Ring Security Configuration
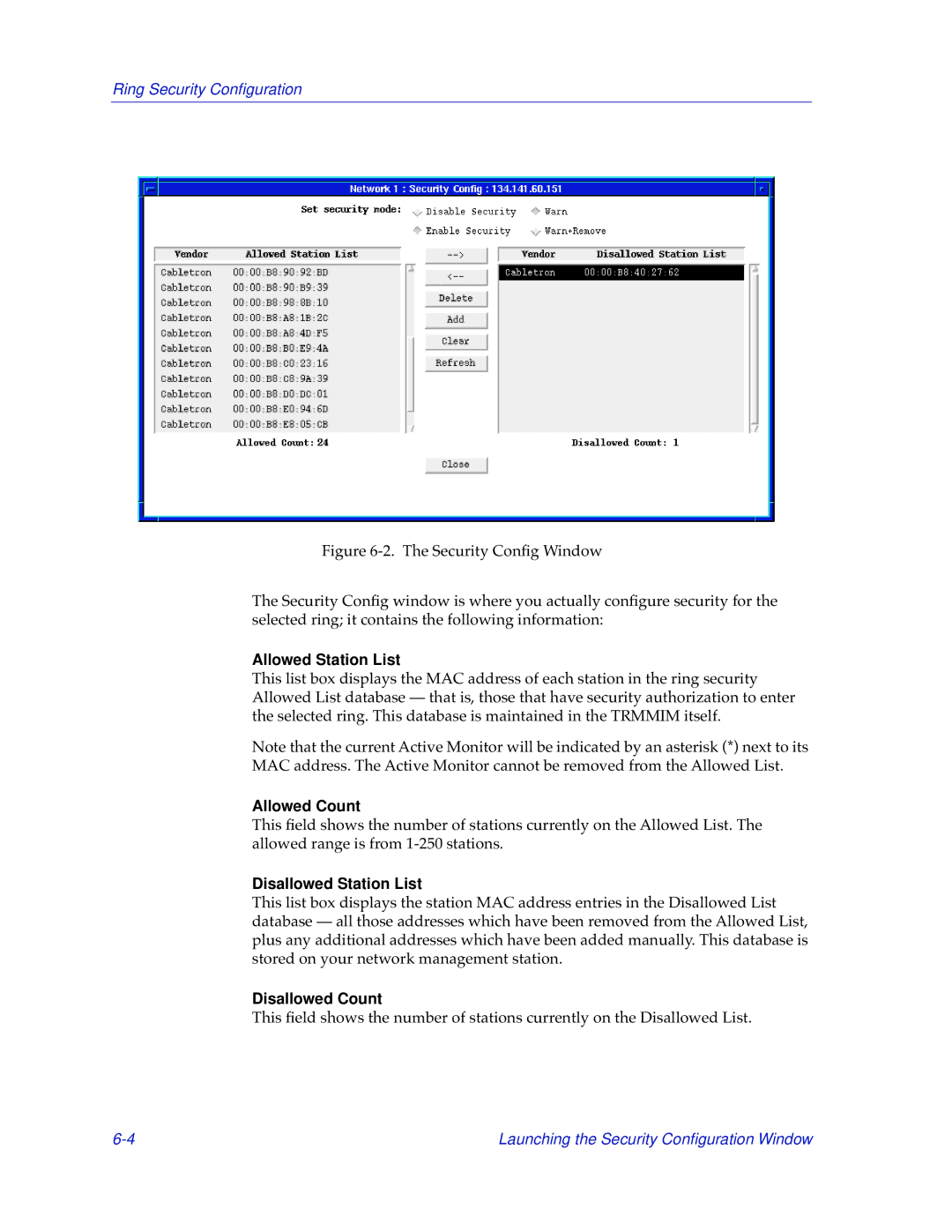
Figure 6-2. The Security Config Window
The Security Config window is where you actually configure security for the selected ring; it contains the following information:
Allowed Station List
This list box displays the MAC address of each station in the ring security Allowed List database — that is, those that have security authorization to enter the selected ring. This database is maintained in the TRMMIM itself.
Note that the current Active Monitor will be indicated by an asterisk (*) next to its MAC address. The Active Monitor cannot be removed from the Allowed List.
Allowed Count
This field shows the number of stations currently on the Allowed List. The allowed range is from
Disallowed Station List
This list box displays the station MAC address entries in the Disallowed List database — all those addresses which have been removed from the Allowed List, plus any additional addresses which have been added manually. This database is stored on your network management station.
Disallowed Count
This field shows the number of stations currently on the Disallowed List.
Launching the Security Configuration Window |