A
3 – Planning Fabric Security
3.7.4.2
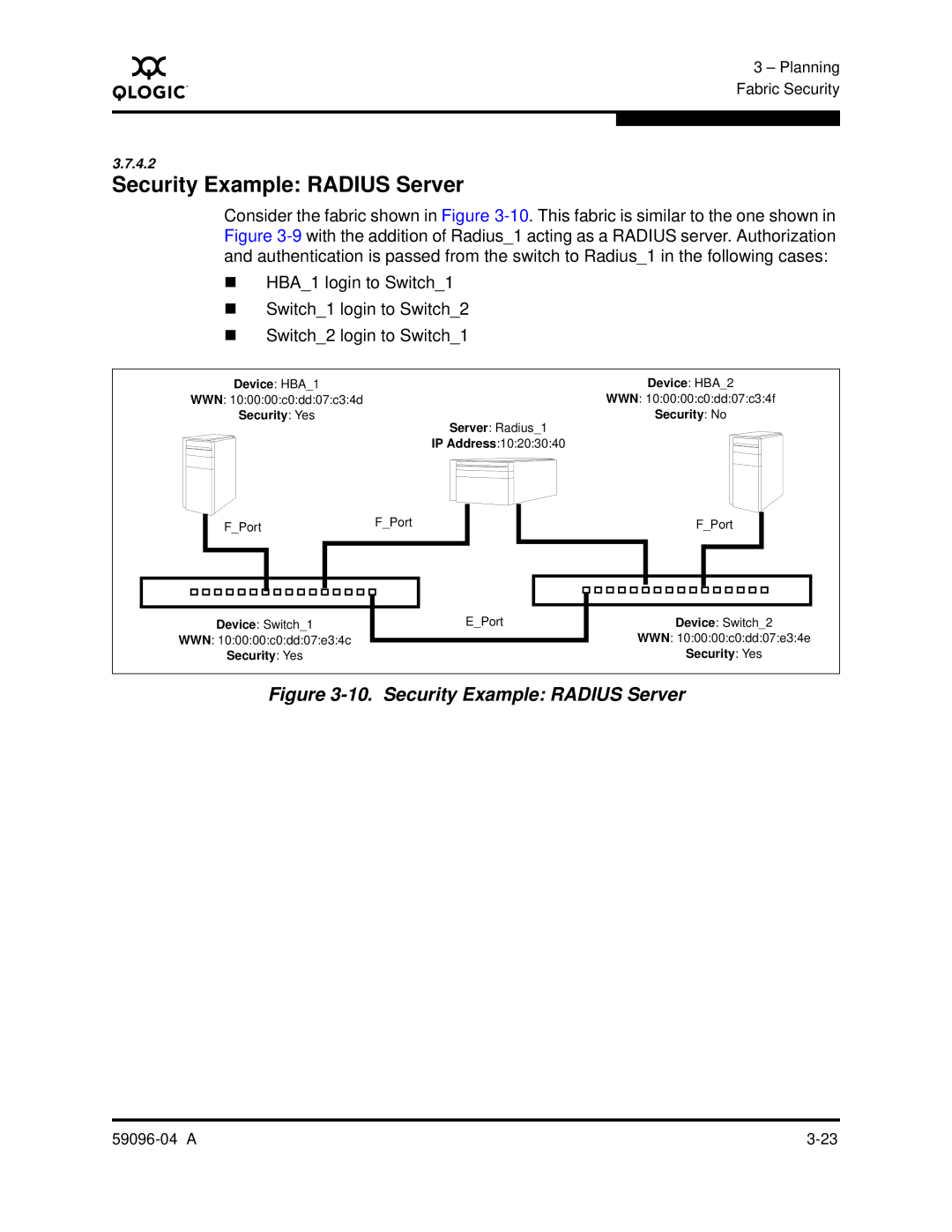
Security Example: RADIUS Server
Consider the fabric shown in Figure
HBA_1 login to Switch_1
Switch_1 login to Switch_2
Switch_2 login to Switch_1
Device: HBA_1 | Device: HBA_2 |
WWN: 10:00:00:c0:dd:07:c3:4d | WWN: 10:00:00:c0:dd:07:c3:4f |
Security: Yes | Security: No |
| Server: Radius_1 |
| IP Address:10:20:30:40 |
F_Port | F_Port |
| |
Device: Switch_1 | E_Port |
WWN: 10:00:00:c0:dd:07:e3:4c |
|
Security: Yes |
|
F_Port |
Device: Switch_2
WWN: 10:00:00:c0:dd:07:e3:4e
Security: Yes