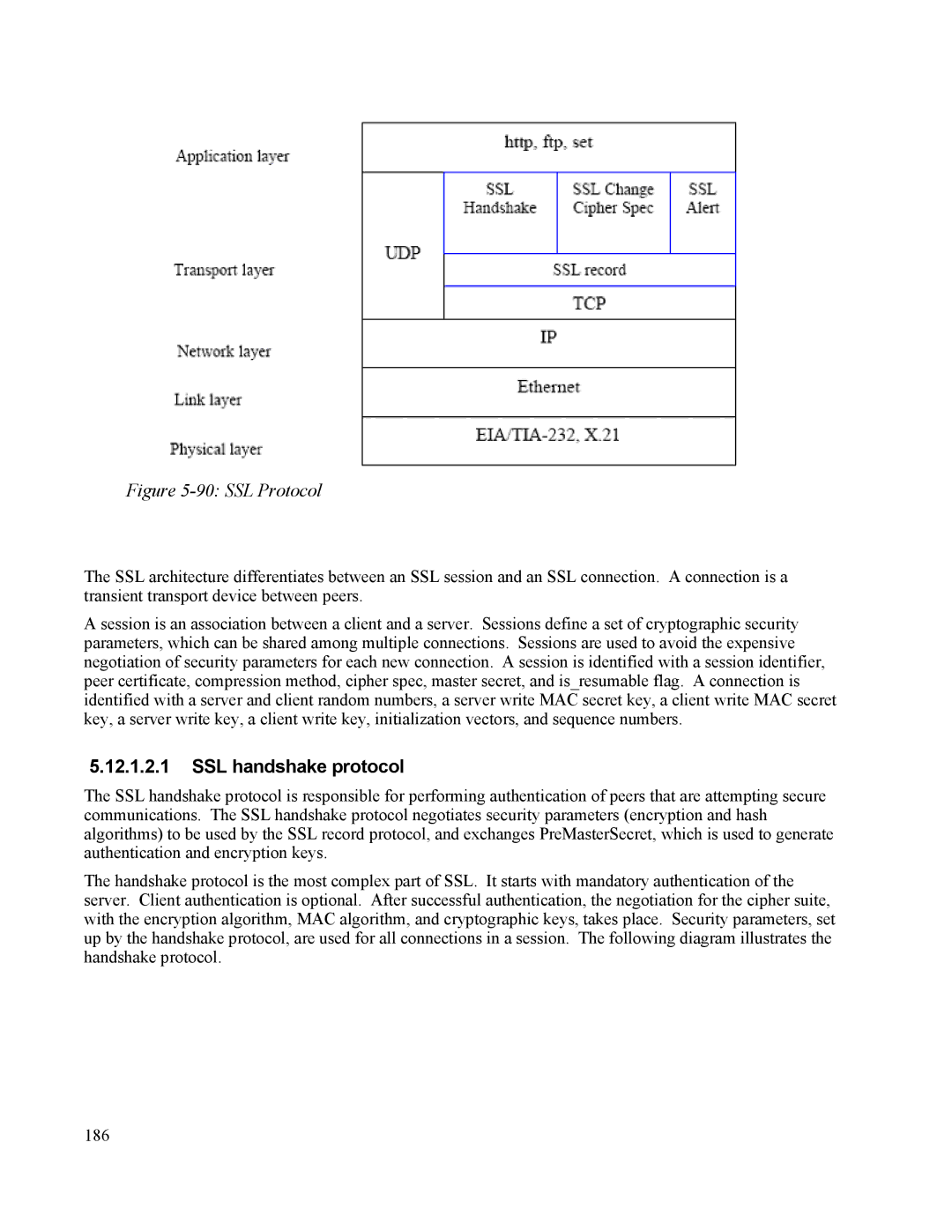
Figure 5-90: SSL Protocol
The SSL architecture differentiates between an SSL session and an SSL connection. A connection is a transient transport device between peers.
A session is an association between a client and a server. Sessions define a set of cryptographic security parameters, which can be shared among multiple connections. Sessions are used to avoid the expensive negotiation of security parameters for each new connection. A session is identified with a session identifier, peer certificate, compression method, cipher spec, master secret, and is_resumable flag. A connection is identified with a server and client random numbers, a server write MAC secret key, a client write MAC secret key, a server write key, a client write key, initialization vectors, and sequence numbers.
5.12.1.2.1SSL handshake protocol
The SSL handshake protocol is responsible for performing authentication of peers that are attempting secure communications. The SSL handshake protocol negotiates security parameters (encryption and hash algorithms) to be used by the SSL record protocol, and exchanges PreMasterSecret, which is used to generate authentication and encryption keys.
The handshake protocol is the most complex part of SSL. It starts with mandatory authentication of the server. Client authentication is optional. After successful authentication, the negotiation for the cipher suite, with the encryption algorithm, MAC algorithm, and cryptographic keys, takes place. Security parameters, set up by the handshake protocol, are used for all connections in a session. The following diagram illustrates the handshake protocol.
186