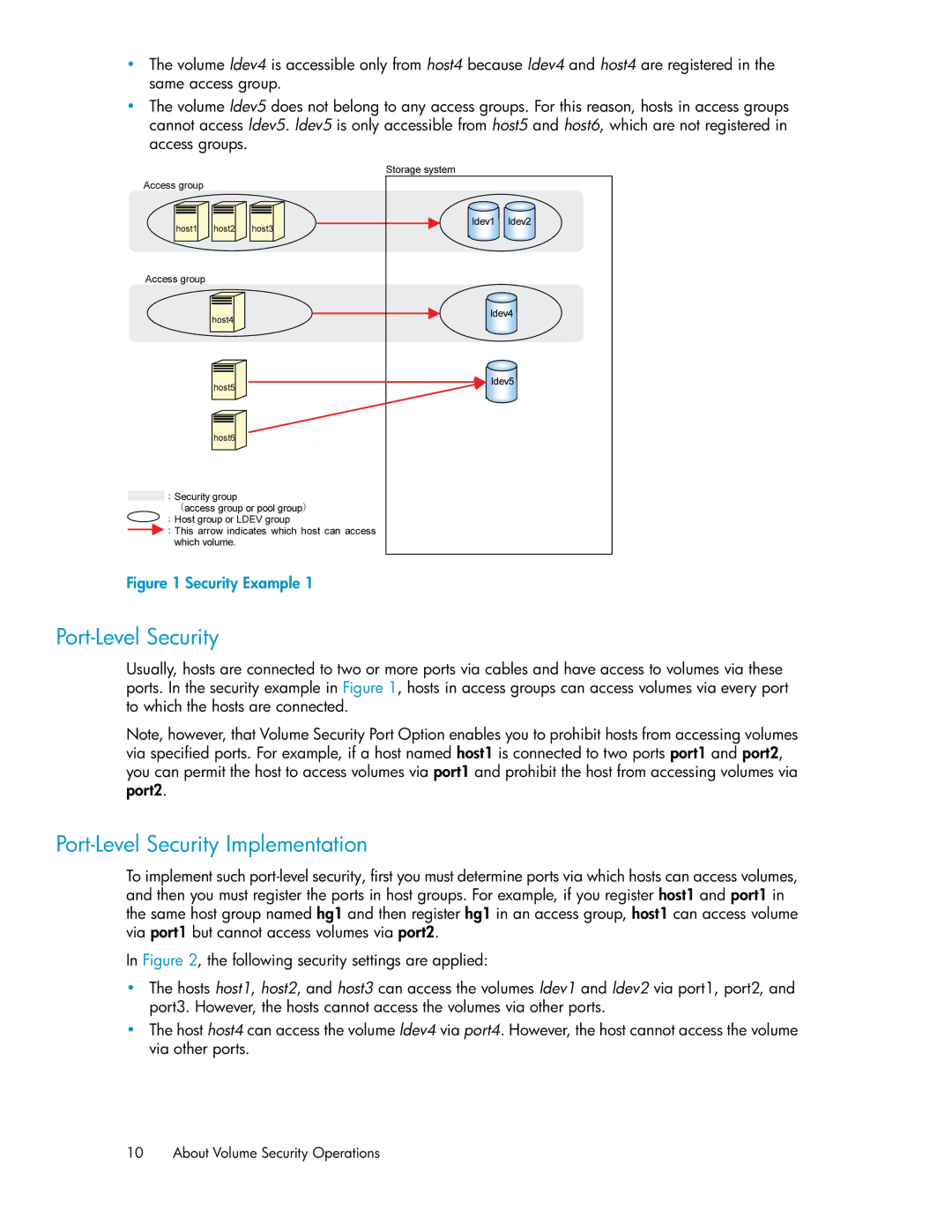
•The volume ldev4 is accessible only from host4 because ldev4 and host4 are registered in the same access group.
•The volume ldev5 does not belong to any access groups. For this reason, hosts in access groups cannot access ldev5. ldev5 is only accessible from host5 and host6, which are not registered in access groups.
Figure 1 Security Example 1
Port-Level Security
Usually, hosts are connected to two or more ports via cables and have access to volumes via these ports. In the security example in Figure 1, hosts in access groups can access volumes via every port to which the hosts are connected.
Note, however, that Volume Security Port Option enables you to prohibit hosts from accessing volumes via specified ports. For example, if a host named host1 is connected to two ports port1 and port2, you can permit the host to access volumes via port1 and prohibit the host from accessing volumes via port2.
Port-Level Security Implementation
To implement such
In Figure 2, the following security settings are applied:
•The hosts host1, host2, and host3 can access the volumes ldev1 and ldev2 via port1, port2, and port3. However, the hosts cannot access the volumes via other ports.
•The host host4 can access the volume ldev4 via port4. However, the host cannot access the volume via other ports.
10 About Volume Security Operations