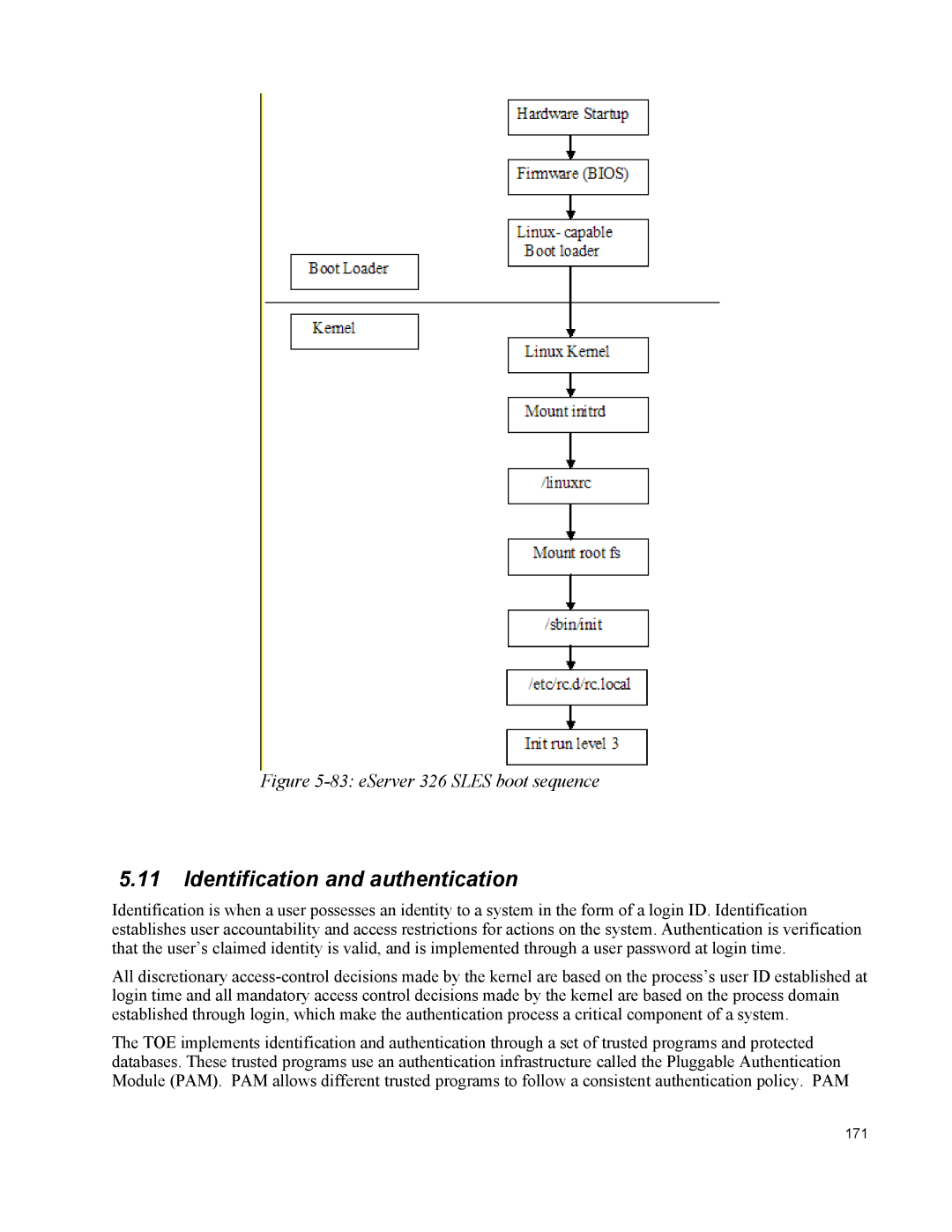
Figure 5-83: eServer 326 SLES boot sequence
5.11Identification and authentication
Identification is when a user possesses an identity to a system in the form of a login ID. Identification establishes user accountability and access restrictions for actions on the system. Authentication is verification that the user’s claimed identity is valid, and is implemented through a user password at login time.
All discretionary
The TOE implements identification and authentication through a set of trusted programs and protected databases. These trusted programs use an authentication infrastructure called the Pluggable Authentication Module (PAM). PAM allows different trusted programs to follow a consistent authentication policy. PAM
171