IP88S36-T001-000
Troubleshooting Guide
Copyright c 2009, NEC Corporation, All rights reserved
November, 2009 1st Edition IP88S36-T001-000
Intended users
Introduction
Applicable product
Correction of this manual
IP8800/S6700, IP8800/S6600, IP8800/S6300
Troubleshooting Guide IP88S36-T001
Operation Commands, Vol.1 IP88S63-S006
IP8800/S3600, IP8800/S2400
Introduction
III
BGP4+
Conventions abbreviations
CIR
MIP
Conventions kB, MB, GB, and TB
Page
Contents
IPv4 Network Communication Failure
Layer 2 Authentication Communication Failure
Network Interface Communication Failure
Layer 2 Network Communication Failure
Snmp Communication Failure 110
Problems on Power Saving Feature 123
When Resource Shortage Occurs in Shared Memory 135
Communication Failure on High-reliability Function 103
Restarting the System 160
Transferring Files for Maintenance Information 144
Testing Line 154
Writing to MC 152
Be careful in operation
Safety guide for the IP8800/S6700 series
Symbols
Operations and actions
Do not put foreign matters in the device
Do not use power not specified
Do not place the device in an unstable location
Do not remove the device cover
Do not touch the potential tap
Grounding is required
Do not plug too many leads into a single outlet
Handle the power cable with caution
Keep air dusters away from fire
Before carrying the device, remove the cables
Do not install the device in a humid or dusty environment
Do not stack the devices
Do not block the intake and/or exhaust port
Do not drop an optional component
Do not roughly handle the power cable
Do not touch the inside of the device
An SFP-T has the following label attached
Lithium battery
Cleaning
Be careful of laser beams
Do not attach a label or the like to the transceivers
Handle a memory card with care
Attach an option component with care
Use air dusters with care
Handle the optical connector with care
Maintenance and cleaning
Do not bring a TV or radio close to the device
Page
Safety guide for the IP8800/S6600 series
Safety Guide IP8800/S6600
Safety Guide IP8800/S6600
Model Mass Number of people
Xix
IP8800/S6604 45 kg/100 lb Or more IP8800/S6608 64 kg/142 lb
Label below is attached to the device
Keep air dusters away from fire
IP8800/S6604
Use support brackets only for IP8800/S6604
Use support brackets with care
Model Items
Do not block the intake and/or exhaust port
Do not roughly handle the power cable
Lithium battery
Handle a memory card with care
Attach an option component with care
Do not bring a TV or radio close to the device
Safety guide for the IP8800/S6300 series
Safety Guide IP8800/S6300
Safety Guide IP8800/S6300
Grounding is required
IP8800/S6304 45kg/100 lb Or more IP8800/S6308 64kg/142 lb
Keep air dusters away from fire
IP8800/S6304
Use support brackets only for IP8800/S6304
Do not block the intake and/or exhaust port
Do not roughly handle the power cable
Lithium battery
Handle a memory card with care
Damaged by the static electricity
Do not bring a TV or radio close to the device
Operations and Handling
Safety guide for the IP8800/S3600 and IP8800/S2400 series
Do not put foreign materials in the device
Safety Guide IP8800/S3600 IP8800/S2400
Device in Trouble Action to Be Taken
Do not use power not specified
Do not use too many plugs at a single outlet
Do not use the cable with the protection cap detached
Do not block the intake/exhaust port
Xlvi
Precaution on carrying the device
Be careful of the laser beams
Do not ride, recline, or place a heavy loading on the device
Do not bring a TV or radio close to the device
Handle a memory card and a dummy memory card with care
Before installing or Uninstalling
Discarding the device
Page
Overview
Overview
Failure Analysis Overview
System and Partial Failure Analysis Overview
LED Indications, Switches, and Connectors
Name Type Status Description
Failure Analysis for IP8800/S3600 and IP8800/S2400
Connecting operation terminal
Overview Name Type Status Description
LED Green
Lit in green Power on OFF Power OFF or power failure
Connector Memory card slot
Name Type Function Description
Blocked
Overview Name Type Function Description
Orange 100/1000BASE-T Ethernet port
Sent/received
Functional Failure Status and Reference
Functional Failure Analysis Overview
Subitem Reference
Overview Subitem Reference
Schedule Is Disabled IP8800/S6700
Time Synchronization by NTP Is Disabled
Active System Switchover Is Disabled
Active BSU Switchover Is Disabled
Page
Troubleshooting System Failures
Failure Action
Troubleshooting Procedure on System Failures
Troubleshooting System Failures
Troubleshooting System Failures
Troubleshooting System Failures Action
Power Failure Check Items
Replacement Method of Optional Components
Follow the steps in -4 Isolating Power Supply Failure
Troubleshooting for IP8800/S3600 and IP8800/ S2400
Power failure according to -4 Isolating Power Supply
Isolating Power Supply Failure
Failures on External Power Unit to isolate the failure
Isolating Failures on Power Module
Isolating Failures on External Power Unit
Isolating Failures on External Power Unit
Isolating Failures on External Power Unit Main Body
Replacement Method of System and Optional Components
Troubleshooting Functional Failures in Operation
Troubleshooting Functional Failures in Operation
Forgot the Login User Password
Problems on Login Password
Forgot the System Administrator Password
Instruction in -1 Problems and Actions When MC
Problems on MC
MC not found is displayed when MC is accessed
Problems and Actions When MC not found is displayed
System and Partial Failure Analysis Overview
Problems on Operation Terminal
Problems and Actions When Connecting to Console
Unable to Input/Display from the Console Correctly
Problems and Actions When Connecting to Modem
Login from the Remote Operation Terminal Is Failed
Symptom Action to Be Taken or Reference
Some users remain in the login
Login Authentication Using RADIUS/TACACS+ Is Disabled
Command Authorization Using RADIUS/TACACS+ Is Disabled
Disabled, check No or later
Troubleshooting Functional Failures in Operation
Checking port status
NIF Status Problem Action
Network Interface Communication Failure
Ethernet Port Cannot Be Connected
Checking statistical information
Port Status Problem Action
Check and Action for Port Status
Check and Action for BSU/PSP Operation Status
Communication Failure in Basic Switching Unit BSU/PSP
BSU Operation Problem Action Status
Checking BSU/PSP operation status
Configuration of Basic Switching Unit BSU
Status, see 3.20 Problems on Redundant
Actions against Troubles on 10BASE-T/100BASE-TX/ 1000BASE-T
Troubleshooting Steps Problem Action
Troubleshooting for Failed 10BASE-T/100BASE-TX/1000BASE-T
10 Failure Analysis Method for Troubles on 1000BASE-X
Actions against Troubles on 1000BASE-X
Actions against Troubles on 10GBASE-R
11 Failure Analysis Method for Troubles on 10GBASE-R
Troubleshooting Steps and Command Action
Communication Failure on Using PoE
Allocations
Communication Failure on Using Link Aggregation
Function of the port by the power inline command
Check the setting of failed link aggregation
Tion, set the Duplex mode to Full
Check the setting of failed port status using
CH Disabled
Link aggregation group is Disabled and Down
Layer 2 Network Communication Failure
Layer 2 Communication by Vlan Is Disabled
Checking Vlan status
Take the action below according to the Type displayed
Checking MAC address table
Checking filtering/QoS
Failures on Using Spanning Tree
Flooding is executed if the MAC address is not displayed
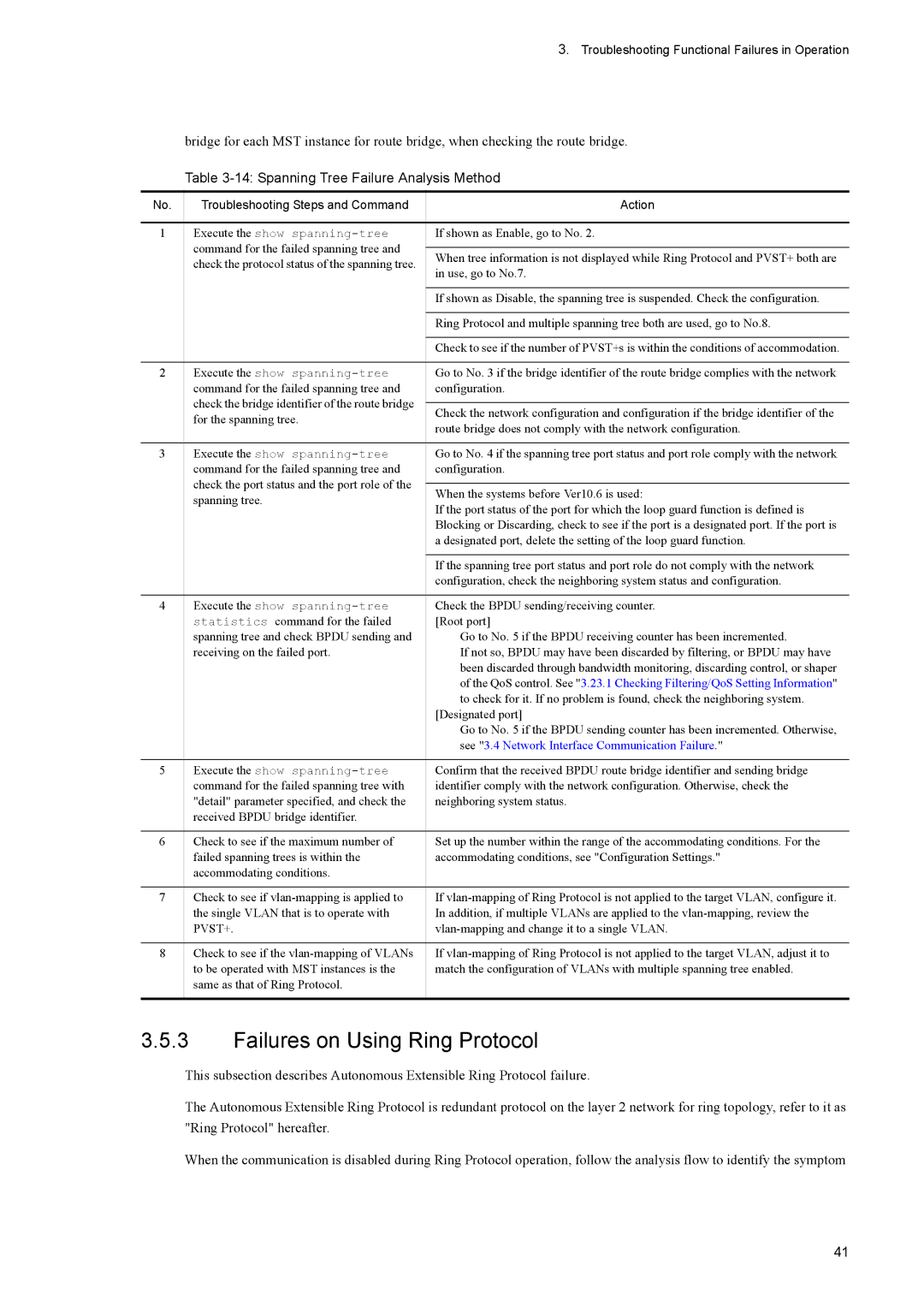
14 Spanning Tree Failure Analysis Method
Failures on Using Ring Protocol
See 3.4 Network Interface Communication Failure
Analysis Flow
Replace the faulty Parts
Troubleshooting Steps Action Command
15 Ring Protocol Failure Analysis Method
Spanning tree or Gsrp is used at Configurations Same time
Command to check timer values for
Transmission delay is not considered
See the manual Configuration Guide
Multicast Relay by Igmp snooping Is Disabled
Multicast in the VLAN. IP8800/S3600
16 Troubleshooting on Multicast Relay
Has been set up appropriately for system operation
Show system command
Group address
If a multicast router is connected, check mrouter-port
Is it a relay within the same VLAN?
Multicast Relay by MLD snooping Is Disabled
Check the following You want to use IPv6 multicast at
17 Troubleshooting on Multicast Relay
Using the show mld-snooping
IPv4 Network Communication Failure
Communication Is Disabled or Is Disconnected
Route
Checking log
Checking interface status
Checking ARP resolution information with neighboring system
Checking option license OP-NPAR OP-NPAR
Checking DHCP/BOOTP setting information
Checking filtering/QoS setting information
Checking unicast routing information
DHCP/BOOTP relay communication failure
IP Addresses Cannot Be Assigned Using Dhcp Function
Checking the log and interface
Checking ARP resolution information with neighboring system
Checking route information
Checking DHCP/BOOTP setting information
Checking filtering/QoS setting information
Dhcp server communication trouble
Checking the log message and interface
Checking configuration
Associated with each log message
Checking layer 2 network
DynamicDNS Cooperation in Dhcp Function Is Disabled
System
DNS update disabled Check the configuration
Checking route information
18 RIP Failure Analysis Method
IPv4 Unicast Routing Communication Failure
No RIP Routing Information Exists
No Ospf Routing Information Exists
21 VRF Failure Analysis Method
No BGP4 Routing Information Exists
No Routing Information Exist OP-NPAR
20 BGP4 Failure Analysis Method
22 Common Check Items
Communication on IPv4 PIM-SM Network Is Disabled
IPv4 Multicast Routing Communication Failure
Common check items
BSR check items
24 Rendezvous Point Router Check Items
Rendezvous point router check items
Last-hop-router check items
23 BSR Check Items
First-hop-router check items
Multicast Data Is Double-relayed on IPv4 PIM-SM Network
26 first-hop-router Check Items
Multicast Sender First-hop-router Last-hop-router Data
Communication on IPv4 PIM-SSM Network Is Disabled
27 Check Items When Double-relay Continues
28 Common Check Items
29 last-hop-router Check Items
30 first-hop-router Check Items
Multicast Data Is Double-relayed on IPv4 PIM-SSM Network
Is Double-relayed on IPv4 PIM-SSM Network
31 Check Items When Double-relay Continues
5 IPv4 Multicast Communication Failure In VRF OP-NPAR
32 Check Items for VRF
IPv6 Network Communication Failure
Checking the log and interface
Checking NDP resolution information with neighboring system
Checking unicast interface information
Checking RA setting information
2 IPv6 Dhcp Troubleshooting
Configuration is not distributed
See the manuals Message Log Reference
Checking the status of the IPv6 Dhcp server in this system
Check the status of IPv6DHCP server
Duplicate acquisition by the client
Procedure to check configuration
Procedure for restoring from duplicate distribution
Checking client setting
Condition Cause Binding Information Route Information
Reproducing the Duid
Reconfiguring route information
If Duid of this system conflicts with other system
Deleting the file containing Duid information
Checking the Duid
35 Failure Analysis of RIPng
10 IPv6 Unicast Routing Communication Failure
No RIPng Routing Information Exists
No OSPFv3 Routing Information Exists
Go to No.5 if no route exist
Hop address resolution in BGP4+ exist Exists
No BGP4+ Routing Information Exists
37 BGP4+ Failure Analysis Method
11 IPv6 Multicast Routing Communication Failure
Communication on IPv6 PIM-SM Network Is Disabled
38 Common Check Items
If the unicast route does not exist, see 3.10 IPv6 Unicast
Neighboring router using the show ipv6 pim
Command with interface parameter specified
Relay target group address Rendezvous point setting
41 last-hop-router Check Items
Multicast receiver Configuration to run MLD
39 BSR Check Items
40 Rendezvous Point Router Check Items
Multicast Data Is Double-relayed on IPv6 PIM-SM Network
43 Check Items When Double-relay Continues
42 first-hop-router Check Items
44 Common Check Items
Communication on IPv6 PIM-SSM Network Is Disabled
To the ports to which neighboring routers connect
45 last-hop-router Check Items
For MLD snooping
Multicast Data Is Double-relayed on IPv6 PIM-SSM Network
46 first-hop-router Check Items
Group join function is running
47 Check Items When Double-relay Continues
Communication Failure on Using Ieee
Layer 2 Authentication Communication Failure
48 Ieee 802.1X Failure Analysis Method
To see if authentication failed
Following cause. Check to see if there is any problem
Table setting failed
Authentication dynamic mode, go to No
Tunnel-Type for the Radius server to VLAN13
Command and check to see if dynamic
Assignment of Vlan authentication
Authentication dynamic. Match the Vlan ID set for
50 Failure Analysis Method for Web Authentication
Communication Failure on Using Web Authentication
Port for authentication
Check to see authentication Ipv4 access list
Confirm that authentication IPv4 access list is applied
IPv4 access list are set in the access list as well
Restarted. The Web server starts to perform authentication
Authenticated
Command Soon After Suspended
When Web Server Is restarted Using
Check Point Troubleshooting Steps
51 Checking Web Authentication Configuration
Setting Information
Failure Analysis Method for Web Authentication
52 Web Authentication Failure Analysis Method
53 Failure Analysis Method for MAC Authentication
Communication Failure on Using MAC Authentication
Configuration command mac-authentication port
IPv4 access list is applied
Not applied to the port for authentication
Authentication is displayed by the show To No.7
Failure Analysis Method for MAC Authentication
Communication Failure on Using Authentication Vlan OP-VAA
54 Checking MAC Authentication Configuration
55 MAC Authentication Failure Analysis Method
100
56 Authentication Vlan Failure Analysis Method
When Vlan Identification Table Resource Shortage Occurs
57 Checking Authentication Vlan Configuration
101
102
Gsrp Communication Failures
Communication Failure on High-reliability Function
104
60 Analysis Method for Gsrp Unknown Adjacency
105
61 Vrrp Failure Analysis Method
106
107
62 Vrrp Failure Analysis Method
108
109
Set up, and the virtual router may operate. IP8800/S3600
MIBs Cannot Be Obtained from Snmp Manager
Snmp Communication Failure
Traps Cannot Be Received by Snmp Manager
111
Checking route to the collector
Checking operation status by operation command
Checking configuration Checking failures etc
SFlow Packets Do Not Reach Collector
Collector information must be set correctly
Checking configuration
Checking NIF/port status
Checking settings of collector
114
Checking transmission interval of counter sample
Flow Sample Does Not Reach Collector
Counter Sample Does Not Reach Collector
Checking presence/absence of the relay packet
64 Failure Analysis When Using Oadp Function
63 Failure Analysis Method When Using Lldp Functions
Network Interface Communication Failure
Otherwise, see 3.5 Layer 2 Network Communication Failure
Checking Filtering/QoS Setting Information to check for it
117
Otherwise, see 3.4 Network Interface Communication Failure
NTP Communication Failure
Time Synchronization by NTP Is Disabled
65 NTP Failure Analysis Method
Port Becomes Inactive Due to IEEE802.3ah/UDLD Function
Communication Failure on IEEE802.3ah/UDLD Function
67 Problems and Actions When Switching Active System
Active System Switchover Is Disabled
Cause for Switchover Disabled Troubleshooting Steps
68 Failure Analysis Method When BSU Switchover Disabled
Active BSU Switchover Is Disabled
Boards
122
Display of Result Confirmation Cause Action
Problems on Power Saving Feature
Set to disabled, delete the entry that is
Schedule error caused by
Neighboring system in 3.9.1 Communication Is Disabled or Is
Neighboring system in 3.6.1 Communication Is Disabled or Is
Disconnected
125
Checking Filtering/QoS Setting Information
Communication Failure Caused by Settings of Filtering/QoS
Checking packet discarding by filtering
127
IP8800/S3600 and IP8800/S2400
Page
129
IP8800/S6700 IP8800/S6600 IP8800/S6300
Operation Log Message for Checking Resource Use Status
MAC Address Table Resource Shortage
Checking Resource Usage of MAC Address Table
Operation Log Message for Checking Resource Usage
File Name Specified for get Log Message
131
132
Checking Vlan Identification Table Resource Usage
Tag translation function
Vlan setting.*1
Vlan Identification Table Entry Clear Method
Entry to Be Cleared Step
Checking Resource Usage of Shared Memory
When Resource Shortage Occurs in Shared Memory
Page
137
Collecting Failure Information
File Name Specified for get Acquiring Basic Information
Collecting Failure Information
Available Information via ftp
Collecting Failure Information
139
Collecting basic information
Collecting memory dump when communication failure occurs
Collecting Failure Information Using dump Command IP8800
140
141
After above log is displayed, execute next the dump command
142
143
Maintenance Information
Transferring Files for Maintenance Information
Storage Location and File Name File Transfer
Transferring dump files to the remote operation terminal
Transferring Files Using ftp Command
145
146
147
ETA
148
Transferring failure backup information files to a console
Transferring dump files to a console
Transferring log information to a console
149
IP8800/S6700 IP8800/S6600 IP8800/S6300
150
Files That Can Be Acquired Using ftp Command
File Name Specified for Acquired Files
151
10 Collecting Dump Files from the Remote Terminal
Writing to MC
Writing File to MC Using Operation Terminal
153
Line Test
Line Test Type for Each Frame Loopback Point
Testing Line
Ethernet Port
Checking frame loopback within system
155
Command IP8800/S6700 IP8800/S6600 IP8800/S6300
156
Checking frame loopback at a loop connector
157
Page
159
Restarting the System
Restarting the System
Restarting the System
Parameter to input Active Standby None
161
Set the system to restart Or stop
Specifying when
162
163
Collecting memory
Dump Back to command input mode
164
Collect Memory dump? Memorydump is Restart?
165
Appendix
Appendix a Contents of show tech-support Command Display
167
168
169
170
171
172
173
IP8800/S3600
Table A-2 Details of Display Contents IP8800/S3600
174
175
Information 2 for Ver.10.7 Earlier
Update for Ver.11.1 and later
176
Log information during software
177
178
179
180
IP8800/S2400
Table A-3 Details of Display Contents IP8800/S2400
181
182
Information on L2 loop detection For Ver.10.7 and later
183
MLD snooping group information
Built-in WEB authentication DB For Ver.10.3 and later
Authenticated user account
184
185
Page
187
Index
Index
188