•Requestor Privilege Level (RPL):RPL represents the privilege level of the program that created the segment selector. The RPL is stored in the segment selector used to reference the segment descriptor.
•Descriptor Privilege Level (DPL):DPL is the privilege level that is associated with an individual segment. The system software assigns this DPL, and it is stored in the segment descriptor.
CPL, RPL, and DPL are used to implement access control on data accesses and control transfers as follows.
5.5.2.5.5.1Access control for data access
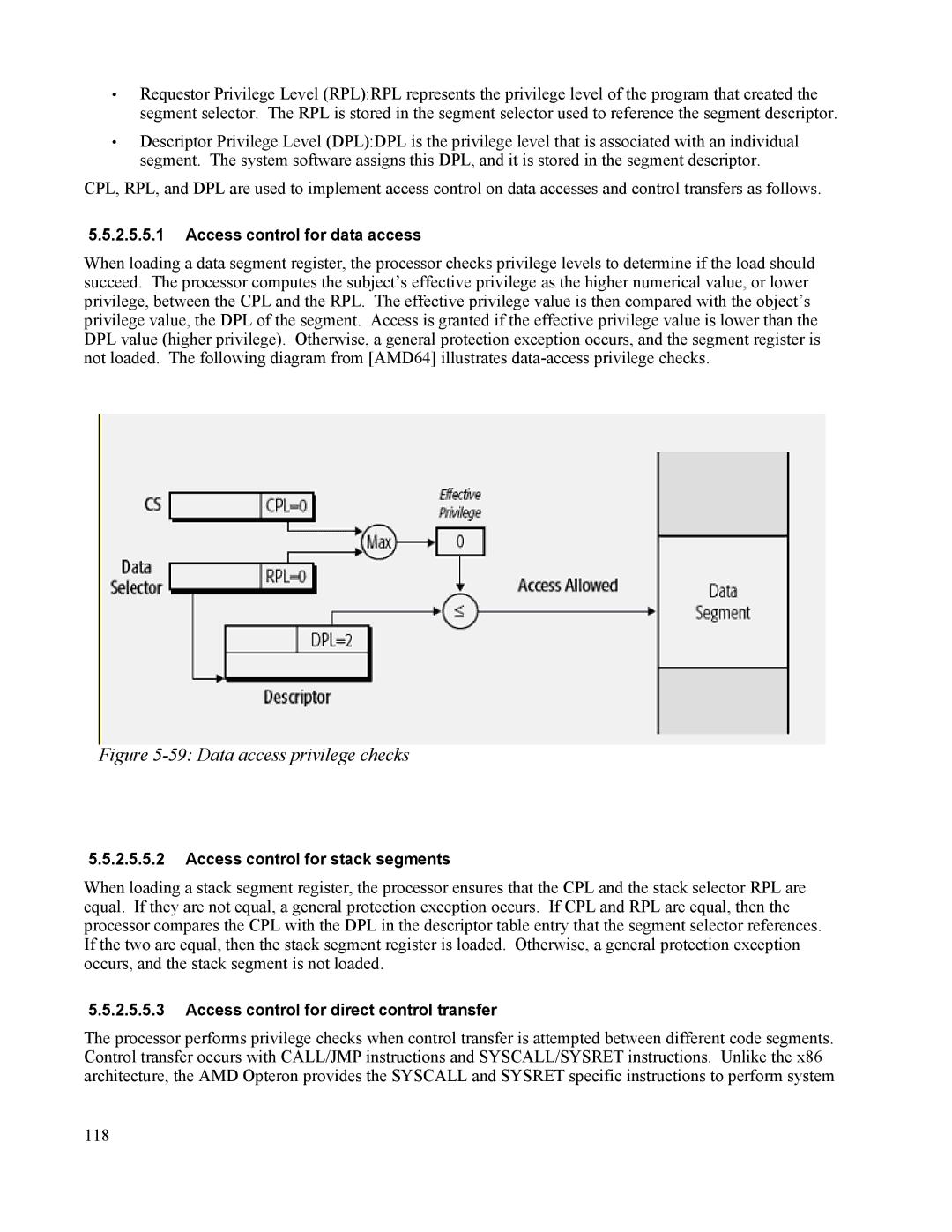
When loading a data segment register, the processor checks privilege levels to determine if the load should succeed. The processor computes the subject’s effective privilege as the higher numerical value, or lower privilege, between the CPL and the RPL. The effective privilege value is then compared with the object’s privilege value, the DPL of the segment. Access is granted if the effective privilege value is lower than the DPL value (higher privilege). Otherwise, a general protection exception occurs, and the segment register is not loaded. The following diagram from [AMD64] illustrates
Figure 5-59: Data access privilege checks
5.5.2.5.5.2Access control for stack segments
When loading a stack segment register, the processor ensures that the CPL and the stack selector RPL are equal. If they are not equal, a general protection exception occurs. If CPL and RPL are equal, then the processor compares the CPL with the DPL in the descriptor table entry that the segment selector references. If the two are equal, then the stack segment register is loaded. Otherwise, a general protection exception occurs, and the stack segment is not loaded.
5.5.2.5.5.3Access control for direct control transfer
The processor performs privilege checks when control transfer is attempted between different code segments. Control transfer occurs with CALL/JMP instructions and SYSCALL/SYSRET instructions. Unlike the x86 architecture, the AMD Opteron provides the SYSCALL and SYSRET specific instructions to perform system
118