DGS-3024 Gigabit Ethernet Switch Manual
SSH Algorithm
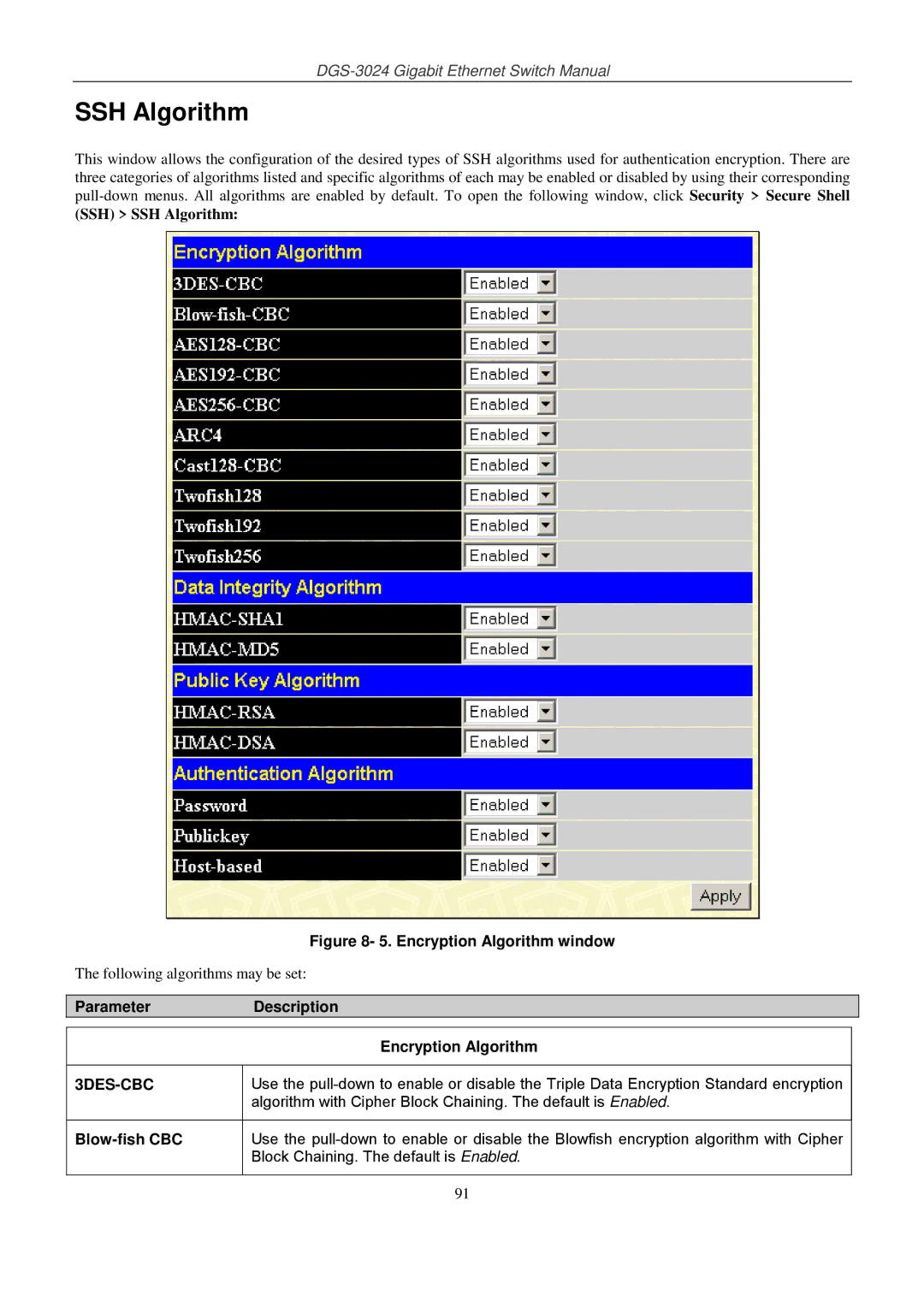
This window allows the configuration of the desired types of SSH algorithms used for authentication encryption. There are three categories of algorithms listed and specific algorithms of each may be enabled or disabled by using their corresponding
Figure 8- 5. Encryption Algorithm window
The following algorithms may be set:
ParameterDescription
| Encryption Algorithm |
|
|
| Use the |
| algorithm with Cipher Block Chaining. The default is Enabled. |
|
|
| Use the |
| Block Chaining. The default is Enabled. |
|
|
91