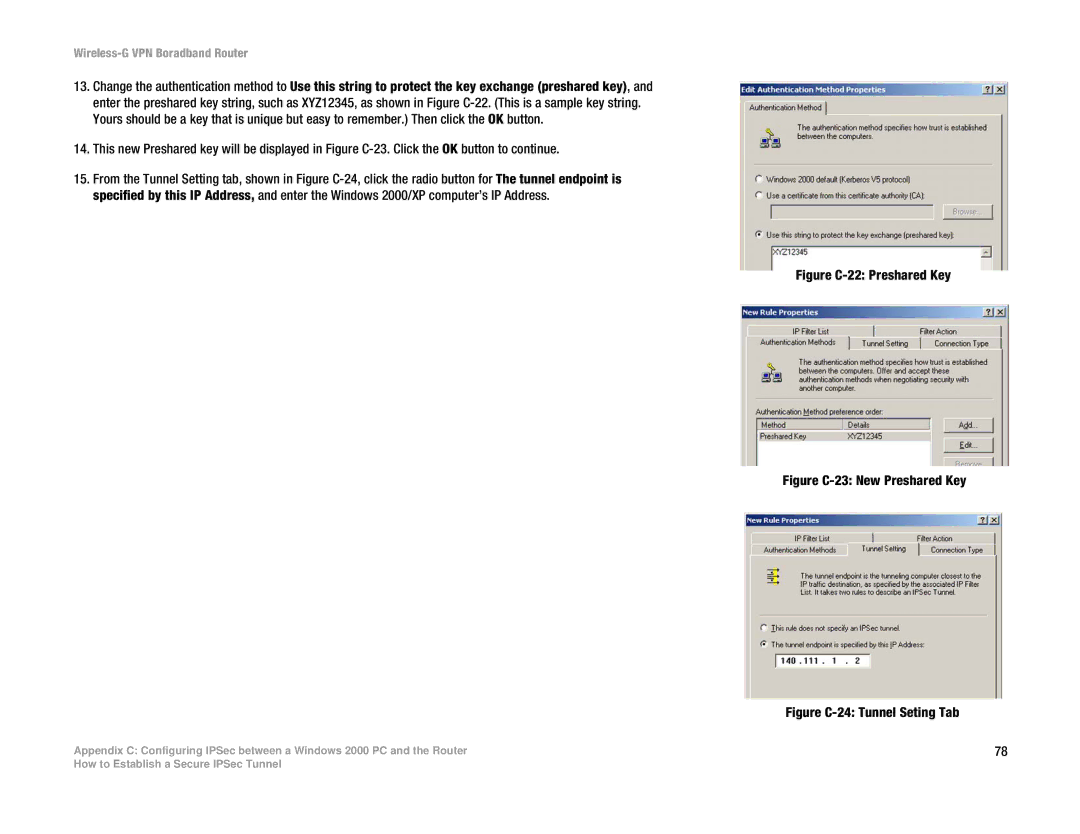
13.Change the authentication method to Use this string to protect the key exchange (preshared key), and enter the preshared key string, such as XYZ12345, as shown in Figure
14.This new Preshared key will be displayed in Figure
15.From the Tunnel Setting tab, shown in Figure
Appendix C: Configuring IPSec between a Windows 2000 PC and the Router
Figure C-22: Preshared Key
Figure C-23: New Preshared Key
Figure C-24: Tunnel Seting Tab
78
How to Establish a Secure IPSec Tunnel