a secure connection that, in effect, operates as if you were directly connected to your local network. Virtual Private Networking can be used to create secure networks linking a central office with branch offices, telecommuters, and/or professionals on the road (travelers can connect to a VPN Router using any computer with VPN client software that supports IPSec, such as SSH Sentinel.)
There are two basic ways to create a VPN connection:
•VPN Router to VPN Router
•Computer (using VPN client software that supports IPSec) to VPN Router
The VPN Router creates a “tunnel” or channel between two endpoints, so that data transmissions between them are secure. A computer with VPN client software that supports IPSec can be one of the two endpoints. Any computer with the
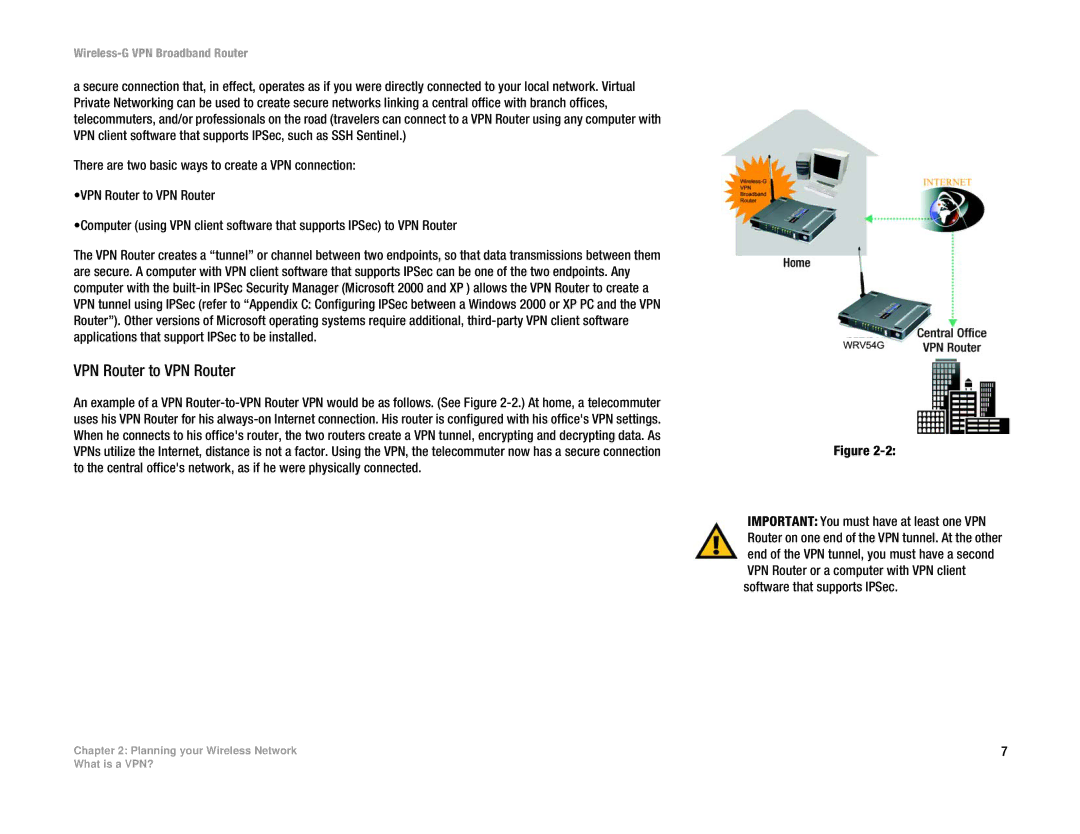
VPN Router to VPN Router
An example of a VPN
Chapter 2: Planning your Wireless Network
Figure
IMPORTANT: You must have at least one VPN Router on one end of the VPN tunnel. At the other end of the VPN tunnel, you must have a second VPN Router or a computer with VPN client software that supports IPSec.
7
What is a VPN?