CPE SIP Products
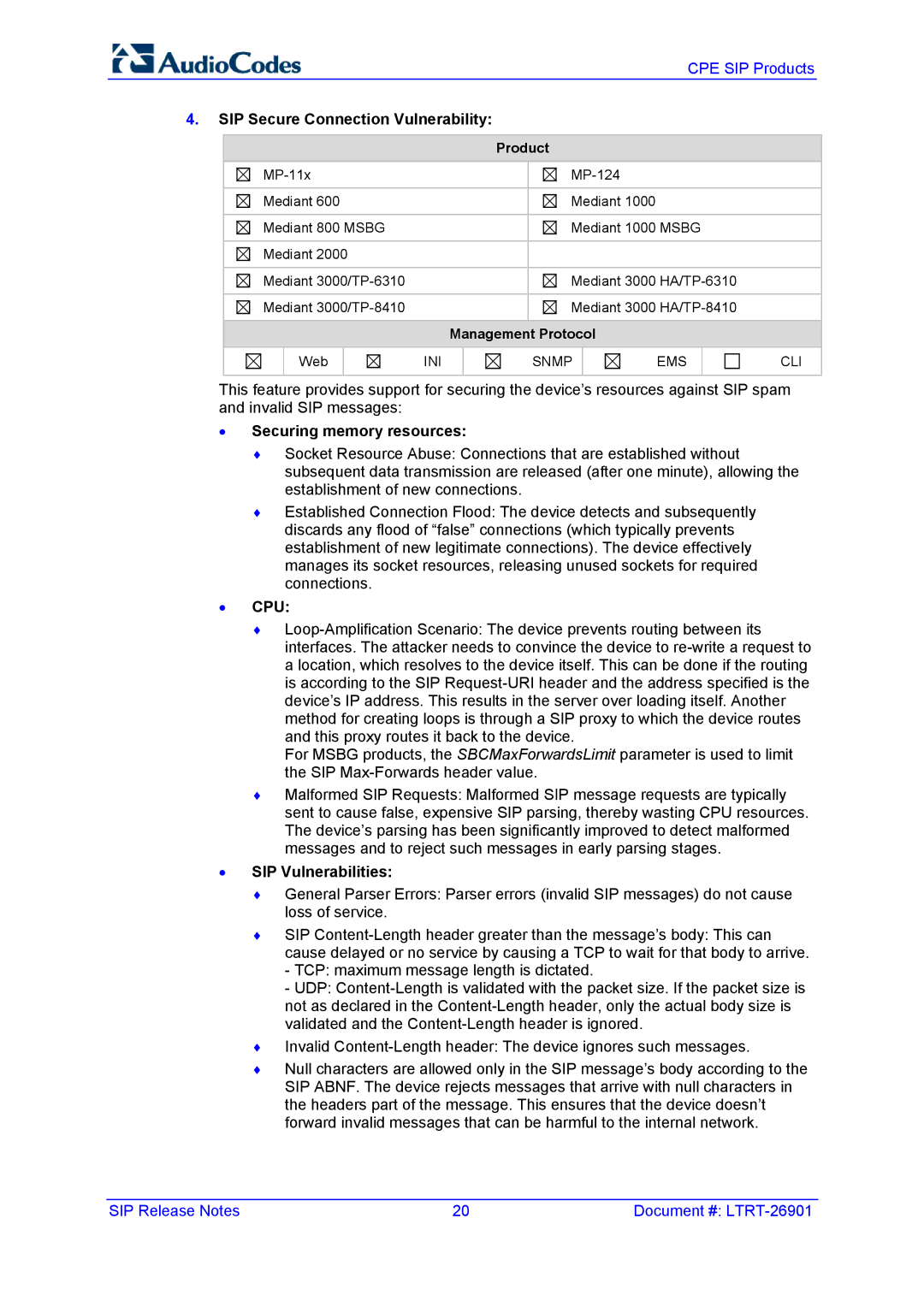
4.SIP Secure Connection Vulnerability:
| Product | |
| ||
|
|
|
Mediant 600 |
| Mediant 1000 |
|
|
|
Mediant 800 MSBG |
| Mediant 1000 MSBG |
|
|
|
Mediant 2000 |
|
|
|
|
|
Mediant |
| Mediant 3000 |
|
|
|
Mediant |
| Mediant 3000 |
|
|
|
| Management Protocol | |
|
|
|
Web
INI
SNMP
EMS
CLI
This feature provides support for securing the device’s resources against SIP spam and invalid SIP messages:
•Securing memory resources:
♦Socket Resource Abuse: Connections that are established without subsequent data transmission are released (after one minute), allowing the establishment of new connections.
♦Established Connection Flood: The device detects and subsequently discards any flood of “false” connections (which typically prevents establishment of new legitimate connections). The device effectively manages its socket resources, releasing unused sockets for required connections.
•CPU:
♦
For MSBG products, the SBCMaxForwardsLimit parameter is used to limit the SIP
♦Malformed SIP Requests: Malformed SIP message requests are typically sent to cause false, expensive SIP parsing, thereby wasting CPU resources. The device’s parsing has been significantly improved to detect malformed messages and to reject such messages in early parsing stages.
•SIP Vulnerabilities:
♦General Parser Errors: Parser errors (invalid SIP messages) do not cause loss of service.
♦SIP
-TCP: maximum message length is dictated.
-UDP:
♦Invalid
♦Null characters are allowed only in the SIP message’s body according to the SIP ABNF. The device rejects messages that arrive with null characters in the headers part of the message. This ensures that the device doesn’t forward invalid messages that can be harmful to the internal network.
SIP Release Notes | 20 | Document #: |