Foundry AR-Series Router User Guide
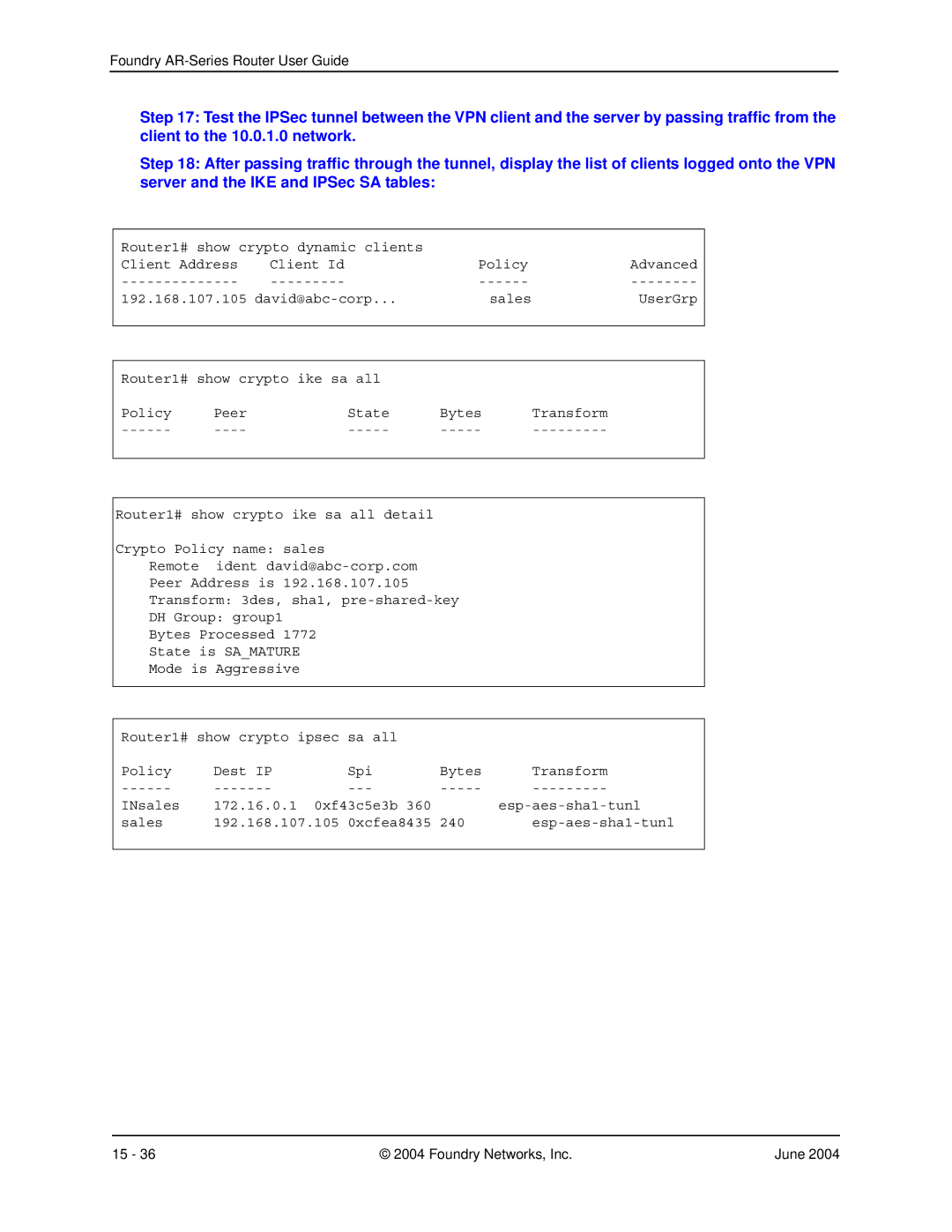
Step 17: Test the IPSec tunnel between the VPN client and the server by passing traffic from the client to the 10.0.1.0 network.
Step 18: After passing traffic through the tunnel, display the list of clients logged onto the VPN server and the IKE and IPSec SA tables:
Router1# show crypto dynamic clients |
|
| |
Client Address | Client Id | Policy | Advanced |
192.168.107.105 | sales | UserGrp | |
|
|
|
|
Router1# show crypto ike sa all |
|
| ||
Policy | Peer | State | Bytes | Transform |
|
|
| ||
|
|
| ||
Router1# show crypto ike sa all detail |
|
| ||
Crypto Policy name: sales |
|
|
| |
Remote | ident |
|
| |
Peer Address is 192.168.107.105 |
|
| ||
Transform: 3des, sha1, |
| |||
DH Group: group1 |
|
|
| |
Bytes Processed 1772 |
|
|
| |
State is SA_MATURE |
|
|
| |
Mode is Aggressive |
|
|
| |
|
|
|
| |
|
|
|
| |
Router1# show crypto ipsec | sa all |
|
| |
Policy | Dest IP | Spi | Bytes | Transform |
INsales | 172.16.0.1 0xf43c5e3b 360 |
| ||
sales | 192.168.107.105 | 0xcfea8435 | 240 | |
|
|
|
|
|
15 - 36 | © 2004 Foundry Networks, Inc. | June 2004 |