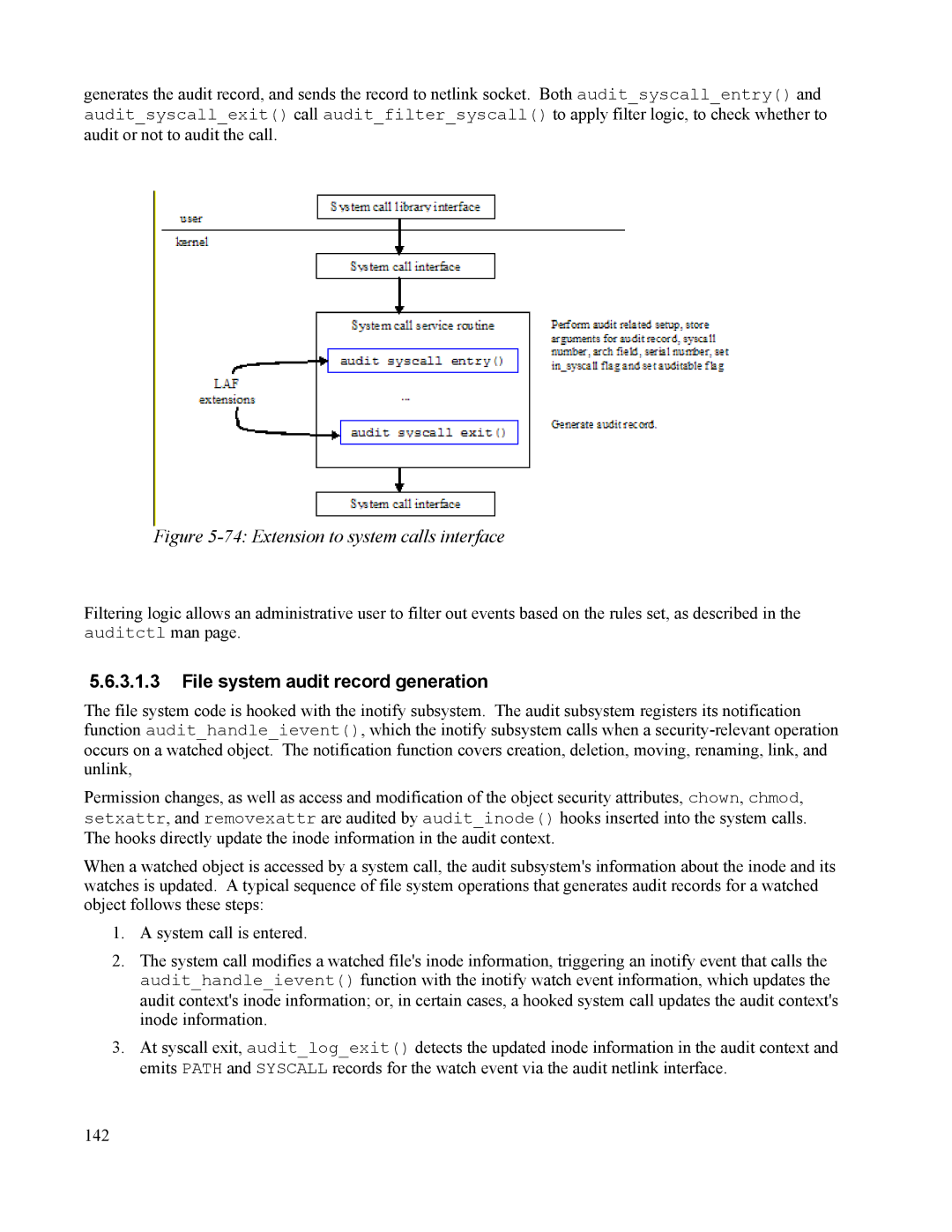
generates the audit record, and sends the record to netlink socket. Both audit_syscall_entry() and
audit_syscall_exit() call audit_filter_syscall() to apply filter logic, to check whether to
audit or not to audit the call.
Figure 5-74: Extension to system calls interface
Filtering logic allows an administrative user to filter out events based on the rules set, as described in the auditctl man page.
5.6.3.1.3File system audit record generation
The file system code is hooked with the inotify subsystem. The audit subsystem registers its notification function audit_handle_ievent(), which the inotify subsystem calls when a
Permission changes, as well as access and modification of the object security attributes, chown, chmod, setxattr, and removexattr are audited by audit_inode() hooks inserted into the system calls. The hooks directly update the inode information in the audit context.
When a watched object is accessed by a system call, the audit subsystem's information about the inode and its watches is updated. A typical sequence of file system operations that generates audit records for a watched object follows these steps:
1.A system call is entered.
2.The system call modifies a watched file's inode information, triggering an inotify event that calls the audit_handle_ievent() function with the inotify watch event information, which updates the audit context's inode information; or, in certain cases, a hooked system call updates the audit context's inode information.
3.At syscall exit, audit_log_exit() detects the updated inode information in the audit context and emits PATH and SYSCALL records for the watch event via the audit netlink interface.