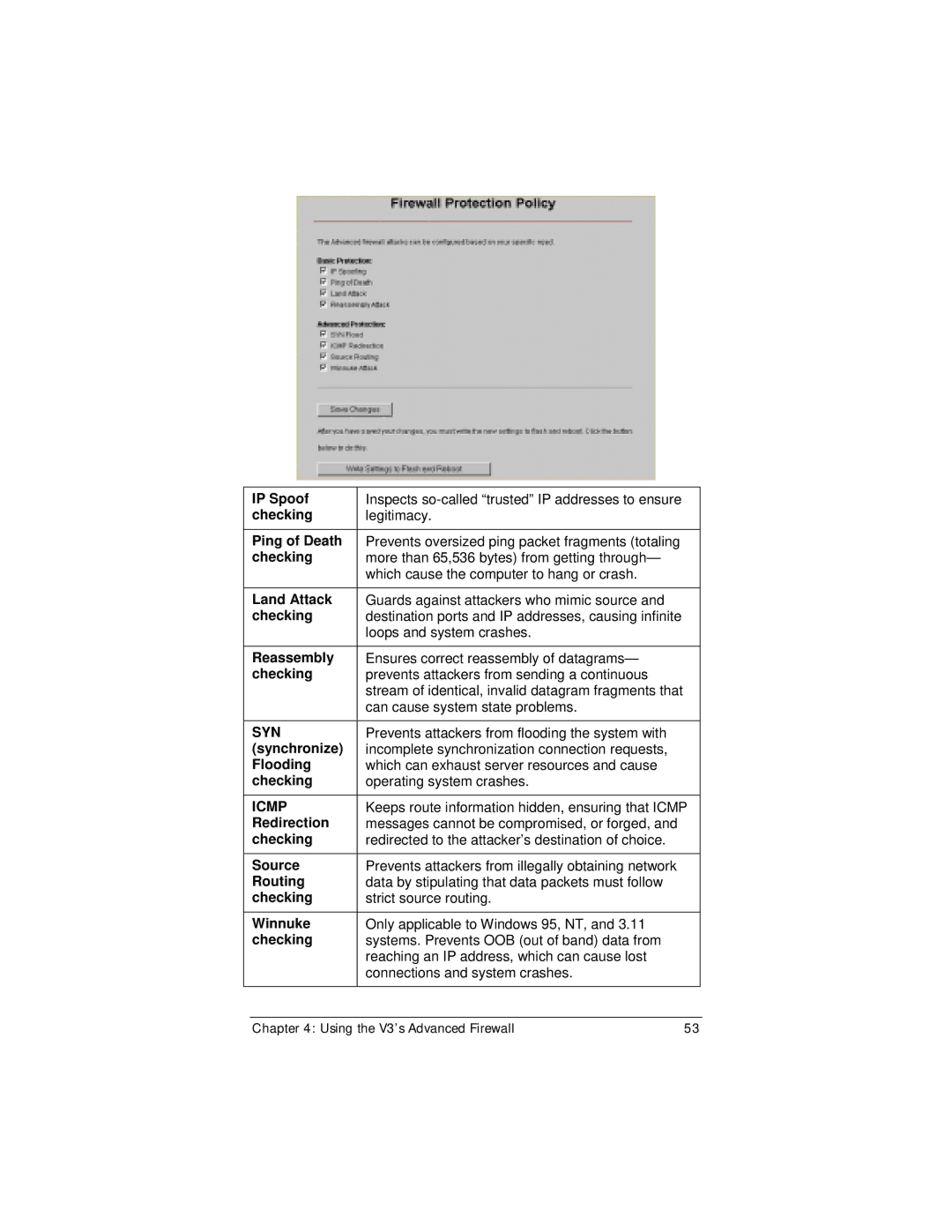
IP Spoof | Inspects |
checking | legitimacy. |
|
|
Ping of Death | Prevents oversized ping packet fragments (totaling |
checking | more than 65,536 bytes) from getting through— |
| which cause the computer to hang or crash. |
|
|
Land Attack | Guards against attackers who mimic source and |
checking | destination ports and IP addresses, causing infinite |
| loops and system crashes. |
|
|
Reassembly | Ensures correct reassembly of datagrams— |
checking | prevents attackers from sending a continuous |
| stream of identical, invalid datagram fragments that |
| can cause system state problems. |
|
|
SYN | Prevents attackers from flooding the system with |
(synchronize) | incomplete synchronization connection requests, |
Flooding | which can exhaust server resources and cause |
checking | operating system crashes. |
|
|
ICMP | Keeps route information hidden, ensuring that ICMP |
Redirection | messages cannot be compromised, or forged, and |
checking | redirected to the attacker’s destination of choice. |
|
|
Source | Prevents attackers from illegally obtaining network |
Routing | data by stipulating that data packets must follow |
checking | strict source routing. |
|
|
Winnuke | Only applicable to Windows 95, NT, and 3.11 |
checking | systems. Prevents OOB (out of band) data from |
| reaching an IP address, which can cause lost |
| connections and system crashes. |
|
|
Chapter 4: Using the V3’s Advanced Firewall | 53 |