Cryptography can be used to neutralize some of these attacks and to ensure confidentiality and integrity of network traffic. Cryptography can also be used to implement authentication schemes using digital signatures. The TOE supports a technology based on cryptography called OpenSSL.
OpenSSL is a cryptography toolkit implementing the Secure Sockets Layer (SSL) versions 2 and 3, and Transport Layer Security (TLS) version 1 network protocols and related cryptography standards required by them.
SSL, which is
•Open SSL Web site at http://www.openssl.org/docs.
•IBM Redbook TCP/IP Tutorial and Technical Overview, by Adolfo Rodriguez, et al. at http://www.redbooks.ibm.com/redbooks/pdfs/gg243376.pdf.
•“The TLS Protocol version 1.1” by Tim Dierks and Eric Rescorla at http://www.ietf.org/rfc/rfc2246.txt?number=2246.
•Internet Security Protocols: SSLeay & TLS, by Eric Young.
•Cryptography and Network Security Principles and Practice, 2nd Edition, by William Stallings.
SSL was originally designed by Netscape. SSL version 3 was designed with public input. As SSL gained in popularity, a Transport Layer Security (TLS) working group was formed to submit the protocol for Internet standardization. OpenSSL implements Secure Socket Layer (SSL versions 2 and 3) and Transport Layer Security (TLS version 1) protocols, as well as a
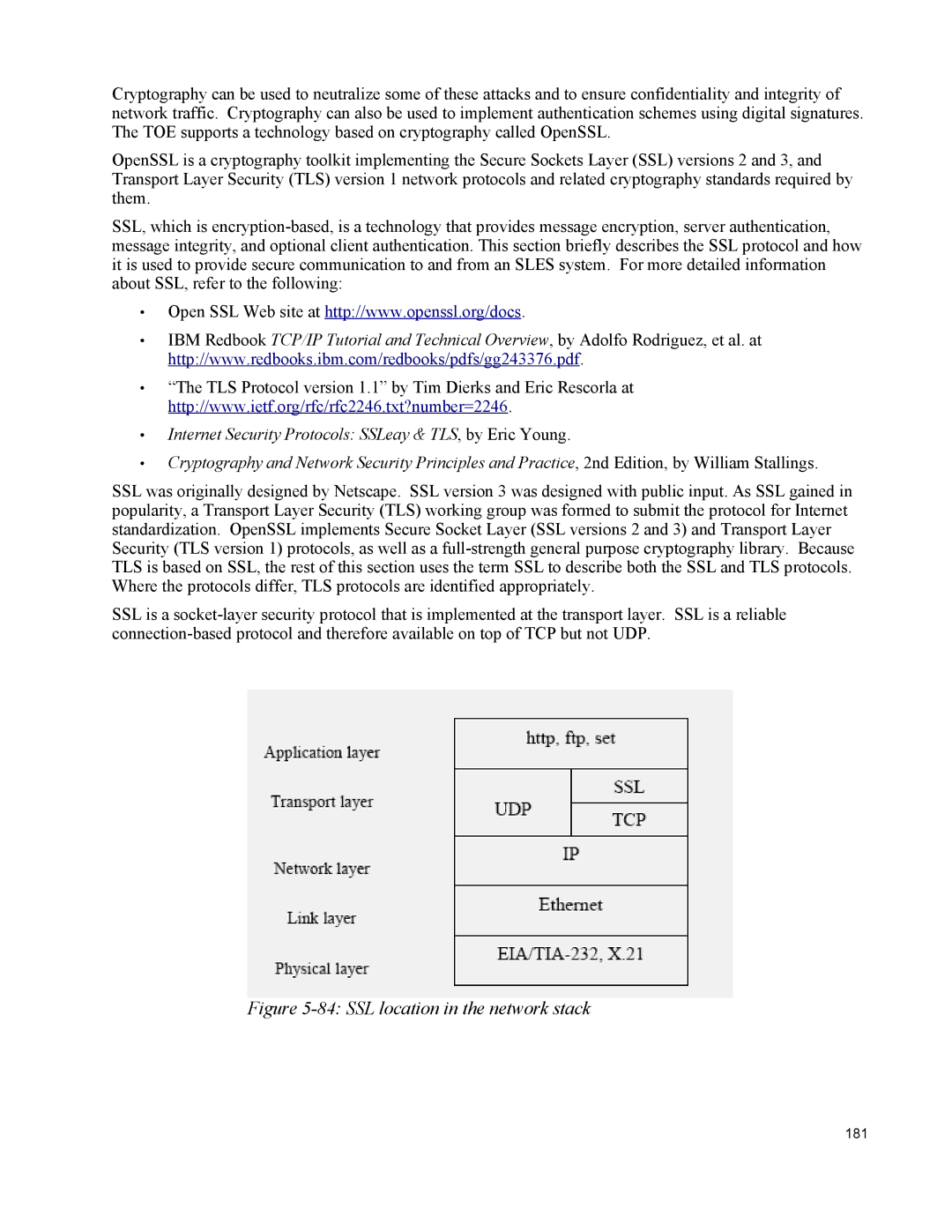
SSL is a
Figure 5-84: SSL location in the network stack
181