Using the Web-Based Advanced User Interface
Table of Contents | sections | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
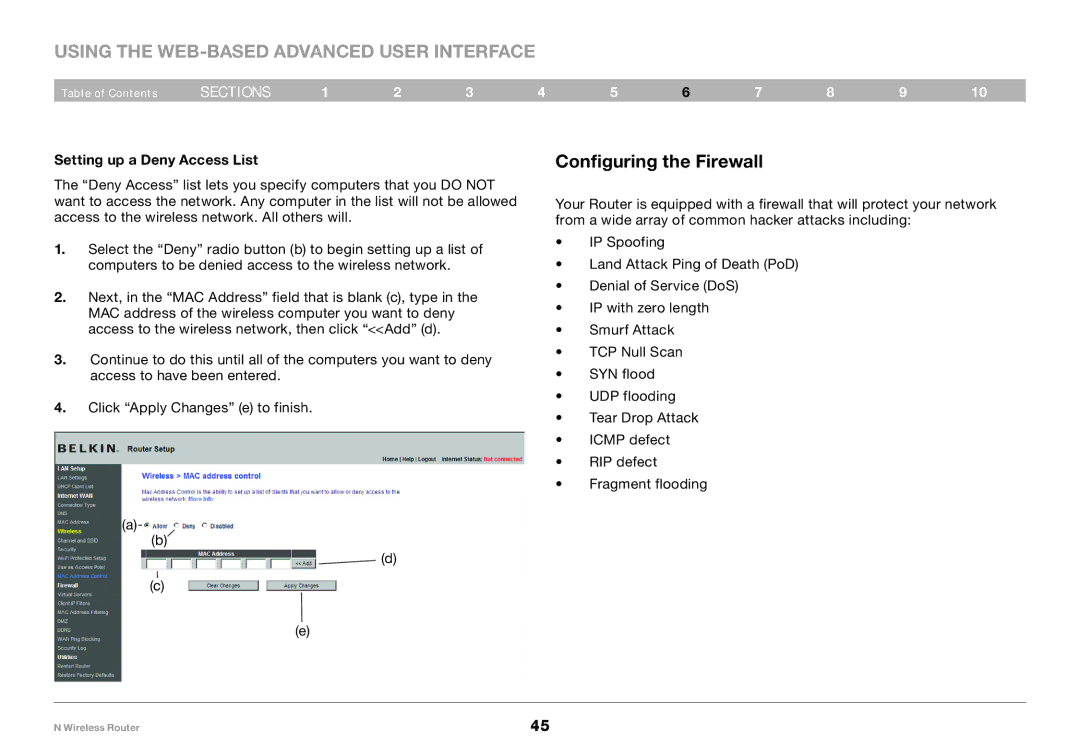
Setting up a Deny Access List
The “Deny Access” list lets you specify computers that you DO NOT want to access the network. Any computer in the list will not be allowed access to the wireless network. All others will.
1.Select the “Deny” radio button (b) to begin setting up a list of computers to be denied access to the wireless network.
2.Next, in the “MAC Address” field that is blank (c), type in the MAC address of the wireless computer you want to deny access to the wireless network, then click “<<Add” (d).
3.Continue to do this until all of the computers you want to deny access to have been entered.
4.Click “Apply Changes” (e) to finish.
(a)
(b)![]()
![]() (d)
(d)
(c)
Configuring the Firewall
Your Router is equipped with a firewall that will protect your network from a wide array of common hacker attacks including:
•IP Spoofing
•Land Attack Ping of Death (PoD)
•Denial of Service (DoS)
•IP with zero length
•Smurf Attack
•TCP Null Scan
•SYN flood
•UDP flooding
•Tear Drop Attack
•ICMP defect
•RIP defect
•Fragment flooding
(e)
N Wireless Router | 45 |