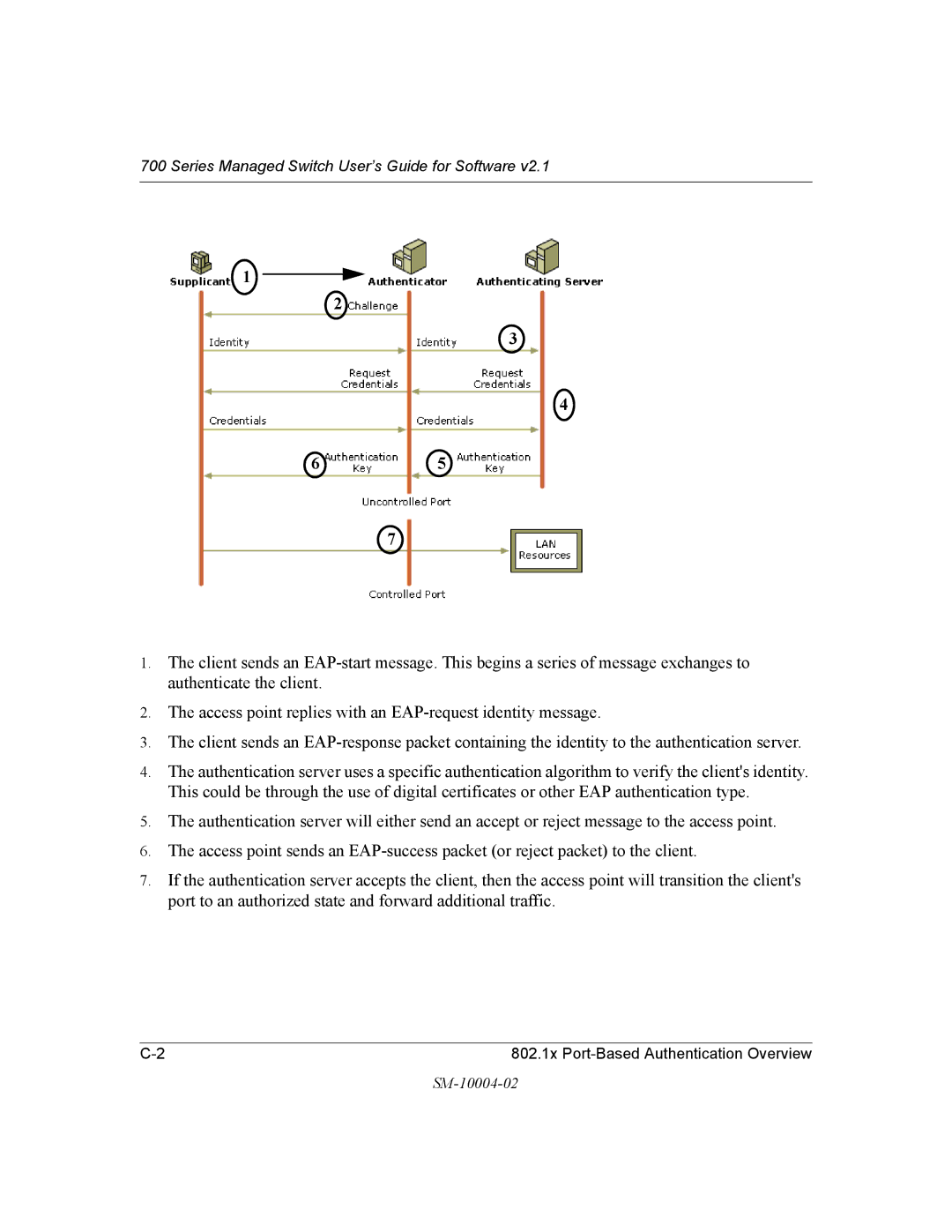
1.The client sends an
2.The access point replies with an
3.The client sends an
4.The authentication server uses a specific authentication algorithm to verify the client's identity. This could be through the use of digital certificates or other EAP authentication type.
5.The authentication server will either send an accept or reject message to the access point.
6.The access point sends an
7.If the authentication server accepts the client, then the access point will transition the client's port to an authorized state and forward additional traffic.
802.1x |