Value-Line and Advanced Console Servers User’s Manual
Value-Line and Advanced Console Servers Manual
Blackbox.com
Value-Line and Advanced Console Servers Manual
Value-Line and Advanced Console Servers Manual
Management network configuration
Power connection
Administrator Password
System Services
Serial Port Redirection Managed Devices IPsec VPN
FIREWALL, Failover and OoB DIAL-IN OoB Dial-In Access
Configuring for SSH Tunneling to Hosts
SDT Connector Client Configuration
SSH Tunneling using other SSH clients e.g. PuTTY
SDT Connector to Management Console
SDT Connector Public Key Authentication
Setting up SDT for Remote Desktop access
PAM Pluggable Authentication Modules
Remote Power Control RPC
Uninterruptible Power Supply Control UPS
Authentication Configuration
213
13.4 Power Management 212
203
209
Power Strip Control
Raw Access to Serial Ports
Modifying Snmp Configuration
Secure Shell SSH Public Key Authentication
Appendix
Server
Chapter Introduction
This Manual
Manual Organization
Management Console
Types of users
Console server
Publishing history
Manual Conventions
Date Revision Update details
Copyright
Introduction
Chapter Installation
Models
Kit components LES1508A Console Server
Blackbox.com
1 LES1508A power
Power connection
Kit components LES1108A Console Server
2 LES1116A, LES1132A and LES1148A power
Network connection
4 LES1108A power
Serial Port connection
USB Port Connection
PIN Signal Definition Direction
Antenna and SIM
Before powering on the console server
Management console connection
Chapter Initial System Configuration
IP address
Browser connection
Blackbox.com
Administrator Password
Network IP address
Set up new administrator
Name the console server
Configuration Method
Dynamic DNS Ddns configuration
1 IPv6 configuration
Service Access
System Services
Blackbox.com
Select the Service Settings tab on the System Services
Message Changes to configuration succeeded Service Settings
Communications Software
PuTTY
SDT Connector
SSHTerm
Management network configuration
Enable the Management LAN
Check Enable Dhcp Server
Configure the Dhcp server
Select Failover or broadband OOB
Blackbox.com
Aggregating the network ports
Static routes
To add to the static route to the route table of the system
Configure Serial Ports
Serial Port, Host, Device & User Configuration
Common Settings
Console Server Mode
Blackbox.com
Blackbox.com
Blackbox.com
Blackbox.com
SDT Mode
Terminal Server Mode
Device RPC, UPS, EMD Mode
Serial Bridging Mode
Cisco USB console connection
Add/ Edit Users
Ftp
Admin
Pptpd
Dialin
Blackbox.com
Blackbox.com
Network Hosts
Authentication
Select Serial & Network Trusted Networks
Trusted Networks
Automatically generate and upload SSH keys
Serial Port Cascading
Select RSA Keys and/or DSA Keys
Check Generate SSH keys automatically and click Apply
Manually generate and upload SSH keys
# ssh remhost
Configure the slaves and their serial ports
Managing the Slaves
Serial Port Redirection
Select Serial & Network Managed Devices
Managed Devices
Add Connection
IPsec VPN
Select IPsec VPN on the Serial & Networks menu
Enable the VPN gateway
Select OpenVPN on the Serial & Networks menu
Enable the OpenVPN
Configure as Server or Client
Windows OpenVPN Client and Server set up
Windows client/server configuration file options are
AES
Blackbox.com
Pptp VPN
None
Set up a remote Pptp client
Click Apply Settings Add a Pptp user
Blackbox.com
OoB Dial-In Access
Chapter Firewall, Failover and OoB Dial Access
Check Enable Dial-In
Configure Dial-In PPP
MSCHAPv2
Set up Windows XP/ 2003/Vista/7 client
Using SDT Connector client
Set up earlier Windows clients
OoB broadband access
Set up Linux clients for dial-in
Broadband Ethernet Failover
Always-on dial-out
Dial-Out Failover
Blackbox.com
Connect to the GSM HSUPA/UMTS carrier network
Failover dial-out
Blackbox.com
Otasp Activation
Connect to the Cdma EV-DO carrier network
Manual Activation
Cellular modem watchdog
Verify cellular connection
Cellular failover setup
OOB access set up
Check Enable Dial-In and configure the Dial-In Settings
Cellular CSD dial-in setup
Cellular routing
Firewall & Forwarding
Configuring network forwarding and IP masquerading
Manual Configuration
Configuring client devices
Dhcp Configuration
Click Add New Port Forward
Port forwarding
Firewall rules
Dialout/Cellular, VPN, Network Interface, Dial-in etc
Click New Firewall Rule
Interface Dialout/Cellular Port Range
Destination IP
Interface
Port Range
Source IP
Chapter Secure SSH Tunneling & SDT Connector
SDT Connector Client Configuration
Configuring for SSH Tunneling to Hosts
Run the set-up program
SDT Connector installation
Blackbox.com
Blackbox.com
Make an SDT connection through the gateway to a host
Manually adding hosts to the SDT Connector gateway
Manually adding new services to the new hosts
Blackbox.com
Adding a client program to be started for the new service
Blackbox.com
Dial in configuration
SDT Connector to Management Console
Blackbox.com
Click Add, then scroll to the bottom and click Apply
Blackbox.com
Pon networkconnection
Importing and exporting preferences
OpenSSH Windows http//sshwindows.sourceforge.net/download
SDT Connector Public Key Authentication
Setting up SDT for Remote Desktop access
Configure the Remote Desktop Connection client
Blackbox.com
Option Description
Click Connect
On a Macintosh client
SDT SSH Tunnel for VNC
Install, configure and connect the VNC Viewer
Blackbox.com
Blackbox.com
Blackbox.com
From
Select Allow calling computer to specify its own address
Set up SDT Serial Ports on console server
SSH Tunneling using other SSH clients e.g. PuTTY
Blackbox.com
Blackbox.com
Chapter Alerts, Auto-response Logging
Configure Auto-Response
Blackbox.com
Click on UPS Status as the Check Condition
UPS / Power Supply
Click on UPS / Power Supply as the Check Condition
Check Save Auto-Response UPS Status
Click on Icmp Ping as the Check Condition
Serial Login/Logout
Check Save Auto-Response Cellular Data
Click on SMS Command as the Check Condition
Check Save Auto-Response SMS Command
Click on Custom Check as the Check Condition
Send Email
Action Delay Time
Send SMS
Send Email alerts
Click Save New Action
Select Alerts & Logging Smtp &SMS
SMS via Email Gateway
Send SMS alerts
SMS via Cellular Modem
Select Cellular Modem In the SMS Settings field
Select Alerts & Logging Snmp
Send Snmp trap alerts
Log storage
Logging
Nagios alerts
Network Serial Ports refer to Chapter
Serial port logging
Network TCP and UDP port logging
Power device logging
Auto-Response event logging
Remote Power Control RPC
Chapter Power & Environmental Management
RPC connection
Blackbox.com
Blackbox.com
User power management
RPC access privileges and alerts
Turn on
Turn OFF Cycle Status
Uninterruptible Power Supply Control UPS
RPC status
Managed UPS connections
Blackbox.com
Blackbox.com
Remote UPS management
Controlling UPS powered computers
UPS alerts
Monitor managedups@192.168.0.1 1 username password slave
UPS status
Overview of Network UPS Tools NUT
Blackbox.com
Environmental Monitoring
Connecting the EMD
Blackbox.com
Environmental status
Environmental alerts
Authentication Configuration
Chapter Authentication
Tacacs authentication
Radius authentication
Ldap authentication
Enter the Server Password
Blackbox.com
Group support with remote authentication
RADIUS/TACACS User Configuration
Remote groups with Ldap authentication
Remote groups with Radius authentication
Network
Administration Group DN
Kerberos authentication
Remote groups with TACACS+ authentication
Idle timeout
Select Serial and Network Authentication
Authentication testing
PAM Pluggable Authentication Modules
TACACS+
SSL Certificate
Blackbox.com
Blackbox.com
Chapter Nagios Integration
Nagios Overview
Central management and setting up SDT for Nagios
Distributed console servers Black Box console servers
Set up central Nagios server
Description, for example Windows 2003 IIS Server
Set up distributed console servers
Check Nagios Nsca
In Description enter Administrator connection
Select Serial Port from the Serial & Network menu
Click Console server Mode, and select Logging Level
Select Users & Groups from the Serial & Network menu
Configuring Nagios distributed monitoring
Enable Nagios on the console server
Enabled
Select System Nagios and check Nrpe Enabled
Enable Nrpe monitoring
Enable Nsca monitoring
Permitted Service
Select System Nagios and check Nsca Enabled
Configure Selected Serial Ports for Nagios Monitoring
Configure Selected Network Hosts for Nagios Monitoring
Configure the upstream Nagios monitoring host
Advanced Distributed Monitoring Configuration
Sample Nagios configuration
Hostname Black Box
CheckpingviaBlack Box
Checkportlog
CheckconnviaBlack Box
Executionfailurecriteria SSH Port Define command
Basic Nagios plug-ins
Number of supported devices
Additional plug-ins
Local office
Distributed Monitoring Usage Scenarios
Remote site with restrictive firewall
II. Remote site
Remote site with no network access
Chapter System Management
System Administration and Reset
Configure Date and Time
Upgrade Firmware
Configuration Backup
Blackbox.com
Blackbox.com
Delayed Configuration Commit
Select the System Administration menu option
Fips Mode
Statistics
Port Access and Active Users
Select the Status Port Access
Chapter Status Reports
Select Status Syslog
Support Reports
Syslog
Select the Status Statistics
Dashboard
Configuring the Dashboard
Blackbox.com
Blackbox.com
Echo table
Creating custom widgets for the Dashboard
Device Management
Chapter Management
Port and Host Logs
Web Terminal to Command Line
Web Terminal
Check Web Terminal and click Apply
SDT Connector access
Select Manage Terminal
Select Manage Power
Power Management
Accessing config from the command line
Chapter Command Line Configuration
Description
Syntax
Options
Listed below
At /etc/config/config.xml
Run=configurator
# /bin/config -d element name
Serial Port configuration
Device Mode
Console server mode
Syslog settings
Serial bridge mode
# config -s config.ports.port5.mode=bridge
Config.ports.port5.bridge.ssh.enabled=on
# config -d config.users.user2.port1
# config -g config.users.total
Adding and Removing Users
Adding and removing user Groups
# ./delete-node config.users.user2
# config -r users
# config -g config.groups.total
# config -r auth
# config -a
Add other network host
# config -g config.sdt.hosts.total
# config -s config.sdt.hosts.total=4
Add power device host
Cascaded Ports
# config -g config.devices.total
# config -hosts
# config -g config.portaccess.total
UPS Connections
# config -r cascade
Managed UPSes
RPC Connections
# config -s config.ups.monitors.total=1
Remote UPSes
Environmental
Port Log
# config -d config.devices.device8
User Syslog Mail News
Alerts
Error
General settings for all alerts
Signal Alert
Environmental and Power Sensor Alert
UPS Power Status Alert
Pattern Match Alert
Smtp & SMS
Alarm Sensor Alert
# config -r alerts
# config -s config.system.smtp.server2=mail.Black Box.com
IP settings
Administration
Snmp
Date & Time Settings
# config -s config.console.ppp.defaultroute=on
Dial-in settings
# config -s config.system.timezone=US/Eastern
# config -r time
Services
Blowfish Twofish RIJNDAEL-256 Serpent Gost
Nagios
Custom Scripting
Chapter Advanced Configuration
Using IPMItools
Custom script to run when booting
Running custom scripts when alerts are triggered
# dos2unix /etc/config/rc.local
# cd
Bin/sh /etc/scripts/alert-email $suffix
Example script Power Cycling on Pattern Match
Deleting Configuration Values from the CLI
Example script Multiple email notifications on each alert
Delete-node script
# ./delete-node config.users.user3
While $COUNTER != $TOTAL-NUMBER+1 do
NEWTOTAL=$ $TOTAL
Power Cycle any device when a ping request fails
Ping-detect script
Running custom scripts when a configurator is invoked
# /etc/scripts/backup-usb load filename
# /etc/scripts/backup-usb list
Backing-up the configuration off-box
Pmchat
Portmanager commands
Advanced Portmanager
Pmshell
External Scripts and Alerts
Signals
Pmusers
Portmanager daemon
Access to serial ports
Raw Access to Serial Ports
Etc/config/ipfilter
Accessing the console/modem port
IP- Filtering
15.5.1 /etc/config/snmpd.conf
Modifying Snmp Configuration
Sysdescr Black Box Syscontact
Adding more than one Snmp server
Config --set config.system.snmp.password2=yourpassword
Secure Shell SSH Public Key Authentication
SSH Overview
28aa2938ba40f4115e3fd4fae53614d6 user@server
Installing the SSH Public/Private Keys Clustering
Generating Public Keys Linux
$ ssh-keygen -t rsadsa
Chown fred /etc/config/users/fred/.ssh/authorizedkeys
Installing SSH Public Key Authentication Linux
Blackbox.com
Generating public/private keys for SSH Windows
Blackbox.com
Ab7e33bd85505a430be0bd433f1ca5f8
Fingerprinting
Offending key in /.ssh/knownhosts1
Client Keys
SSH tunneled serial bridging
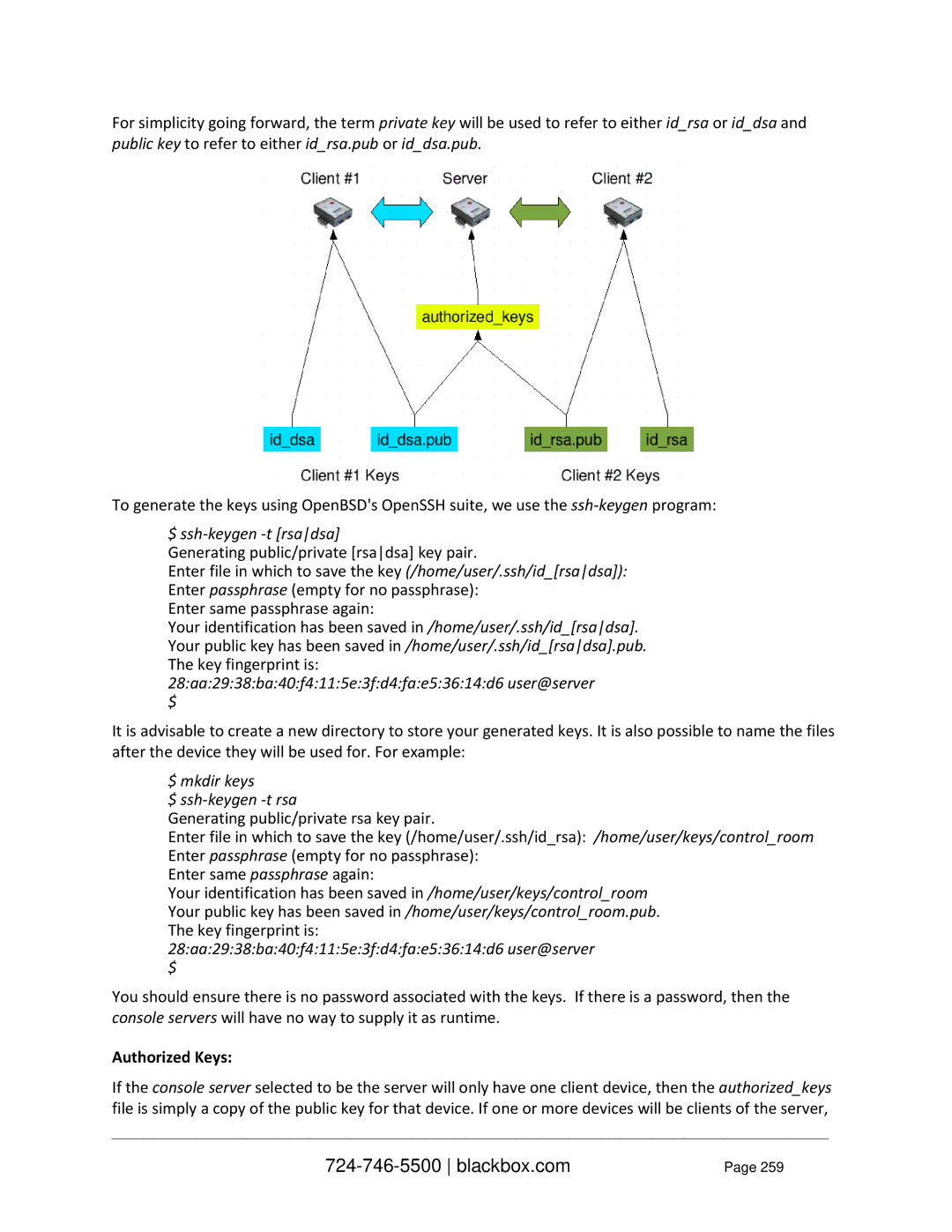
Authorized Keys
Public key to refer to either idrsa.pub or iddsa.pub
Uploading Keys
SDT Connector Public Key Authentication
Secure Sockets Layer SSL Support
$ ls /home/user/keys
Generating a self-signed certificate with OpenSSL
Https
Generating an encryption key
Openssl genrsa -des3 -out sslkey.pem
Kill -HUP `cat /var/run/inetd.pid`
Power Strip Control
Installing the key and certificate
Launching the Https Server
Target Specification
PowerMan tool
Synopsis
Pmpower tool
Powerman --on foo0,4-5
Adding new RPC devices
Blackbox.com
IPMItool
P-f password -o oemtype command
Ipmitool -c-h-v-V-I lan -H hostname -p port
Lprivlvl
Aauthtype
Cciphersuite
Iinterface
Ipmitool help
Help
Ipmitool chassis help
Ipmitool chassis power help
Custom Development Kit CDK
Scripts for Managing Slaves
Select Serial & Network Serial Port, Edit the serial ports
Select Alerts & Logging Port Log
Select Status Support Report
Appendix a Linux Commands & Source Code
Blackbox.com
Blackbox.com
Blackbox.com
Commands
Sigspec -n signum -si let arg arg
Feature Value
Appendix B Hardware Specifications
FCC Warning Statement
Appendix C Safety & Certifications
Appendix F End User License Agreement
Read Before Using the Accompanying Software
JSch License
SDT Connector License
Blackbox.com
No Warranty
Blackbox.com
Blackbox.com
Black Box Tech Support FREE! Live /7