Factory default firewall configuration | Factory defaults |
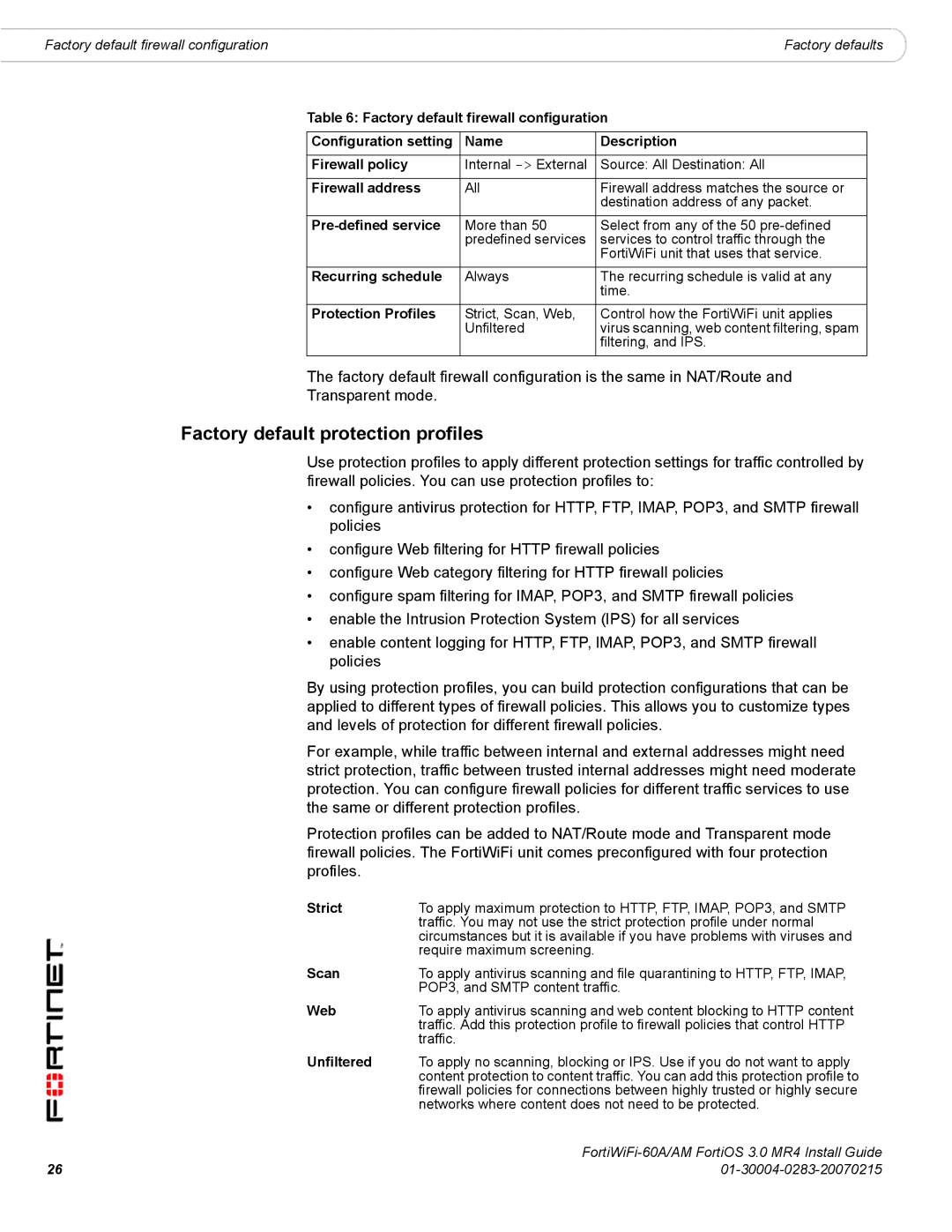
Table 6: Factory default firewall configuration
Configuration setting | Name | Description |
|
|
|
Firewall policy | Internal | Source: All Destination: All |
Firewall address | All | Firewall address matches the source or |
|
| destination address of any packet. |
|
|
|
| More than 50 | Select from any of the 50 |
| predefined services | services to control traffic through the |
|
| FortiWiFi unit that uses that service. |
|
|
|
Recurring schedule | Always | The recurring schedule is valid at any |
|
| time. |
|
|
|
Protection Profiles | Strict, Scan, Web, | Control how the FortiWiFi unit applies |
| Unfiltered | virus scanning, web content filtering, spam |
|
| filtering, and IPS. |
|
|
|
The factory default firewall configuration is the same in NAT/Route and
Transparent mode.
Factory default protection profiles
Use protection profiles to apply different protection settings for traffic controlled by firewall policies. You can use protection profiles to:
•configure antivirus protection for HTTP, FTP, IMAP, POP3, and SMTP firewall policies
•configure Web filtering for HTTP firewall policies
•configure Web category filtering for HTTP firewall policies
•configure spam filtering for IMAP, POP3, and SMTP firewall policies
•enable the Intrusion Protection System (IPS) for all services
•enable content logging for HTTP, FTP, IMAP, POP3, and SMTP firewall policies
By using protection profiles, you can build protection configurations that can be applied to different types of firewall policies. This allows you to customize types and levels of protection for different firewall policies.
For example, while traffic between internal and external addresses might need strict protection, traffic between trusted internal addresses might need moderate protection. You can configure firewall policies for different traffic services to use the same or different protection profiles.
Protection profiles can be added to NAT/Route mode and Transparent mode firewall policies. The FortiWiFi unit comes preconfigured with four protection profiles.
Strict | To apply maximum protection to HTTP, FTP, IMAP, POP3, and SMTP |
| traffic. You may not use the strict protection profile under normal |
| circumstances but it is available if you have problems with viruses and |
| require maximum screening. |
Scan | To apply antivirus scanning and file quarantining to HTTP, FTP, IMAP, |
| POP3, and SMTP content traffic. |
Web | To apply antivirus scanning and web content blocking to HTTP content |
| traffic. Add this protection profile to firewall policies that control HTTP |
| traffic. |
Unfiltered | To apply no scanning, blocking or IPS. Use if you do not want to apply |
| content protection to content traffic. You can add this protection profile to |
| firewall policies for connections between highly trusted or highly secure |
| networks where content does not need to be protected. |
|
26 |