NXA-ENET24
AMX Limited Warranty and Disclaimer
Table of Contents
Saving or Restoring Configuration Settings
Setting the IP Address
Console Port Settings
Telnet Settings
Setting the System Clock
Resetting the System
Setting the Time Zone
Setting Community Access Strings
Configuring SNMPv3 Groups
Configuring SNMPv3 Users
Setting SNMPv3 Views
Overview Configuring User Accounts
Configuring 802.1x Port Authentication
Configuring Port Security
Displaying and Configuring the 802.1x Global Setting
Configuring Port Settings for
Configuring an IP ACL Mask
Configuring ACL Masks
Configuring a MAC ACL Mask
Configuring Interface Connections
Configuring Port Mirroring
Statically Configuring a Trunk
Showing Port Statistics 100
Overview 109
Overview 105
Overview 113
Private VLANs 132
Overview Ieee 802.1Q VLANs 123
Overview 137
Overview 149
Multicast Filtering 149
Command Groups 164 Line Commands 165
Entering Commands 160
Overview 155
System Management Commands 171
General Commands 169
Authentication Commands 199
Flash/File Commands 193
196
Radius Client 200
802.1x Port Authentication 205
Port Security Commands 203
Access Control List Commands 209
IP ACL Commandss 210
Mirror Port Commands 237
Interface Commands 231
Link Aggregation Commands 239
238
Configuring Private VLANs 259
Vlan Commands 255
Gvrp and Bridge Extension Commands 262
Priority Commands 264
IP Interface Commands 275
Multicast Filtering Commands 271
DNS Commands 278
Table of Contents Xviii NXA-ENET24 Software Management Guide
Key Features
Key Features
Feature Description
Static and dynamic address configuration, proxy ARP
Description of Software Features
Introduction
Software Specifications
Software Specifications
Software Features
Power Over Ethernet
Management Features
Sntp RFC SSH Version
Standards
SNMP-MPD MIB RFC
Management Information Bases
System Defaults
System Defaults
Function Parameter Default
Lacp
Additional Documentation
Clock Synchronization Disabled
Connecting to the Switch
Initial Configuration
Configuration Options
Remote Connections
Required Connections
Setting Passwords
Basic Configuration
Setting an IP Address
Console Connection
Dynamic Configuration
Manual Configuration
Community Strings
Enabling Snmp Management Access
Managing System Files
Saving Configuration Settings
Trap Receivers
Dhcp Relay
Configuring Power over Ethernet
Initial Configuration NXA-ENET24 Software Management Guide
Overview
Web Interface
Navigating the Web Browser Interface
Home
Configuration Options
Button Action
Panel Display
Switch Main Menu
Main Menu
Port
Menu Description Security
Address Table
Menu PoE Description
Spanning Tree
Private Vlan
Vice value
Menu Description Priority
Igmp Snooping
Displaying System Information
Basic Configuration
Displaying System Information Web
Field Attributes
Displaying System Information CLI
Displaying Switch Hardware/Software Versions
Field Attributes
Displaying Switch Hardware/Software Versions CLI
Displaying Switch Hardware/Software Versions Web
Displaying Bridge Extension Capabilities
Displaying Bridge Extension Capabilities Web
Setting the IP Address
Displaying Bridge Extension Capabilities CLI
Manual Configuration Web
Command Attributes
Manual Configuration CLI
Command Attributes
Using DHCP/BOOTP CLI
Using DHCP/BOOTP Web
Renewing Dchp
Downloading System Software from a Server Web
Managing Firmware
File Transfer Method
File Name
Deleting Files
Downloading System Software from a Server CLI
Command Usage
Saving or Restoring Configuration Settings
PoE controller PDController file
Downloading Configuration Settings from a Server CLI
Downloading Configuration Settings from a Server Web
233
Console Port Settings
Console Port Settings CLI
Console Port Settings Web
Telnet Settings Web
Telnet Settings
For specific user-name accounts the default
Enabling Telnet CLI
Telnet Settings CLI
System Log Configuration
Configuring Event Logging
Logging Levels
Logging Levels
System Log Configuration Web
Remote Logs Configuration
System Log Configuration CLI
Remote Logs Configuration CLI
Remote Logs Configuration Web
Displaying Log Messages
Displaying Log Messages Web
Displaying Log Messages CLI
Sending Smtp Alerts
Sending Smpt Alerts CLI
Sending Smpt Alerts Web
Setting the System Clock
Resetting the System
Resetting the System Web
Resetting the System CLI
Setting the System Clock CLI
Setting the Time Zone
Setting the Time Zone Web
Setting the Time Zone CLI
Page
SNMPv3 Security Models and Levels
Snmp Protocol
SNMPv3 Security Models and Levels
Model Level Group Read View Write View Security
Setting Community Access Strings Web
Setting Community Access Strings
Enabling Snmp
Enabling Snmp Web
Specifying Trap Managers and Trap Types
Setting Community Access Strings CLI
Specifying Trap Managers and Trap Types Web
Specifying Trap Managers and Trap Types CLI
Setting an Engine ID
Configuring SNMPv3 Management Access
Configuring SNMPv3 Users
Setting an Engine ID Web
Configuring SNMPv3 Users CLI
Configuring SNMPv3 Users Web
Configuring SNMPv3 Groups Web
Configuring SNMPv3 Groups
Configuring SNMPv3 Groups CLI
Setting SNMPv3 Views Web
Setting SNMPv3 Views
Type
From the Snmp view
295
Setting SNMPv3 Views CLI
Configuring User Accounts
User Authentication
Configuring User Accounts Web
Configuring User Accounts CLI
Configuring Local/Remote Logon Authentication
Command Attributes
Authentication Settings CLI
Authentication Settings Web
Https Support
Configuring Https
Https Support
Internet Explorer 5.0 or later
Configuring the Secure Shell
Replacing the Default Secure-Site Certificate
Configuring Https Web
Configuring Https CLI
Switch supports both SSH Version 1.5
Generating the Host Key Pair
Configuring the Secure Shell Web
Configuring the Secure Shell CLI
Configuring the SSH Server
Timeout
Range 1 to 120 seconds
Configuring the SSH Server Web
Configuring Port Security
Configuring the SSH Server CLI
Configuring Port Security CLI
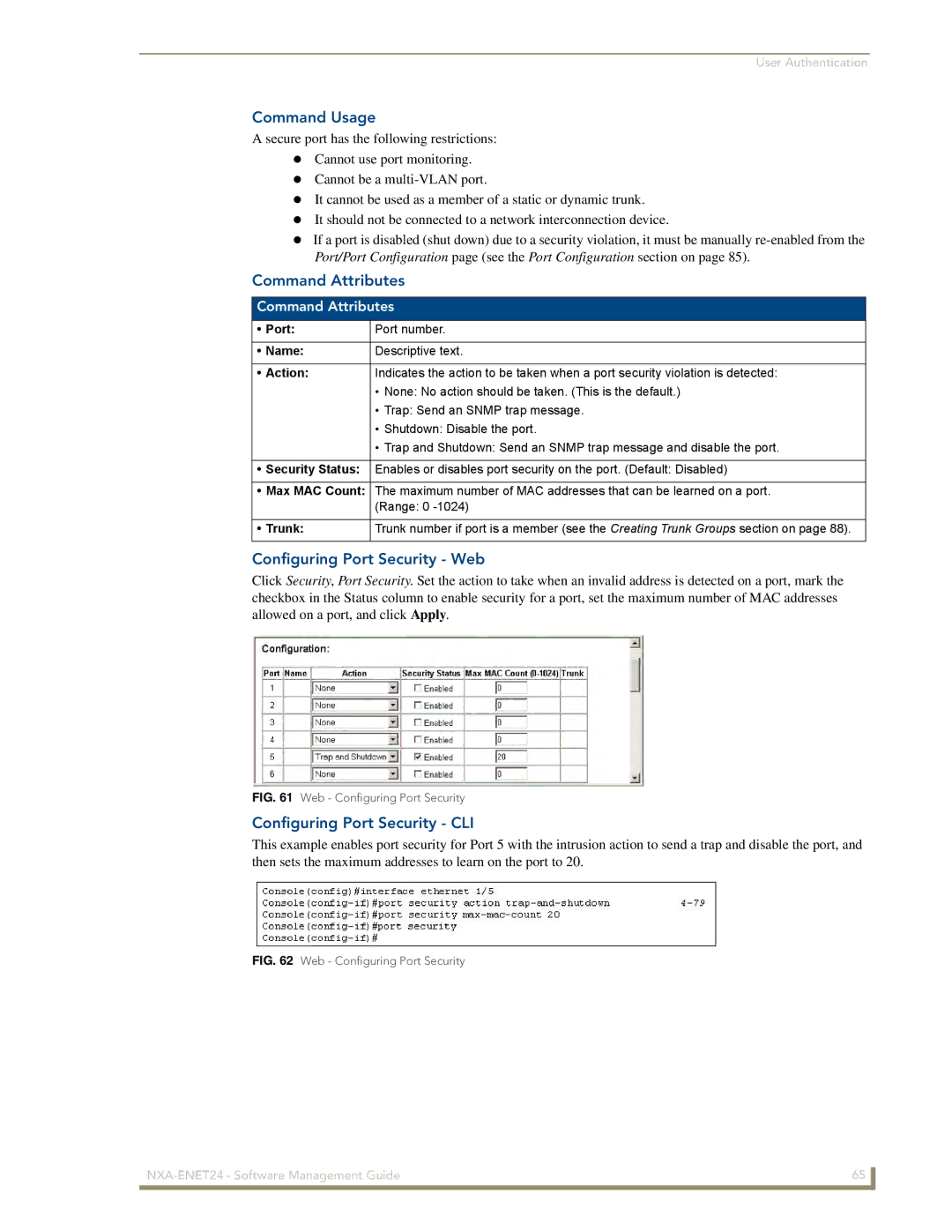
Configuring Port Security Web
Port Port number Name Descriptive text
Requirements
Configuring 802.1x Port Authentication
Configuring Port Settings for
Displaying and Configuring the 802.1x Global Setting
Displaying and Configuring the 802.1x Global Setting Web
Displaying and Configuring the 802.1x Global Setting CLI
Configuring Port Settings for 802.1x Web
CLI 802.1x Port Configuration
Configuring Port Settings for 802.1x CLI
Displaying 802.1x Statistics Web
Displaying 802.1x Statistics
802.1x Statistics
Parameter Description
Displaying 802.1x Statistics CLI
Filtering Addresses for Snmp Client Access
Filtering Addresses for Snmp Client Access CLI
Filtering Addresses for Snmp Client Access Web
Configuring Access Control Lists
Configuring ACLs
Setting the ACL Name and Type
Name Type
Setting the ACL Name and Type Web
Configuring a Standard IP ACL
Setting the ACL Name and Type CLI
Configuring a Standard IP ACL CLI
Configuring a Standard IP ACL Web
Configuring an Extended IP ACL Command Attributes
Configuring an Extended IP ACL CLI
Configuring an Extended IP ACL Web
Configuring a MAC ACL Web
Configuring a MAC ACL
Configuring a MAC ACL CLI
Configuring ACL Masks
Specifying the Mask Type
Configuring ACL Masks Web
Configuring an IP ACL Mask
Configuring ACL Masks CLI
Control flags of rule must match this bitmask
Configuring an IP ACL Mask Web
Configuring a MAC ACL Mask
Configuring an IP ACL Mask CLI
Configuring a MAC ACL Mask CLI
Configuring a MAC ACL Mask Web
Binding a Port to an Access Control List Web
Mapping ACLs to Port Ingress/Egress Queues
Binding a Port to an Access Control List CLI
Filtering IP Addresses for Management Access Web
Filtering IPs for Management Access
198
Filtering IP Addresses for Management Access CLI
Displaying Connection Status Web
Port Configuration
Field Attributes CLI
Field Attributes Web
Current status
Displaying Connection Status CLI
Admin
Configuring Interface Connections
Configuring Interface Connections CLI
Configuring Interface Connections Web
Creating Trunk Groups
Statically Configuring a Trunk Web
Statically Configuring a Trunk
New
Unit
Member List Current Shows configured trunks Unit, Port
Statically Configuring a Trunk CLI
Enabling Lacp on Selected Ports
Unit Stack unit. Range
Enabling Lacp on Selected Ports CLI
Enabling Lacp on Selected Ports Web
Dynamically Creating a Port Channel
Admin Key
System Priority
Port Priority
Dynamically Creating a Port Channel CLI
Dynamically Creating a Port Channel Web
Displaying Lacp Port Counters Web
Displaying Lacp Port Counters
Displaying Lacp Port Counters CLI
Counter Information Fields
Displaying Lacp Settings and Status for the Local Side Web
Displaying Lacp Settings and Status for the Local Side
Displaying Lacp Local Settings
Admin State
Displaying Lacp Settings and Status for the Local Side CLI
Displaying Lacp Settings and Status for the Remote Side
Displaying Lacp Settings and Status for the Remote Side Web
Displaying Lacp Settings and Status for the Remote Side CLI
Setting Broadcast Storm Thresholds
Threshold
Setting Broadcast Storm Thresholds Web
Configuring Port Mirroring
Setting Broadcast Storm Thresholds CLI
Configuring Port Mirroring Web
Configuring Rate Limits
Configuring Port Mirroring CLI
Rate Limit
Configuring Rate Limits CLI
Configuring Rate Limits Web
Showing Port Statistics
Port Statistics
Transmit Multicast
Transmit Unicast
Etherlike Statistics
Frames More than one collision
Oversize Frames
Showing Port Statistics Web
Byte Frames But including FCS octets
This example shows statistics for port
Showing Port Statistics CLI
Port Configuration 104 NXA-ENET24 Software Management Guide
Switch Power Status
Power Over Ethernet PoE Settings
Switch Power Status Web
Setting a Switch Power Budget
Switch Power Status CLI
Setting a Switch Power Budget Web
Setting a Switch Power Budget CLI
Displaying Port Power Status CLI
Displaying Port Power Status Web
Configuring Port PoE Power
Configuring Port PoE Power CLI
Configuring Port PoE Power Web
Setting Static Addresses
Address Table Settings
Setting Static Addresses Web
Setting Static Addresses CLI
Displaying the Address Table Web
Displaying the Address Table
Displaying the Address Table CLI
Changing the Aging Time
Changing the Aging Time CLI
Changing the Aging Time Web
Page
Spanning Tree Algorithm Configuration
Spanning Tree Algorithm Configuration
These additional parameters are only displayed for the CLI
Displaying Global Settings
Configuring Global Settings
Displaying Global Settings Web
Command Attributes Root Device Configuration
Command Attributes Basic Configuration of Global Settings
Root device
Range 0-61440, in steps
Configuring Global Settings CLI
Configuring Global Settings Web
Configuration Settings for Rstp
Displaying Interface Settings
Ing network loops
Numeric identifier will be enabled
Displaying Interface Settings CLI
Displaying Interface Settings Web
Configuring Interface Settings
Enables/disables spanning tree on a port
Web Configuring Spanning Tree per Port
Configuring Interface Settings Web
Configuring Interface Settings CLI
Overview Ieee 802.1Q VLANs
Vlan Configuration
Assigning Ports to VLANs
124 NXA-ENET24 Software Management Guide
Forwarding Tagged/Untagged Frames
Enabling or Disabling Gvrp Global Setting
Enabling or Disabling Gvrp Web
Enabling or Disabling Gvrp CLI
Command Attributes CLI
Command Attributes Web
Displaying Basic Vlan Information CLI
Displaying Current VLANs
Creating VLANs
Displaying Current VLANs CLI
Creating VLANs Web
Adding Static Members to VLANs Vlan Index
Creating VLANs CLI
Adding Static Members to VLANs CLI
Adding Static Members to VLANs Web
Adding Static Members to VLANs Port Index
Configuring Vlan Behavior for Interfaces
Configuring Vlan Behavior for Interfaces CLI
Configuring Vlan Behavior for Interfaces Web
Timer
Group
Displaying Current Private VLANs
Private VLANs
Displaying Current Private VLANs Web
Configuring Private VLANs Web
Configuring Private VLANs
Configuring Private VLANs CLI
Displaying Current Private VLANs CLI
Associating Community VLANs CLI
Associating Community VLANs Web
Displaying Private Vlan Interface Information
Displaying Private Vlan Interface Information Web
Configuring Private Vlan Interfaces Web
Configuring Private Vlan Interfaces
Displaying Private Vlan Interface Information CLI
CLI Private Vlan Port Configuration
Configuring Private Vlan Interfaces CLI
Setting the Default Priority for Interfaces
Class of Service Configuration
Setting the Default Priority for Interfaces Web
Mapping CoS Values to Egress Queues
Setting the Default Priority for Interfaces CLI
Egress Queue Priority Mapping
CoS Priority Levels
Mapping CoS Values to Egress Queues Web
Selecting the Queue Mode
Mapping CoS Values to Egress Queues CLI
Selecting the Queue Mode CLI
Selecting the Queue Mode Web
Setting the Service Weight for Traffic Classes
Setting the Service Weight for Traffic Classes Web
Selecting IP Precedence/DSCP Priority
Mapping Layer 3/4 Priorities to CoS Values
Selecting IP Precedence/DSCP Priority Web
Selecting IP Precedence/DSCP Priority CLI
Mapping IP Precedence CLI
Mapping IP Precedence Web
Mapping Dscp Priority Web
Mapping Dscp Priority
Mapping Dscp Priority Values
IP Dscp Value CoS Value
Mapping IP Port Priority
Mapping Dscp Priority CLI
Mapping IP Port Priority Web
Priority Settings
Copy Settings
Copy Settings Carries out the command
Mapping IP Port Priority CLI
Copy Settings CLI
Copy Settings Web
Mapping CoS Values to ACLs
CoS to ACL Mapping
Mapping CoS Values to ACLs CLI
Mapping CoS Values to ACLs Web
Changing Priorities Based on ACL Rules
Port Port identifier Name Name of ACL
Changing Priorities Based on ACL Rules CLI
Changing Priorities Based on ACL Rules Web
Layer 2 Igmp Snooping and Query
Multicast Filtering
Configuring Igmp Snooping and Query Parameters
Configuring Igmp Snooping and Query Parameters CLI
Configuring Igmp Snooping and Query Parameters Web
Displaying Interfaces Attached to a Multicast Router
Displaying Interfaces Attached to a Multicast Router CLI
Displaying Interfaces Attached to a Multicast Router Web
Specifying Interfaces Attached to a Multicast Router
Specifying Interfaces Attached to a Multicast Router Web
Displaying Port Members of Multicast Services Web
Displaying Port Members of Multicast Services
Displaying Port Members of Multicast Services CLI
Assigning Ports to Multicast Services
Assigning Ports to Multicast Services CLI
Assigning Ports to Multicast Services Web
Configuring General DNS Server Parameters
Configuring Domain Name Service
Configuring General DNS Server Parameters CLI
Configuring General DNS Server Parameters Web
Configuring Static DNS Host to Address Entries
Configuring Static DNS Host to Address Entries CLI
Configuring Static DNS Host to Address Entries Web
Displaying the DNS Cache
Displaying the DNS Cache CLI
Displaying the DNS Cache Web
Using the Command Line Interface
CLI Command Line Interface
Console Connection
Telnet Connection
Command Completion
Entering Commands
Keywords and Arguments
Minimum Abbreviation
Showing Commands
Getting Help on Commands
Using Command History
Negating the Effect of Commands
Understanding Command Modes
Exec Commands
Command Line Processing
Configuration Commands
Configuration Commands
Keystroke Commands
Command Group Index
Command Groups
Line Commands
Line Commands
Login Syntax
Command Usage
Command Function Password Syntax
Timeout login Syntax Response
Default Setting
Silent-time Syntax
Command Function Password-thresh Syntax
Databits Syntax
Stopbits Syntax
Speed Syntax
Disconnect Syntax
General Commands
General Commands
Disable Default Setting None
Show history Default Setting None
Command Function Configure Default Setting None
Reload Default Setting None
End Default Setting None
System Management Commands
System Management Commands
Quit Default Setting None
Help
User Access Commands
Device Designation Commands
Device Designation Commands
User Access Commands
IP Filter Commands
IP Filter Commands
Enable password Syntax
Command Function Management Command Usage Cont
Web Server Commands
Web Server Commands
Command Function Ip http port Syntax
Default Setting Enabled
Secure Shell Commands
Telnet Server Commands
Telnet Server Commands
Show calendar
To Use the SSH Server
Ip ssh timeout Syntax
Secure Shell Commands
Ip ssh authentication Syntax Retries
Ip ssh server-key size Syntax
Delete public-key Syntax
Command Function Copy tftp public-key
Ip ssh crypto host-key Syntax Generate
Ip ssh crypto zeroize Syntax
Show ssh
Command Function Show ip ssh
Show ssh display description Field Description
Event Logging Commands
Event Logging Commands
Command Function Show public-key Syntax
Command Function Logging on Syntax
Logging Levels Severity Name Description
Command Function Logging history Syntax
Logging host Syntax
Default Setting Flash and RAM
Command Function Logging facility Syntax
Logging trap Syntax
Clear logging Syntax
Field Description
Command Function Show logging Syntax
Smtp Alert Commands
Smtp Alert Commands
Command Function Show log Syntax
Command Function Logging sendmail host Syntax
Logging sendmail source-email Syntax
Command Function Logging sendmail level Syntax
Logging sendmail destination Syntax
Logging sendmail Syntax
Time Commands
Time Commands
Command Function Show logging sendmail
Command Function Sntp client Syntax
Default Setting 16 seconds
Command Function Sntp poll Syntax
Show sntp
Clock timezone Syntax
System Status Commands
System Status Commands
Command Function Show calendar Default Setting None
Command Function Light unit Syntax
Information currently
Command Function Show startup-config
Show system Default Setting None
Command Function
Show version Default Setting None
Command Function Show users Default Setting None
Telnet client
Flash/File Commands
Flash/File Commands
Command Function Copy Syntax
Delete Syntax
Command Function Copy Example Cont
Whichboot Syntax
Command Function Dir Syntax
When the system Command Mode Privileged Exec Powered up
PoE Commands
Power over Ethernet PoE Commands
Command Function Boot system
Default Setting 375 watts
Default Setting auto
Command Function Power inline Syntax
Power inline maximum Syntax Allocation
Power inline priority Syntax
Show power mainpower
Command Function Show power inline status Syntax
Authentication Commands
Authentication Commands
Command Function Authentication login Syntax
Default Setting Local
Radius Client
Radius Client Commands
Radius-server port Syntax
Radius-server key Syntax
Show radius-server Default Setting None
Radius-server timeout Syntax
Show tacacs-server Default Setting None
TACACS+ Client Commands
TACACS+ Client
Tacacs-server port Syntax
Port Security Commands
Port Security Commands
Command Function Port security Syntax
Show mac-address-table Syntax
Command Function Mac-address-table static Syntax
802.1x Port Authentication Commands
802.1x Port Authentication
Dot1x default Syntax
Dot1x max-req Syntax
Dot1x re-authenticate Syntax
Command Function Dot1x port-control Syntax
Dot1x re-authentication Syntax
Dot1x operation-mode Syntax
Dot1x timeout re-authperiod Syntax
Command Function Dot1x timeout quiet-period Syntax
Dot1x timeout tx-period Syntax
Show dot1x Syntax
Command Function Show dot1x
Access Control Lists
Access Control List Commands
Command Function Show dot1x
Masks for Access Control Lists
IP ACL Commandss
IP ACL Commands
Command Function Access-list ip Syntax
Permit, deny Syntax Extended ACL
Command Function Permit, deny Syntax Standard ACL
Ignore a bit. The following bits may be specified
Command Function Permit, deny
SYN flag valid, use control-code 2
Both SYN and ACK valid, use control-code 18
Command Mode IP Mask
Command Function Show ip access-list Syntax
Mask Syntax
IP ACL
Command Function Mask
Command Function Mask Example IP ACL
Ip access-group Syntax
Command Function Show access-list ip mask Syntax Precedence
Show ip access-group
Map access-list ip Syntax
Match access-list ip Syntax
Command Function Show map access-list ip Syntax
Show marking
MAC ACL Commands
MAC ACL Commands
Command Function Access-list mac Syntax
Command Mode MAC ACL
Access-list mac mask Syntax Precedence
Command Function Show mac access-list Syntax
Command Mode MAC Mask
Command Function Mask Syntax
MAC ACLs. This mask defines
Egress ACL
Permit offset, deny offset Syntax
Show access-list mac mask Syntax Precedence
Show mac access-group
Command Function Mac access-group Syntax
Map access-list mac Syntax
Show map access-list mac Syntax
Command Function Show access-list
Command Function Match access-list mac Syntax
Show access-group
ACL Information
Snmp Commands
Snmp Commands
Command Function Snmp-server Default Setting Enabled
Show snmp Default Setting None
Snmp-server contact Syntax
Command Function Snmp-server community Syntax
Snmp-server location Syntax
Command Function Snmp-server host Syntax
Show snmp engine-id
Command Function Snmp-server engine-id Syntax
Snmp-server view Syntax
Snmp-server group Syntax
Command Function Show snmp view
Command Function Show snmp group
Show snmp user
Command Function Snmp-server user Syntax
Interface Commands
Interface Commands
Command Function Interface Syntax
Description Syntax
Capabilities Syntax
Command Function Negotiation Syntax
Switchport broadcast Syntax Packet-rate
Command Function Flowcontrol Syntax
Shutdown Syntax
Power reset
Command Function Clear counters Syntax
Example The following example clears statistics on port
Show interfaces status Syntax
NXA-ENET24 Software Management Guide 235
Interfaces Switchport Statistics
Command Function Show interfaces Syntax Switchport
Mirror Port Commands
Mirror Port Commands
Command Function Port monitor Syntax
Show port monitor
Rate Limit Commands
Rate Limit Commands
Command Function Rate-limit Syntax
Link Aggregation Commands
Link Aggregation Commands
Guidelines for Creating Trunks
Channel-group Syntax
Use the no form to disable it
Command Function Dynamic Configuration Commands Lacp
Lacp admin-key Syntax Ethernet Interface
Command Function Lacp system-priority Syntax
Lacp port-priority Syntax
Command Function Lacp admin-key Syntax Port Channel
Port-channel Show lacp Syntax
Show interfaces status
Command Function Show lacp Example
NXA-ENET24 Software Management Guide 245
Address Table Commands
Address Table Commands
Clear mac-address-table Default Setting None Dynamic
Default Setting 300 seconds
Command Function Show mac-address-table Syntax
Show mac-address-table Default Setting None Aging-time
Time
Spanning Tree Commands
Spanning Tree Commands
Command Function Spanning-tree Syntax
Spanning-tree mode Syntax
Spanning-tree max-age Syntax
Spanning-tree hello-time Syntax
Default Setting Long method
Command Function Spanning-tree priority Syntax
Spanning-tree spanning Syntax Disabled
Spanning-tree pathcost Syntax Method
Spanning-tree port-priority Syntax
Command Function Spanning-tree cost Syntax
Spanning-tree portfast Syntax
Command Function Spanning-tree edge-port Syntax
Link type for Rapid Spanning
Command Function Spanning-tree link-type Syntax
Nate a port as a shared link, Rstp is forbidden
Spanning-tree protocol Syntax Migration
Rstp
Command Function Show spanning-tree Syntax
Command Function Vlan database Default Setting None
Vlan Commands
Editing Vlan Groups
Editing Vlan Groups
Configuring Vlan Interfaces
Configuring Vlan Interfaces
Command Function Interface vlan Syntax
Switchport mode Syntax
Switchport native vlan Syntax
Command Function Switchport ingress-filtering Syntax
Default Setting Vlan
Switchport gvrp
Command Function Switchport allowed vlan Syntax
Switchport forbidden vlan Syntax
Switchport priority default
Command Function Show vlan Syntax
Configuring Private VLANs
Displaying Vlan Information
Displaying Vlan Information
Edit Private Vlan Groups
Command Function Private-vlan Syntax
Edit Private Vlan Groups
Private vlan association Syntax
Configure Private Vlan Interfaces
Configure Private Vlan Interfaces
Switchport private-vlan host Syntax Association
Switchport private-vlan mapping Syntax
Gvrp and Bridge Extension Commands
Gvrp and Bridge Extension Commands
Show bridge-ext Default Setting None
Display Private Vlan Information
Switchport forbidden vlan
Command Function Switchport gvrp Syntax
Show gvrp configuration Syntax
Garp timer Syntax
Priority Commands Layer
Priority Commands
Priority Commands Layer
Show queue mode Default Setting None
Command Function Switchport priority Syntax Default
Priority Commands Layer 2
Queue bandwidth Syntax
Show queue bandwidth Default Setting None
Command Function Queue cos-map Syntax
Show queue cos-map Syntax
Priority Commands Layer 3
Priority Commands Layer 3
Map ip precedence Syntax Global Configuration
Map ip port Syntax
Command Function Map ip precedence
Priority Commands Layer 3 and 4-
Map ip dscp Syntax Global Configuration
Map access-list ip
Command Function Map ip dscp Syntax Interface Configuration
Map access-list mac
Show map ip port Syntax
Show map ip dscp Syntax
Igmp Snooping Commands
Multicast Filtering Commands
Igmp Snooping Commands
Ip igmp snooping vlan static Syntax
Igmp Query Commands Layer
Igmp Query Commands Layer
Command Function Show ip igmp snooping Default Setting None
Command Function Ip igmp snooping querier Syntax
Ip igmp snooping query-interval Syntax
Igmp Query Commands Layer 2
Ip igmp snooping query-max Syntax Response-time
Static Multicast Routing Commands
Static Multicast Routing Commands
Command Function Ip igmp snooping vlan mrouter Syntax
Show ip igmp snooping mrouter Syntax
IP Interface Commands
IP Interface Commands
Command Function Ip address Syntax
Default Setting Dhcp
Ip dhcp restart Default Setting None
Command Function Ip default-gateway Syntax
Show ip redirects Default Setting None
Show ip interface
Command Function Ping Syntax
DNS Commands
DNS Commands
Command Function Ip host Syntax
Clear host Syntax
Ip name-server Syntax
Command Function Ip domain-list Syntax
DNS host name-to
Command Function Ip domain-lookup Syntax
Show hosts
Show dns
Command Mode Privileged Exec This command clears all
Command Function Show dns cache
Entries in the DNS cache
Clear dns cache
Page
Troubleshooting Chart
Troubleshooting
Symptom Action
Cannot connect using Telnet
It’s Your World Take Control