201-10301-02, May
FCC Caution
Trademarks
Statement of Conditions
EN 55 022 Declaration of Conformance
Voluntary Control Council for Interference Vcci Statement
Bestätigung des Herstellers/Importeurs
Certificate of the Manufacturer/Importer
201-10301-02, May
Contents
Chapter Wireless Configuration
Chapter Firewall Protection Content Filtering
Chapter Virtual Private Networking
Chapter Advanced Configuration
Appendix C Preparing Your Network
Appendix D Firewall Log Formats
Appendix F Virtual Private Networking
Glossary
Xiv Contents
Typographical Conventions
Chapter About This Manual
Audience, Scope, Conventions, and Formats
Manual Scope
How to Use This Manual
Printing a Chapter
How to Print this Manual
Printing a Page in the Html View
Printing the Full Manual
About This Manual
Key Features of the FWG114P
Chapter Introduction
Full Routing on Both the Broadband and Serial Ports
802.11g and 802.11b Wireless Networking
Flash memory for firmware upgrade NAT off classical routing
Virtual Private Networking
Wireless Multimedia WMM Support
Powerful, True Firewall with Content Filtering
Security
Autosensing Ethernet Connections with Auto Uplink
Extensive Protocol Support
Easy Installation and Management
Netgear Related Products
Package Contents
FWG114P v2 Rear Panel
LED Descriptions
Router to a broadband modem
Introduction
What You Will Need Before You Begin
Connecting the FWG114P v2 to the Internet
Computer Network Configuration Requirements
Cabling and Computer Hardware Requirements
Internet Configuration Requirements
Where Do I Get the Internet Configuration Parameters?
Record Your Internet Connection Information
Connecting the FWG114P v2 Wireless Firewall/Print Server
Verify That Basic Requirements Are Met
Local Port
It starts automatically
Verify the connections to the firewall
LOG in to the Wireless FIREWALL/PRINT Server
Login Result
RUN the Setup Wizard to Connect to the Internet
Make sure the network settings of the computer are correct
Basic Setup Troubleshooting Tips
FWG114P v2 Setup Wizard Auto Detection
Be sure to restart your network in the correct sequence
Wizard-Detected Login Account Setup
Setup Wizard menu for PPPoE login accounts
Connecting the FWG114P v2 to the Internet
Wizard-Detected Dynamic IP Account Setup
10 Setup Wizard menu for Dynamic IP address
Wizard-Detected Fixed IP Account Setup
11 Setup Wizard menu for Fixed IP address
Configure the Serial Port of the Firewall
Connect the Firewall to your Isdn or dial-up modem
12 Serial Internet Connection configuration menu
Testing Your Internet Connection
Connect to the Internet to test your configuration
Manually Configuring Your Internet Connection
13 Browser-based configuration Basic Settings menu
How to Manually Configure the Primary Internet Connection
Connecting the FWG114P v2 to the Internet
Chapter Wireless Configuration
Observing Performance, Placement, and Range Guidelines
Implementing Appropriate Wireless Security
FWG114P v2 wireless data security options
Understanding Wireless Settings
Wireless Settings menu
Wireless Card Access List
Wireless Network. The station name of the FWG114P
Wireless Access Point
Security Options
Default Factory Settings
Feature Default Factory Settings Ssid Netgear
WPA or WPA2 Radius Settings
Before You Change the Ssid and WEP Settings
Authentication
WEP Encryption Keys
How to Set Up and Test Basic Wireless Connectivity
How to Restrict Wireless Access by MAC Address
Wireless Station Access menu
How to Configure WEP
To configure WEP data encryption, follow these steps
Click Wireless Settings in the main menu of the FWG114P
Wireless Settings menu WEP
How to Configure WPA with Radius
Wireless Settings menu WPA with Radius
How to Configure WPA2 with Radius
Wireless Settings menu WPA2 with Radius
How to Configure WPA and WPA2 with Radius
Wireless Settings menu WPA and WPA2 with Radius
How to Configure WPA-PSK
Wireless Settings menu WPA-PSK
How to Configure WPA2-PSK
10 Wireless Settings menu WPA2-PSK
How to Configure WPA-PSK and WPA2-PSK
11 Wireless Settings menu WPA-PSK and WPA2-PSK
Auto-Rollover
Chapter Serial Port Configuration
Modem
Dial-in
How to Configure a Serial Port Modem
Configuring a Serial Port Modem
Basic Requirements for Serial Port Modem Configuration
Basic Requirements for Auto-Rollover
Configuring Auto-Rollover
How to Configure Auto-Rollover
Configuring Dial-in on the Serial Port
Auto-Rollover configuration menu
How to Configure Dial-in
Basic Requirements for Dial-in
Basic Requirements for LAN-to-LAN Connections
Configuring LAN-to-LAN Settings
How to Configure LAN-to-LAN Connections
LAN-to-LAN configuration menu
Serial Port Configuration
Using the Block Sites Menu to Screen Content
Chapter Firewall Protection Content Filtering
Firewall Protection and Content Filtering Overview
Block Sites menu
These steps are discussed below
Services and Rules Regulate Inbound and Outbound Traffic
Defining a Service
Using Inbound/Outbound Rules to Block or Allow Services
Rules menu
Examples of Using Services and Rules to Regulate Traffic
Inbound Rules Port Forwarding
Example Port Forwarding to a Local Public Web Server
This rule is shown in Figure
Rule example Videoconference from Restricted Addresses
Outbound Rules Service Blocking or Port Filtering
Service example port forwarding for VPN when NAT is Off
Other Rules Considerations
Rule example Blocking Instant Messenger
Order of Precedence for Rules
Rules Menu Options
Using a Schedule to Block or Allow Content or Traffic
Schedule menu
Setting the Time Zone
Getting E-Mail Notifications of Event Logs and Alerts
E-mail menu
Firewall Protection and Content Filtering
Viewing Logs of Web Access or Attempted Web Access
10 Logs menu
Log action buttons
What to Include in the Event Log
Log action buttons are described in Table
Firewall Protection and Content Filtering
FWG114P v2 supports these methods for printing
Chapter Print Server
Printing Options
For Macintosh computers LPR printing
Port
For Windows XP and 2000, Use TCP/IP LPR Printing
Click Add a printer. Click Next to proceed
Complete the Add Standard TCP/IP Printer Port Wizard
Add Printer Wizard Install Printer Software
Print Server
For Windows 95/98/Me, Use the Netgear Printer Port Driver
Set up the Netgear printer port driver
Print Server
Printing from the Macintosh
Windows Printer Port Management
Print Port Configuration menu
Troubleshooting the Print Server
Windows Add Printer Wizard
Windows Printer Properties
Print Server
Print Server
Overview of FWG114P v2 Policy-Based VPN Configuration
Chapter Virtual Private Networking
Using Policies to Manage VPN Traffic
Using Automatic Key Management
IKE Policies’ Automatic Key and Authentication Management
IKE Policy Configuration Menu
IKE Policy Configuration Fields
Field Description General
Field Description Remote
VPN Policy Configuration for Auto Key Negotiation
VPN Auto Policy Menu
VPN Auto Policy Configuration Fields
VPN Auto Policy fields are defined in the following table
Authenticating Header AH
VPN Policy Configuration for Manual Key Exchange
Netbios Enable
VPN Manual Policy Menu
VPN Manual Policy Configuration Fields
VPN Manual Policy fields are defined in the following table
Value in its Authentication Algorithm Key In field
Value in its Encryption Algorithm Key Out field
Certificate Revocation List CRL
Walk-Through of Configuration Scenarios on the FWG114P
How to Use the VPN Wizard to Configure a VPN Tunnel
VPN Wizard Start Screen
Summary screen below displays
Remote IP
VPN Wizard Summary
Vpnc Scenario 1 Gateway to Gateway with Preshared Secrets
10 VPN Consortium Scenario
11 LAN to LAN VPN access from an FWG114P v2 to an FWG114P
Scenario 1 FWG114P v2 to FWG114P v2 with Preshared Secrets
13 LAN IP configuration menu
Set up the IKE Policy illustrated below on the FWG114P
14 Scenario 1 IKE Policy
Set up the FWG114P v2 VPN -Auto Policy illustrated below
Address
How to Check VPN Connections
Vpnc Scenario 2 Gateway-to-Gateway with Certificates
16 VPN Consortium Scenario
Obtain a root certificate
Install the trusted CA certificate for the Trusted Root CA
Scenario 2 FWG114P v2 to FWG114P v2 with Certificates
Create a certificate request for the FWG114P
FWG114P
Highlight, copy and paste this data into a text file
19 Self Certificate Requests table
20 Self Certificates table
Set up Certificate Revocation List CRL checking
Summary
Configuration Profile
Netgear VPN Client to FWG114P
Step-By-Step Configuration of FWG114P v2 Gateway
22 Addressing and Subnet Used for Examples
23 Netgear FWG114P v2 IKE Policy Configuration
Virtual Private Networking
24 VPN Auto Policy settings
Virtual Private Networking
Step-By-Step Configuration of the Netgear VPN Client
Install the Netgear VPN Client Software on the PC
Configure the Connection Network Settings
Configure the Connection Identity Settings
27 My Identity
This example, enter this pre-shared key in this field
Select the Enable Perfect Forward Secrecy PFS check box
Click Pre-Shared Key
Hr5xb84l6aa9r6
Configure the Connection Security Policy
31 Connection Security Policy Authentication Phase
32 Connection Security Policy Key Exchange Phase
Check the Encapsulation Protocol ESP check box
Configure the Global Policy Settings
Save the VPN Client Settings
Choose FWG114P
Testing the VPN Connection
From the Client PC to the FWG114P
Monitoring the PC VPN Connection
From the FWG114P v2 to the Client PC
Viewing the FWG114P v2 VPN Status and Log Information
35 Connection Monitor screen
36 FWG114P v2 VPN Status screen
Chapter Maintenance
Viewing Wireless Firewall/Print Server Status Information
Router Status screen shows the following parameters
Status Fields
Dhcp
Connection Status Fields
Click WAN Status to display the WAN connection status
This screen shows the following statistics
Router Statistics Fields
Click Show Statistics to display router usage statistics
Connection Status action buttons
Viewing a List of Attached Devices
WAN Status action buttons are described in Table
Configuration File Management
Upgrading the Router Software
Restoring and Backing Up the Configuration
Settings Backup menu
Changing the Administrator Password
Erasing the Configuration
Maintenance
Connect Automatically, as Required
Chapter Advanced Configuration
Using the WAN Setup Options
Setting Up a Default DMZ Server
Respond to Ping on Internet WAN Port
Setting the WAN Port Speed
How to Configure Dynamic DNS
Setting the MTU Size
10-4 Advanced Configuration
Using the LAN IP Setup Options
Configuring LAN TCP/IP Setup Parameters
10-6 Advanced Configuration
Using the Router as a Dhcp server
Using Address Reservation
Configuring Static Routes
Static Route Entry and Edit Menu
Enabling Remote Management Access
Using Universal Plug and Play UPnP
UPnP Menu
Advanced Wireless Settings
Advanced Wireless Settings menu
Fragmentation Length
WMM support
RTS Threshold
Beacon Interval
10-14 Advanced Configuration
Basic Functioning
Chapter Troubleshooting
Power LED Not On
LEDs Never Turn Off
LAN or Internet Port LEDs Not On
Troubleshooting the Web Configuration Interface
Troubleshooting the ISP Connection
Click on OK You should see a message like this one
Troubleshooting a TCP/IP Network Using a Ping Utility
Testing the LAN Path to Your Router
If the path is working, you see this message
Testing the Path from Your Computer to a Remote Device
If the path is not working, you see this message
Restoring the Default Configuration and Password
Problems with Date and Time
11-8 Troubleshooting
Protocols PPP over Ethernet PPPoE
Appendix a Technical Specifications
Data and Routing
Protocols
10BASE-T or 100BASE-Tx, RJ-45
Wireless
Interface Specifications
Antenna External detachable 5 dBi omnidirectional
Related Publications Basic Router Concepts
What is a Router?
Appendix B Networks, Routing, and Firewall Basics
Is normally written as
Routing Information Protocol
IP Addresses and the Internet
Three Main Address Classes
Combined with
Netmask
Subnet Addressing
Equals
Example of Subnetting a Class B Address
Netmask Notation Translation Table for One Octet
Netmask Formats
Single IP Address Operation Using NAT
Private IP Addresses
Single IP Address Operation Using NAT
Domain Name Server
MAC Addresses and Address Resolution Protocol
Related Documents
IP Configuration by Dhcp
Internet Security and Firewalls
Ethernet Cabling
What is a Firewall?
Denial of Service Attack
Stateful Packet Inspection
Table B-1 UTP Ethernet cable wiring, straight-through
Category 5 Cable Quality
Inside Twisted Pair Cables
Figure B-1illustrates straight-through twisted pair cable
Uplink Switches, Crossover Cables, and MDI/MDIX Switching
Networks, Routing, and Firewall Basics
Networks, Routing, and Firewall Basics
Appendix C Preparing Your Network
Preparing Your Computers for TCP/IP Networking
Configuring Windows 95, 98, and Me for TCP/IP Networking
Install or Verify Windows Networking Components
Preparing Your Network
Enabling Dhcp to Automatically Configure TCP/IP Settings
Selecting Windows’ Internet Access Method
Verifying TCP/IP Properties
Configuring Windows NT, 2000 or XP for IP Networking
Installing or Verifying Windows Networking Components
From the Apple menu, select Control Panels, then TCP/IP
Configuring the Macintosh for TCP/IP Networking
MacOS 8.6 or
MacOS
Verifying TCP/IP Properties for Macintosh Computers
Verifying the Readiness of Your Internet Account
Are Login Protocols Used?
What Is Your Configuration Information?
Mail.xxx.yyy.com
Preparing Your Network
Restarting the Network
Field List
Appendix D Firewall Log Formats
Action List
Outbound Log
Format is
Inbound Log
Other IP Traffic
Router Operation
Operations that the router initiates are logged Format is
Common attacks and scans are logged
Other Connections and Traffic to this Router
DoS Attack/Scan
Datetimepkttype Srcip Dstipaction
All Web Sites and News Groups Visited
Access Block Site
System Admin Sessions
Policy Administration LOG
Date Time Event Direction Service Description
Firewall Log Formats
Infrastructure Mode
Appendix E Wireless Networking Basics
Wireless Networking Overview
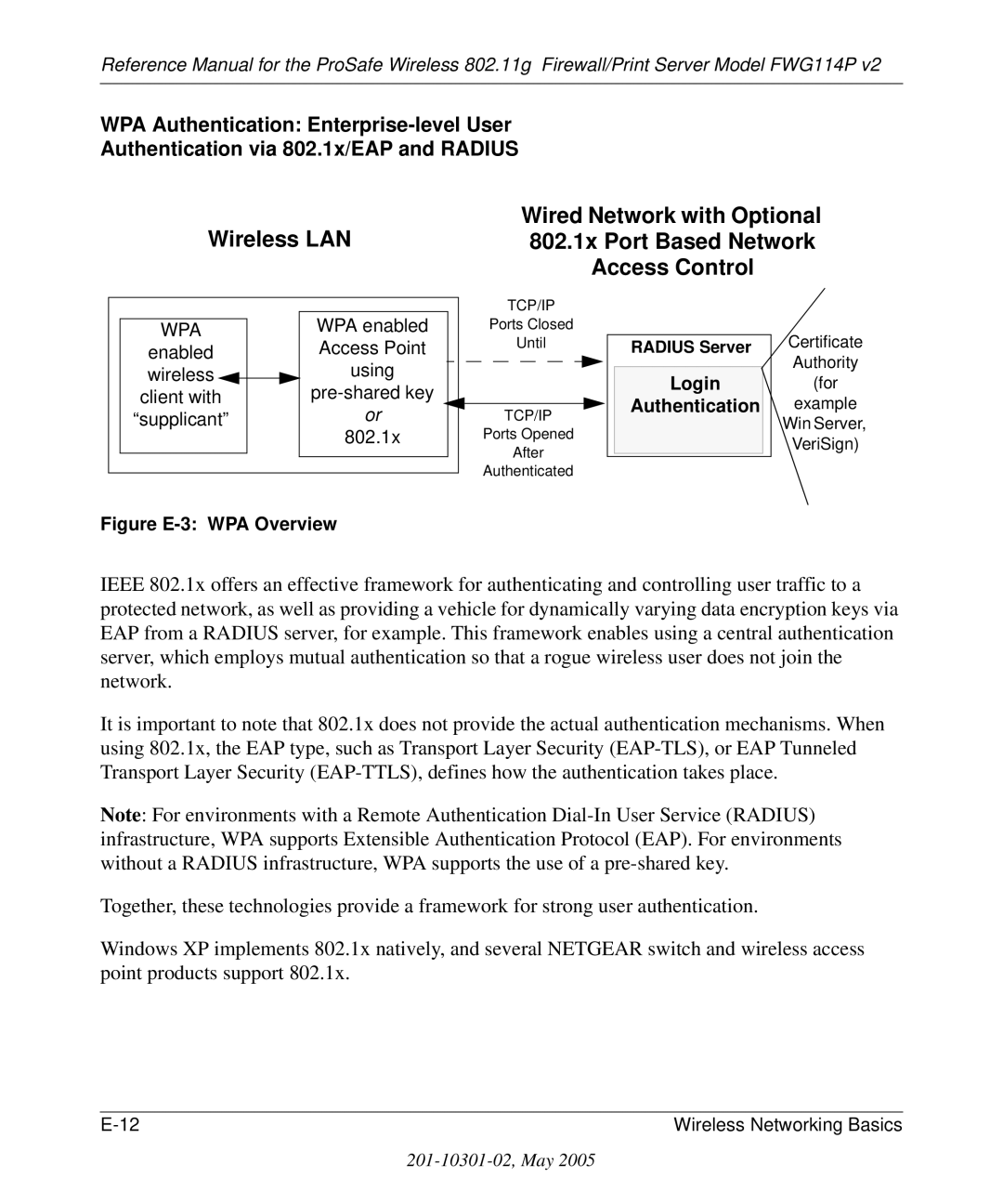
This chapter provides an overview of Wireless networking
Network Name Extended Service Set Identification Essid
Authentication and WEP Data Encryption
Ad Hoc Mode Peer-to-Peer Workgroup
Authentication
Open System Authentication
Shared Key Authentication
Figure E-1 Open system authentication
Figure E-2 Shared key authentication
Overview of WEP Parameters
Key Size
Wireless Channels
WEP Configuration Options
WPA Wireless Security
How Does WPA Compare to WEP?
What are the Key Features of WPA Security?
How Does WPA Compare to Ieee 802.11i?
Wireless Networking Basics
Login Authentication
Figure E-3 WPA Overview
Access point replies with an EAP-request identity message
Figure E-4 802.1x Authentication Sequence
WPA Data Encryption Key Management
Temporal Key Integrity Protocol Tkip
Is WPA Perfect?
Product Support for WPA
Open system, then 802.1x EAP with Radius or preshared key
WPA two-phase authentication
New WPA information element
Michael
Changes to Wireless Client Programs
What is a VPN?
Appendix F Virtual Private Networking
IPSec Components
What is IPSec and How Does It Work?
IPSec Security Features
IPSec contains the following elements
Encapsulating Security Payload ESP
Authentication Header AH
IKE Security Association
Mode
Understand the Process Before You Begin
Key Management
Vpnc Example Network Interface Addressing
VPN Process Overview
Interfaces and Addresses
Subnet Addressing
Setting Up a VPN Tunnel Between Gateways
WAN Internet/Public and LAN Internal/Private Addressing
IPSec Security Association IKE VPN Tunnel Negotiation Steps
Vpnc IKE Phase I Parameters
Vpnc IKE Security Parameters
Additional Reading
Testing and Troubleshooting
Vpnc IKE Phase II Parameters
Virtual Private Networking
Configuration Template
Table G-1 Summary
Figure G-2 Netgear FVS318 VPN Settings Pre-Configuration
Log in to
Figure G-3 Netgear FVS318 VPN Settings part 1 Main Mode
Figure G-4 Netgear FVS318 VPN Settings part 2 Main Mode
Step-By-Step Configuration of FWG114P Gateway B
Figure G-5 Netgear FVS328 IKE Policy Configuration Part
Figure G-6 Netgear FVS328 IKE Policy Configuration Part
Figure G-8 Netgear FVS328 VPN Auto Policy part
Figure G-9 Netgear FWG114P v2 VPN Auto Policy part
Test the VPN Connection
Netgear VPN Configuration FVS318 or FVM318 to FWG114P
Table H-1 Summary
Table H-1
Step-By-Step Configuration of FVS318 or FVM318 Gateway a
Figure H-2 Dynamic DNS Setup menu
Figure H-3 Netgear FVS318 VPN Settings Pre-Configuration
Figure H-4 Netgear FVS318 VPN Settings part 1 Main Mode
Figure H-5 Netgear FVS318 VPN Settings part 2 Main Mode
Step-By-Step Configuration of FVS328 Gateway B
Figure H-6 Netgear FVS328 IKE Policy Configuration Part
Figure H-7 Netgear FVS328 IKE Policy Configuration Part
Figure H-9 Netgear FVS328 VPN Auto Policy part
Figure H-10 Netgear FVS328 VPN Auto Policy part
Test the VPN Connection
201-10301-02, May
Glossary
802.11e Standard
Bandwidth
Collision avoidance
DNS Domain Name System Encryption Key
Gateway
IP Internet Protocol address
PHY
Plug and Play
Satellite broadband
TCP/IP
War Driving
Wi-Fi Protected Access and Ieee 802.11i Comparison
Wi-Fi Protected Access in Mixed Mode Deployment