Virtual names and addresses are the only identification used by clients on the network. Because the names and addresses are virtual, their ownership can transition from one node to the other during a failover, preserving access to the resources in the cluster group.
A cluster uses at least two network connections on each node:
•The private cluster interconnect or “heartbeat” crossover cable connects to one of the network ports on each cluster node. In more than two node deployments, a private VLAN on a switch or hub is required for the cluster interconnect.
•The public client network subnet connects to the remaining network ports on each cluster node. The cluster node names and virtual server names have IP addresses residing on these subnets.
![]() NOTE:
NOTE:
If the share is to remain available during a failover, each cluster node must be connected to the same network subnet. It is impossible for a cluster node to serve the data to a network to which it is not connected.
Protocol planning
Not all file sharing protocols can take advantage of clustering. If a protocol does not support clustering, it will not have a cluster resource and will not failover with any cluster group. In the case of a failover, a client cannot use the virtual name or virtual IP address to access the share since the protocol cannot failover with the cluster group. The client must wait until the initial node is brought back online to access the share.
HP recommends placing cluster aware and non cluster aware protocols on different file shares.
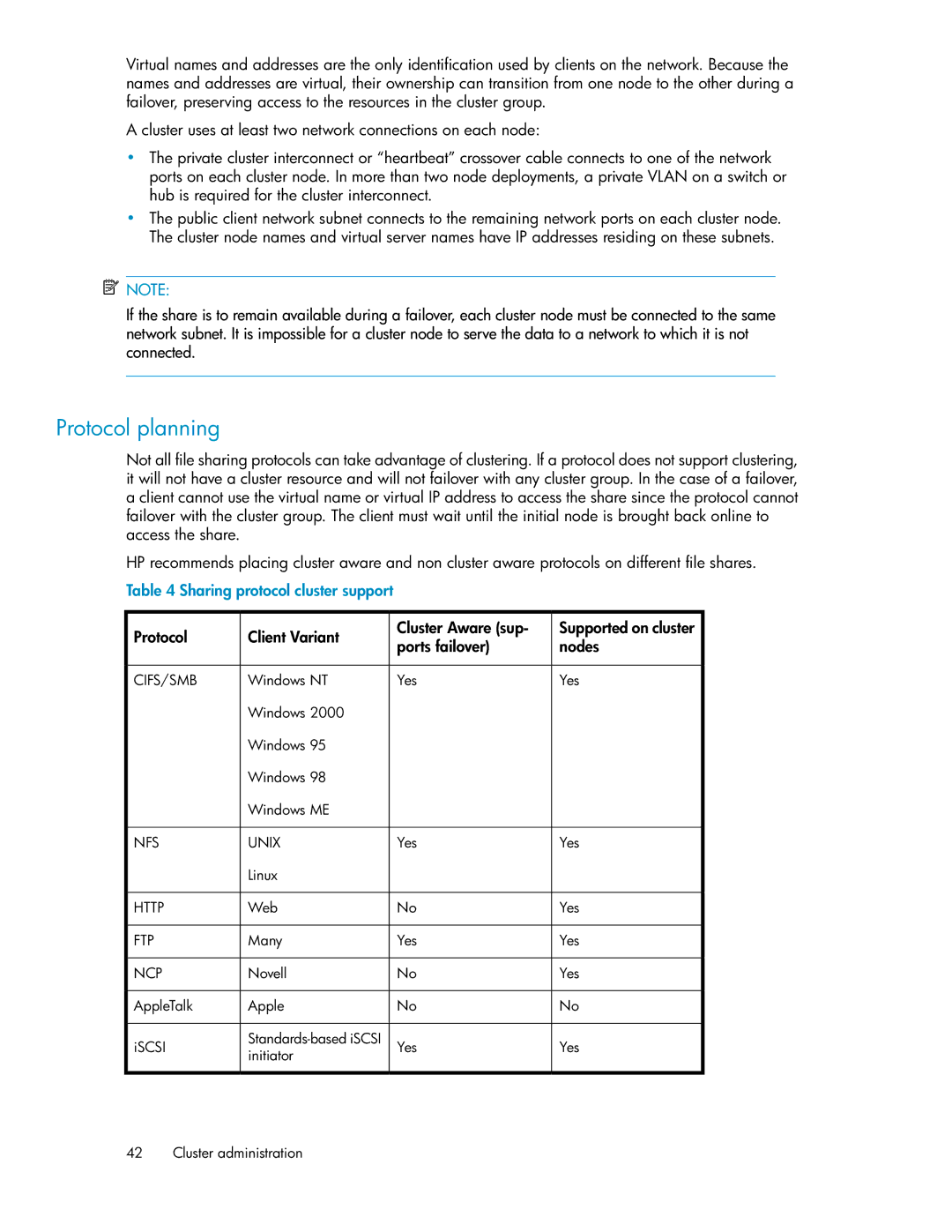
Table 4 Sharing protocol cluster support
Protocol | Client Variant | Cluster Aware (sup- | Supported on cluster | |
ports failover) | nodes | |||
|
| |||
CIFS/SMB | Windows NT | Yes | Yes | |
| Windows 2000 |
|
| |
| Windows 95 |
|
| |
| Windows 98 |
|
| |
| Windows ME |
|
| |
NFS | UNIX | Yes | Yes | |
| Linux |
|
| |
HTTP | Web | No | Yes | |
FTP | Many | Yes | Yes | |
NCP | Novell | No | Yes | |
AppleTalk | Apple | No | No | |
iSCSI | Yes | Yes | ||
initiator | ||||
|
|
|
42 Cluster administration