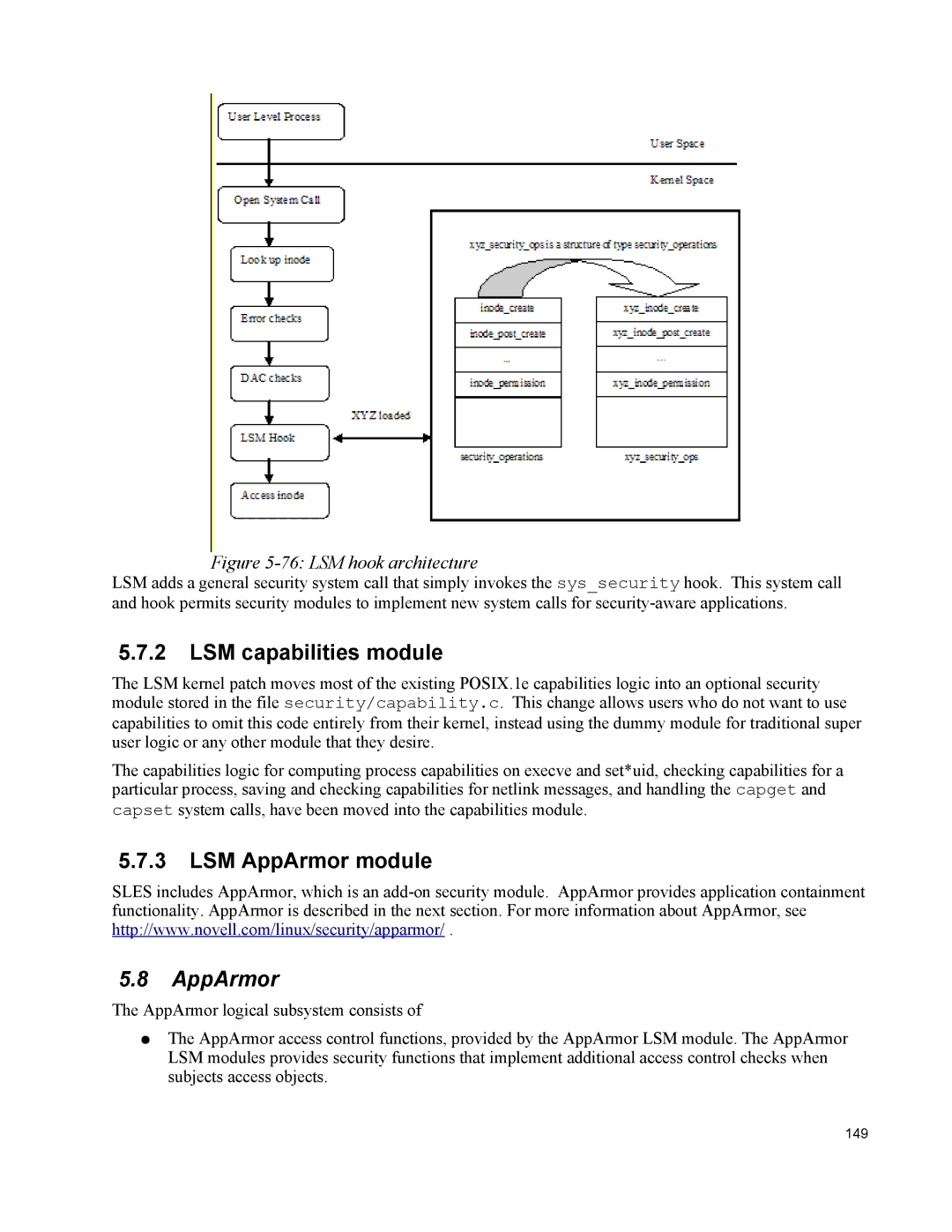
Figure 5-76: LSM hook architecture
LSM adds a general security system call that simply invokes the sys_security hook. This system call and hook permits security modules to implement new system calls for
5.7.2LSM capabilities module
The LSM kernel patch moves most of the existing POSIX.1e capabilities logic into an optional security module stored in the file security/capability.c. This change allows users who do not want to use capabilities to omit this code entirely from their kernel, instead using the dummy module for traditional super user logic or any other module that they desire.
The capabilities logic for computing process capabilities on execve and set*uid, checking capabilities for a particular process, saving and checking capabilities for netlink messages, and handling the capget and capset system calls, have been moved into the capabilities module.
5.7.3LSM AppArmor module
SLES includes AppArmor, which is an
5.8AppArmor
The AppArmor logical subsystem consists of
●The AppArmor access control functions, provided by the AppArmor LSM module. The AppArmor LSM modules provides security functions that implement additional access control checks when subjects access objects.
149