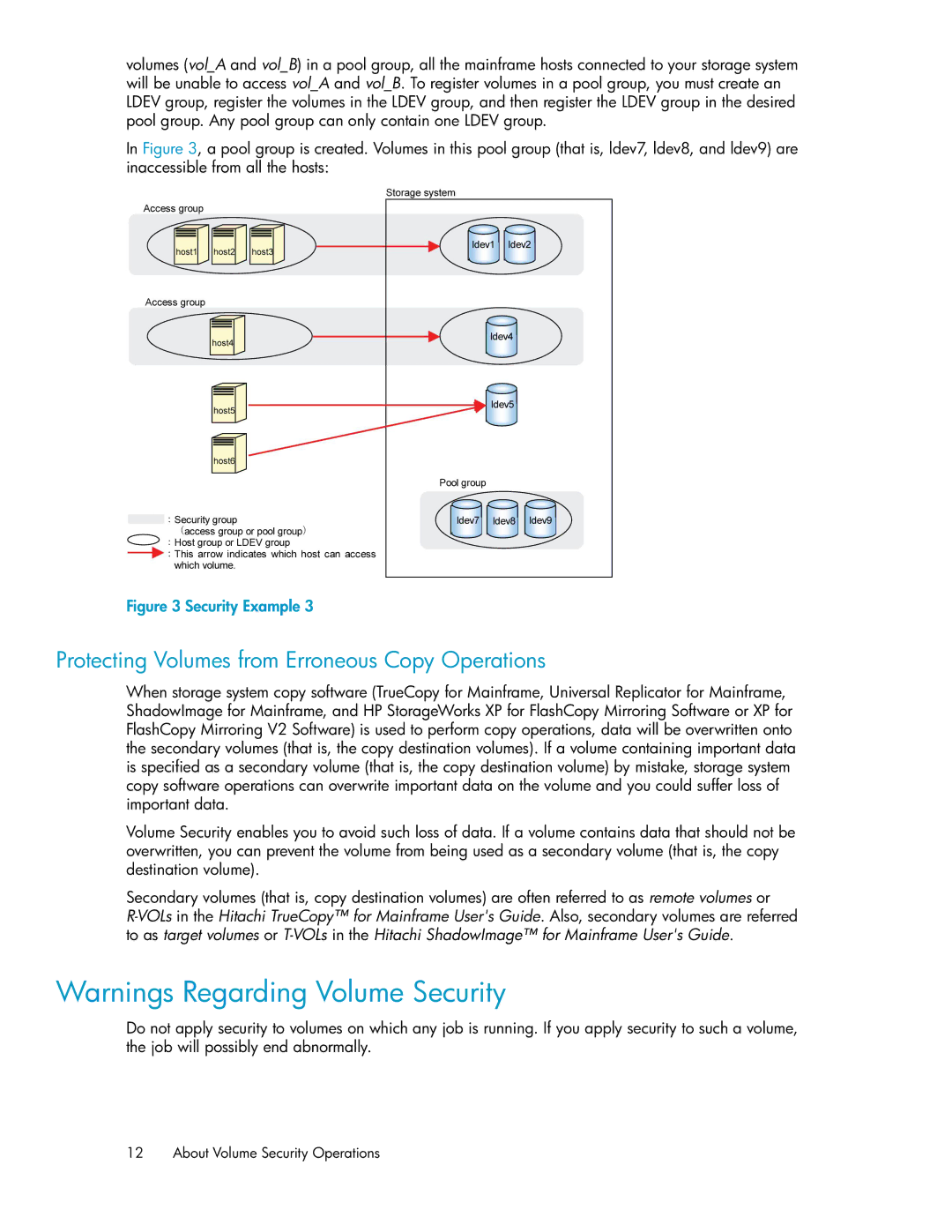
volumes (vol_A and vol_B) in a pool group, all the mainframe hosts connected to your storage system will be unable to access vol_A and vol_B. To register volumes in a pool group, you must create an LDEV group, register the volumes in the LDEV group, and then register the LDEV group in the desired pool group. Any pool group can only contain one LDEV group.
In Figure 3, a pool group is created. Volumes in this pool group (that is, ldev7, ldev8, and ldev9) are inaccessible from all the hosts:
Figure 3 Security Example 3
Protecting Volumes from Erroneous Copy Operations
When storage system copy software (TrueCopy for Mainframe, Universal Replicator for Mainframe, ShadowImage for Mainframe, and HP StorageWorks XP for FlashCopy Mirroring Software or XP for FlashCopy Mirroring V2 Software) is used to perform copy operations, data will be overwritten onto the secondary volumes (that is, the copy destination volumes). If a volume containing important data is specified as a secondary volume (that is, the copy destination volume) by mistake, storage system copy software operations can overwrite important data on the volume and you could suffer loss of important data.
Volume Security enables you to avoid such loss of data. If a volume contains data that should not be overwritten, you can prevent the volume from being used as a secondary volume (that is, the copy destination volume).
Secondary volumes (that is, copy destination volumes) are often referred to as remote volumes or
Warnings Regarding Volume Security
Do not apply security to volumes on which any job is running. If you apply security to such a volume, the job will possibly end abnormally.
12 About Volume Security Operations