Foundry AR-Series Router User Guide
NOTE: Using the redistribute connected command adds a recursive route to the tunnel destination. This will cause the tunnel to shut down. To prevent this, add a 32-bit static route for the tunnel destination.
With the tunnel properly configured and working, users on one side of the tunnel can ping users on the other side.
Firewalls
Configuring firewalls allows administrators to adapt network protection policies to meet ever-changing hacker and intruder threats. Just as virus protection software requires updates to protect against the latest intrusion attacks, firewalls must be updated. In this release of Foundry software, administrators are able to filter traffic on specific ports, protect against Denial of Services attacks, enable IP packet reassembly, and so forth.
Because firewalls provide a barrier between the inside world—the corporate network, and the outside world— primarily the Internet, network administrators can further protect the network inside the firewall by using Network Address Translation (NAT). NAT allows users on the inside of the firewall to use private, nonroutable IP addresses which are translated to routable IP addresses at the firewall. The firewall manages the address translation by converting private IP addresses into a public address for outbound traffic. On inbound traffic the firewall converts traffic addressed to the public IP address into the various private IP addresses of the firewall-protected users. In addition to the protection of not being directly reachable from outside the network, the firewall-NAT enabled network conserves IP addresses.
Firewall Configuration Examples
Basic Firewall Configuration
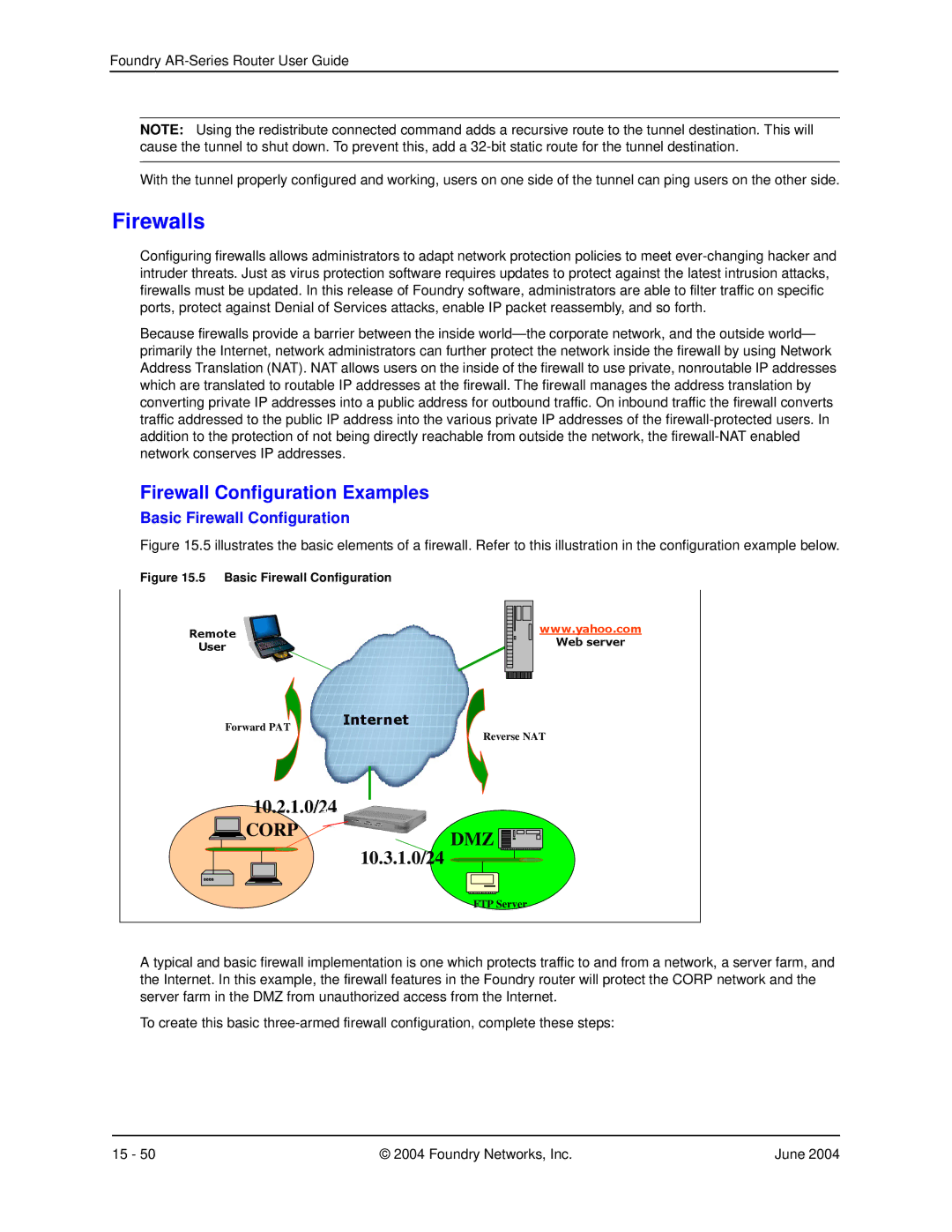
Figure 15.5 illustrates the basic elements of a firewall. Refer to this illustration in the configuration example below.
Figure 15.5 Basic Firewall Configuration
| Remote | www.yahoo.com |
| Web server |
| User |
| |
| Forward PAT | Internet |
| Reverse NAT |
| |
| 10.2.1.0/24 | |
| CORP | DMZ |
| |
| | 10.3.1.0/24 |
| | FTP Server |
A typical and basic firewall implementation is one which protects traffic to and from a network, a server farm, and the Internet. In this example, the firewall features in the Foundry router will protect the CORP network and the server farm in the DMZ from unauthorized access from the Internet.
To create this basic three-armed firewall configuration, complete these steps: