Section 3 - Software Configuration
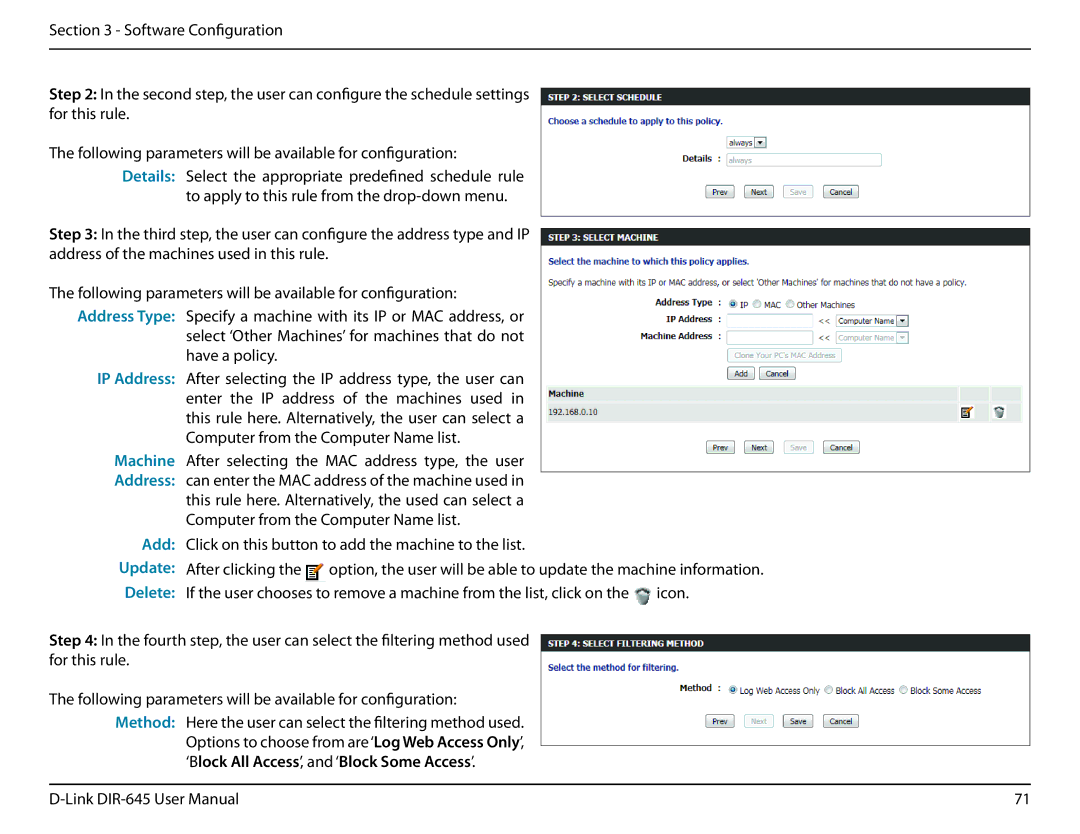
Step 2: In the second step, the user can configure the schedule settings for this rule.
The following parameters will be available for configuration:
Details: Select the appropriate predefined schedule rule to apply to this rule from the
Step 3: In the third step, the user can configure the address type and IP address of the machines used in this rule.
The following parameters will be available for configuration:
Address Type: Specify a machine with its IP or MAC address, or select ‘Other Machines’ for machines that do not have a policy.
IP Address: After selecting the IP address type, the user can enter the IP address of the machines used in this rule here. Alternatively, the user can select a Computer from the Computer Name list.
Machine After selecting the MAC address type, the user Address: can enter the MAC address of the machine used in this rule here. Alternatively, the used can select a
Computer from the Computer Name list.
Add: Click on this button to add the machine to the list.
Update: After clicking the ![]() option, the user will be able to update the machine information. Delete: If the user chooses to remove a machine from the list, click on the
option, the user will be able to update the machine information. Delete: If the user chooses to remove a machine from the list, click on the ![]() icon.
icon.
Step 4: In the fourth step, the user can select the filtering method used for this rule.
The following parameters will be available for configuration:
Method: Here the user can select the filtering method used. Options to choose from are‘Log Web Access Only’, ‘Block All Access’, and ‘Block Some Access’.
71 |